Overview (and a disclaimer)
 This conversation aims to identify opportunities to incorporate security controls into each phase of the DevSecOps methodology throughout the IoT device product development life cycle. Before proceeding, we should note two minor disclaimers:
This conversation aims to identify opportunities to incorporate security controls into each phase of the DevSecOps methodology throughout the IoT device product development life cycle. Before proceeding, we should note two minor disclaimers:
- This post is not meant to define in any way how DevSecOps can or should be implemented for software-only applications.
- There is a substantial difference between producers and consumers of IoT devices. How to ensure consumers are securely leveraging IoT devices is an important topic that warrants a blog post on its own. This blog post doesn’t cover that, but thankfully, our team has produced a few:
Current state
 Historically, these types of IoT devices have been designed following a methodology closer to waterfall, where things were done linearly, and continuous improvements/updates were not as prevalent. The cheap and simple nature of IoT devices might appear to lend itself to this approach however with the emergence of IoT-based security attacks, continuous iterations have never been so vital. As a matter of fact, “lack of secure update mechanism” is listed as the fourth entry in the 2018 OWASP IoT Top 10. Furthermore, it is estimated that by 2030, the number of active IoT devices will surpass 25.4 billion, which emphasizes the urgency for security risks to be quickly identified and remediated. quickly identified and remediated.
Historically, these types of IoT devices have been designed following a methodology closer to waterfall, where things were done linearly, and continuous improvements/updates were not as prevalent. The cheap and simple nature of IoT devices might appear to lend itself to this approach however with the emergence of IoT-based security attacks, continuous iterations have never been so vital. As a matter of fact, “lack of secure update mechanism” is listed as the fourth entry in the 2018 OWASP IoT Top 10. Furthermore, it is estimated that by 2030, the number of active IoT devices will surpass 25.4 billion, which emphasizes the urgency for security risks to be quickly identified and remediated. quickly identified and remediated.
Emphasize IoT security throughout the Dev phases
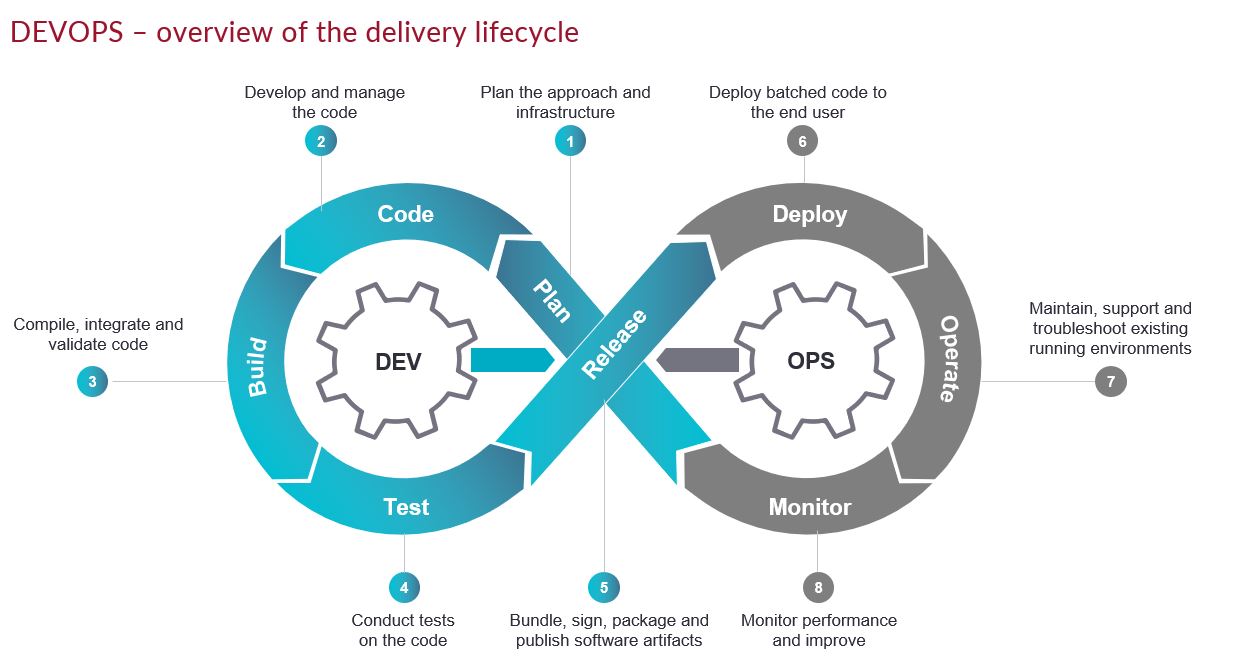
Development
Plan
