For all of its advantages, Software as a Service (SaaS) has introduced licensing considerations that were nonexistent with on-premises enterprise software. The structures of SaaS licenses and security models require more deliberation during initial design, but also recurring review while in operation. While this post focuses primarily on Oracle Fusion Cloud licensing – given intricacies that may inadvertently result in unexpected or unbudgeted costs – the same considerations likely pertain to other cloud software utilized throughout an organization.
The Oracle Fusion Cloud security model
Oracle Fusion Cloud’s licensing model is largely based on access assigned to users via job roles. At a 30,000 foot view, the security architecture can be broken down into the following hierarchical levels:
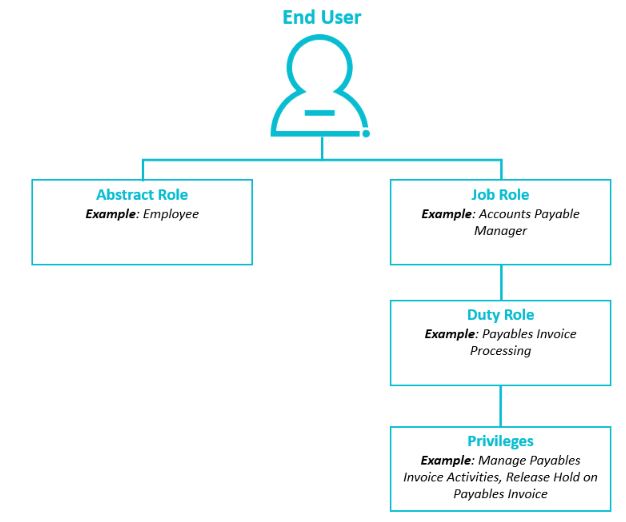
- Abstract roles – identifies a general association to the enterprise
- Job roles – the user’s job function; typically, users will have one or more duty roles assigned to them
- Similar to EBS’ responsibilities
- Duty roles – a grouping of access that enables a user to perform certain tasks; typically have one or more privileges assigned to them
- Similar to EBS’ menus and sub-menus
- Privileges – most granular security component, and determines which product (or SKU” licenses are triggered
- Similar to EBS’ functions
NOTE: This discussion regarding licenses and security models focuses on roles and privileges, not on data access, which is less relevant to managing costs related to Oracle Fusion Cloud licensing.
Unintended license authorization
Oracle Fusion Cloud provides out-of-the-box roles (otherwise known as “seeded” or “delivered”) that bring to life their suggested business processes. Many organizations, though, elect to utilize custom roles, primarily accomplished by copying and then modifying said roles at the duty role and privilege levels, to better fit their specific organizational and business process needs. When opting for the custom role route, organizations often lean on the conservative side by removing very little from the original role design to avoid inadvertently impacting the role’s desired capabilities. While well-intended, many privileges that seem benign – per their Oracle Fusion Cloud authored name or description – can trigger unexpected license authorizations. For example, the seeded tax manager role, by default, triggers licenses for several products that may not be intuitively related such as Procurement Cloud Service, Supply Chain Execution Cloud Service and Supplier Portal Cloud Service.
Misconceptions related to Oracle Fusion Cloud licensing
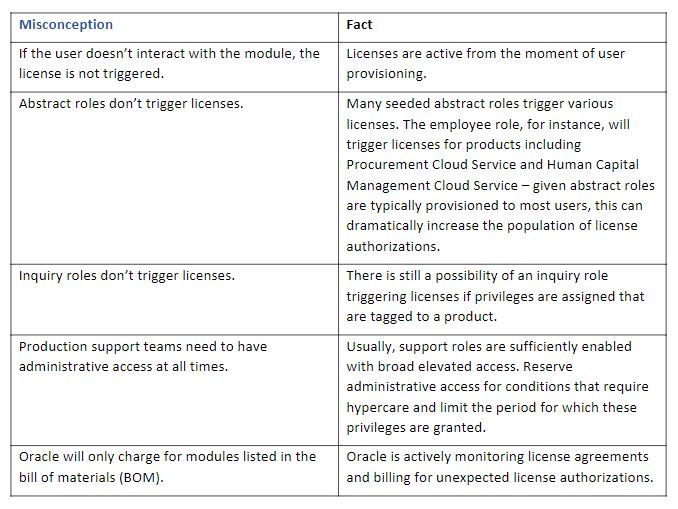
Planning and designing security with a licensing appreciation can be a daunting task when organizations face the many misconceptions about which conditions constitute license authorizations. Here, we clarify a few:
How to identify unexpected usage
Although there are a handful of tools/techniques provided by Oracle for purposes of monitoring license consumption, their consistent utilization is typically low. We strongly encourage organizations to diligently perform the following detective measures on a recurring basis, leveraging the following reports (which can be downloaded from the My Services portal) as supplemental tools
- Review the “hosted named user – unexpected usage report” – this report summarizes monthly usage in contrast (above and below) to contracted amounts.
- NOTE: It is very possible that originally contracted amounts were not right-sized for actual business execution. Said another way, organizations may need more than originally estimated.
- Analyze behaviors/trends via the “drill through” reports – view license usage by user and role as well as unexpected license use.
After confirming whether unexpected usage persists, organizations can further explore – or proactively plan for – these common contributing factors:
- Legacy implementation accounts: Are accounts for long-gone system integrators still active, with roles assigned to them?
- Inactive users: Are there roles assigned to active users, who don’t appear to need system access at all (i.e., haven’t used the platform in 30/60/90 days)?
- Platform support (tier 1/2/3 and/or help desk): Are powerful (and expensive) roles provisioned indefinitely? Or are they only assigned for limited periods – in a “break-glass” and change management compliant fashion – and then removed?
- “Extra” roles: Do users have roles that they don’t leverage? Would they miss them if they were removed? TIP: A structured user access review (UAR) is a great method for fleshing out these instances.
- “Efficient” results: Looking for reduction opportunities within larger groups of users who share the same access can help achieve greater results with smaller efforts.
- Shared, generic and/or service accounts: Are there excessive or unused accounts meant to facilitate integrations between boundary systems? These are often assigned elevated, seeded roles, and granted privileges that will trigger licenses.
More nuanced causes of unexpected license authorizations can be complex to resolve. Organizations will want to plan remediation of these cases carefully, factoring in potential cost savings versus level of effort, business impacts, and other considerations.
Frequency of review, to minimize unexpected usage
While a recurring review is a healthy habit to ultimately instill, there are peak times within the system’s lifecycle where licensing warrants increased attention:
- Before implementing Oracle Fusion Cloud, collaborate with Oracle to identify an adequate amount of necessary product licenses.
- During implementation, work with the system integrator and security implementation partner to understand licensing implications stemming from the proposed security model’s design.
- NOTE: This is especially important if the design will leverage seeded roles.
- Post-go-live, review Oracle-provided content (invoices, unexpected usage report and usage drill-through reports) to determine if consumption is higher or lower than expected.
SaaS licensing structures can seem foreign if approached with an on-prem mindset. Couple that with complex security designs, and there’s a recipe for unplanned expenditures. However, it is possible to minimize organizational exposure through thoughtful planning and steady governing behaviors.
Read our 2023 Global IT Executive Survey: The Innovation vs. Technical Debt Tug-of-War.
To learn more about our Oracle Fusion Cloud solutions, contact us.






