Oracle ERP Cloud roles are known to be riddled with segregation-of-duties (SoD) risks and excessive sensitive access rights. To meet auditor and compliance requirements while ensuring a secure application environment, many organizations are required to develop custom roles that are SoD risk-free and more appropriately tailored to business requirements.
Oracle security teams may face any number of typical implementation challenges while building custom roles, and most experienced teams are painfully aware of the challenges that come with migrating non-human capital management (HCM) roles from one environment to another.
Until release 19A, security teams could not migrate non-HCM roles at all. Rather, they were forced to manually rebuild roles from the ground up in each environment. With release 19A, Oracle introduced a new feature that allowed security teams to export and import role hierarchies – but not data security policies. When this export/import feature is leveraged, security teams are still required to spend a significant amount of effort manually reconfiguring data security policies for all job and duty roles after each migration. This has been referred to and reported as an Oracle bug (#29337499); however, Oracle has classified this as an enhancement. (For a better understanding of this role migration functionality, refer to our previous blog post on migrating security in Oracle ERP Cloud).
Fortunately, Protiviti has identified an alternate approach that allows for complete migration of custom roles – including data security policies – for Oracle ERP Cloud. In fact, this approach has already been communicated by Oracle for migrating HCM roles. After attending an Oracle HCM security webinar, we quickly realized that the specified technique would likely work for Oracle ERP Cloud roles. Oracle has not announced or released any documentation regarding this approach for non-HCM roles (despite the negative feedback regarding lack of data security policy migration); however, Protiviti has tested and successfully leveraged this technique for migrating custom Oracle ERP Cloud roles between environments.
Custom Role Migration, Including Data Security Policies
Security teams can migrate job roles by leveraging the Manage Implementation Project and Manage Configuration Package functionalities within the Setup and Maintenance area. The configuration package should be made up of the Manage Job Roles and Manage Data Security Policies tasks. Once the scope of roles is selected, a package containing the required role hierarchy and data security policy data can be downloaded and then uploaded into a target instance. (Note that this is a different approach than most experienced security teams would have previously used and does not require use of the export/import functionality from the Manage Job Roles area.)
By leveraging this alternate approach, organizations can successfully migrate custom roles and their accompanying data security policies. This will save a significant number of manual hours performing data entry and will also reduce the risk of inaccurate role configurations due to human error.
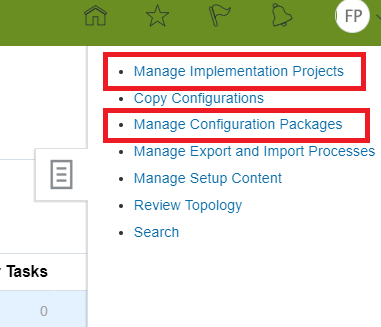
Navigation: Setup and Maintenance > Task Pane > Manage Implementation Project and Manage Configuration Packages
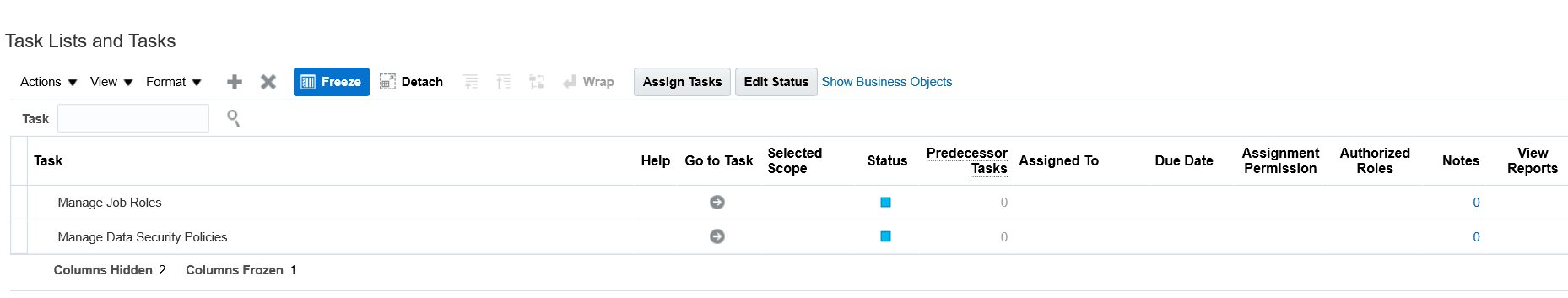
In the implementation project, select Manage Job Roles and Manage Data Security Policies. In the corresponding configuration package, include relevant roles in the scope.
Items to Note
- This functionality is available out-of-the-box with Oracle ERP Cloud.
- This functionality should be independently tested and validated based on the organization’s change management policies.
- Using this feature does not require any prerequisite setups.
- The Application Implementation Consultant and IT Security Manager roles are required to implement this approach.
- The user can migrate all custom roles or select only specific roles using the scope feature.
What Can’t be Migrated?
Using this approach, the efficiency of migrating roles can be dramatically increased; however, there are some limitations around what can be migrated. Some examples include:
- Duty Roles: This approach can be leveraged to migrate only job roles and not duty roles. If individual duty role(s) need to be migrated, a dummy job role may be leveraged to migrate the duty role(s).
- Seeded Roles: The scope feature allows the selection of only custom job roles and not out-of-the-box job roles. In any case, it is best practice to never modify seeded security artifacts, so there should not be a requirement to migrate changes to these roles.
- User Role Mapping: This specific feature does not support migration of user role assignments. Fortunately for teams going through a security design or redesign, the HCM data loader tool can be leveraged for this time-consuming task.
Conclusion
Oracle cloud security teams that have experienced the time-consuming, tedious nature of custom role migration will be thrilled to hear that the migration process can now be fully automated. By eliminating the need to manually reconfigure data security policies after each migration, this approach has been proven to significantly reduce the level of effort required to migrate custom roles from one environment to another and allows organizations and security professionals to feel the benefits.
To learn more about how Protiviti can help with Oracle security, please visit our Oracle Solutions site or contact us.