Modern development methodologies have placed an emphasis on continuous feedback which can stem from a variety of sources such as user feedback, threat remediation, or overall feature improvements. Companies should continuously adapt to industry needs by employing a robust planning methodology. Regarding product security, organizations should seek to integrate secure planning steps into the DevSecOps planning process. Whether it be the output from activities such as threat modeling or establishing organizational policies for security-focused requirements/user stories. Note that any tools mentioned here are simply suggestions. Each organization should determine which may be appropriate to fulfill the DevSecOps strategy.

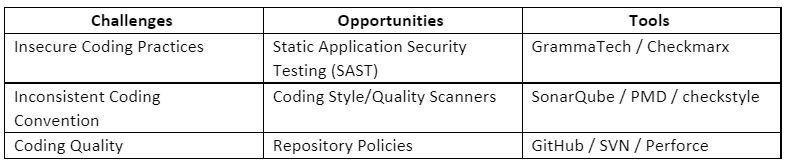
Code
The coding phase arguably requires the highest level of scrutiny in the DevSecOps methodology. Developers should constantly be trained on secure coding practices while simultaneously implementing a variety of tools to aid in identifying vulnerabilities early and often. It is imperative that organizations create a baseline for development strategies such as branching, pre-commit rules, and style guides. It is worth mentioning that opportunities for improving secure coding can also aid in improving the quality and consistency of code being developed.
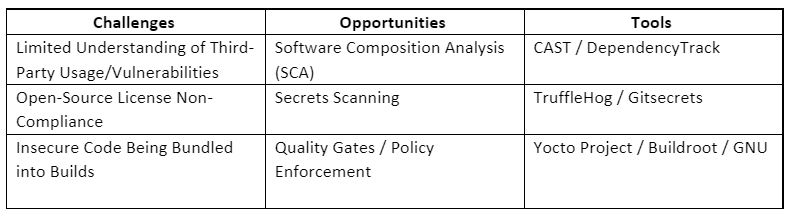
Build
Once code is committed to a shared repository, a variety of quick functional unit tests are often performed. Integrating security into this step allows developers to analyze the source code from a Software Composition Analysis (SCA) perspective. Often developers tend to leverage third-party libraries solely on their functional benefit without considering the potential security implications. Developers that understand dependencies as they are being introduced into a project can be more aware of the potential security risks as well as license violations that impact the organization.
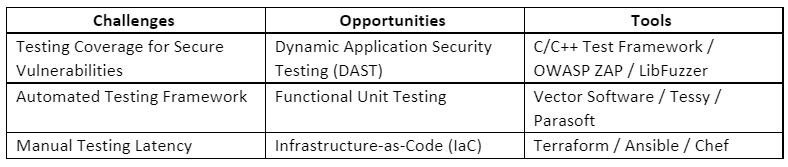
Test
Historically regression testing has been a tedious manual process that requires manual interaction to confirm baseline functionality. With the growing popularity of Infrastructure-as-Code (IaC) solutions, extensive acceptance/validation testing can be performed in parallel with Dynamic Application Security Testing (DAST). In addition to the extensive unit test cases that will likely be performed on an application, organizations should be diligent about creating security-focused unit test cases that aim to identify low-level security vulnerabilities that might have been introduced. Note that unit testing IoT devices is not a trivial task and ample time should be allocated to ensure these test cases can be designed and implemented properly.
Operations
As stated previously, there is a substantial difference between the producer and consumer of IoT devices. Dealing with the operation of IoT devices being leveraged on an organization’s network can be solved with a myriad of tools outlined in the aforementioned blog posts. Producers of IoT devices have an entirely different set of problems to solve. Luckily, in most cases, the solutions can be turnkey. To better understand the need during this stage of DevSecOps it is helpful to have a fundamental grasp on the Ops phases.
Release
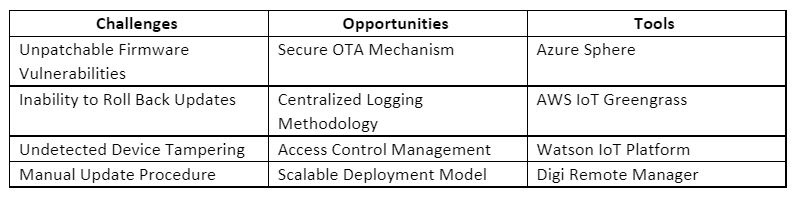
This phase is the transition where development becomes operations. Organizations should ensure that a robust device management system has been put in place to ensure releases can be staged for remote systems. The IBM Watson IoT platform supports multiple security features to improve the security controls in the release phase.
Deploy
An automated deployment methodology aids in eliminating potential security and functional issues introduced when manually deploying updates to remote systems and allows you to manage deployed releases based on tags among other factors. AWS IoT Greengrass supports secure deployment from cloud-to-chip by leveraging their Device Certificate Manager (DCM) to manage device certificates and identities.
Operate
Ensuring the proper operation of remote devices can be achieved by leveraging device management systems to process runtime device data, including firmware update status, operating conditions, errors, etc. The Microsoft Azure Sphere Team released a white paper on The Seven Properties of Highly Secured Devices and listed error reporting for edge devices as one of the seven properties.
Monitor
Manufacturers should utilize the secure device management solution to ensure rogue systems are detected and addressed by implementing a centralized logging system where devices report security events. Digi Remote Manager leverages Digi TrustFence to enable device monitoring, security, privacy, and identity.
Hopefully, the solution is clear. Any organization that is producing and deploying IoT devices should ensure that a robust device management system has been established to handle various aspects of operations. To a manufacturer’s benefit, there are a variety of solutions that address each phase of Ops detailed above in some capacity and can be leveraged with minimal effort as opposed to creating a secure solution from scratch. If a custom device management system must be created, the same security controls outlined above also apply and even more should be considered to properly ensure secure operations. There are also a variety of different DevSecOps tools to consider when implementing a DevSecOps solution on a software application.
Where to begin
Without a proper understanding of an organization’s entire DevOps pipeline, it is difficult to prioritize steps to improve the overall security posture of the process. Multiple maturity models exist that can provide insight into various gaps in existing in the DevOps process. A maturity model assessment is a review process where Protiviti consultants will work alongside development teams to understand various aspects of the current DevOps/DevSecOps solution. The objective of this type of assessment is to sample the various steps of the product development life cycle and identify security gaps throughout each phase. With a firm understanding of security issues throughout an organization’s development/operations methodology, a robust plan can be made to incrementally introduce security controls aiming to achieve a predetermined maturity level.
The output from this assessment identifies gaps that demonstrate follow-up work that should be completed to ensure development teams are following industry best practices regarding their DevSecOps solution, and therefore must be considered as a first step to implementing an overall secure software development strategy.
IoT has many challenges including managing and maintaining endpoints, electronic devices, deployments, connectivity, data, applications and more; creating multidisciplinary teams with expertise and alignment in engineering, applications, data analysis/management, security, infrastructure, and user experience (UX), all working in a way that is aligned with business goals. DevSecOps integrates security into every phase of the DevOps software development life cycle and can be adapted to IoT to bridge the gap between developers and security professionals throughout every stage of the development process to enable organizations to build code faster, more securely and more efficiently.
To learn more about our IoT services, contact us.



