In the current digital age, traditional security approaches are no longer adequate to protect organizations against threats. With an increasingly hybrid workforce, use of cloud-based services and global interconnectivity, organizations should consider a different approach to cybersecurity known as zero trust architecture (ZTA). Zero trust is a term used interchangeably by security professionals in reference to a multitude of technologies, approaches, vendors, etc. We will review what zero trust architecture is, establish a common definition, remove the “buzz” out of the term and weigh its benefits as well as how to embark on a journey to implement ZTA principles.
This post is inspired by the growing interest in zero trust we see in our clients. They are asking questions like:
- What value does zero trust bring compared to traditional network segmentation and access control?
- What are the administrative and cost implications of adopting ZTA?
- What changes in the skillset portfolio will ZTA require?
- Will zero trust make it easier to validate compliance with regulations or introduce challenges?
- How can zero trust be leveraged for operational technologies (OT) environments and more, etc?
We will ponder these and other questions in our ZTA series but first, let’s establish a common understanding of zero trust.
Background
ZTA was first proposed by John Kindervag, a former analyst at Forrester Research, in 2010, and has since been adopted by the industry as the holy grail of cyber defense. Google’s implementation of its BeyondCorp has showcased the strength of architecture in the corporate world. However, ZTA’s true roots can be traced even further back to the U.S. Department of Defense (DOD) implementation of its Black Core concept in the mid-2000s. Black Core is a dedicated routing system, where all traffic is encrypted and authenticated, and network devices are configured to enforce strict access controls and traffic filtering policies. Only authorized users with the appropriate clearance and credentials are allowed access and the network is continuously subjected to monitoring and auditing to detect any unauthorized activity or potential security breaches.
While zero trust is recognized in the industry as the ultimate cybersecurity architecture, there is tremendous confusion as to what it truly means for each organization and how to implement zero trust; and to pile on, tool-centric marketing has turned this confusion into “buzzword” marketing, which is often misinterpreted in the market.
Establishing a common definition
At its core, zero trust is a security architecture that assumes no user or device should be trusted by default and that all access to systems and data should be evaluated on a per-transaction basis. This differs from previous security architectures where organizations implicitly trusted employees or corporate-owned devices simply because they were behind the corporate firewall. The primary goal of zero trust is to prevent unauthorized access, limit lateral movement and minimize an organization’s attack surface and exposure. Zero trust requires both contextual awareness and data to evaluate the risk of granting access to a resource or system. This context can include factors such as the user’s identity, location, device and behavior.
Why it’s gaining traction
While the idea of “deperimeterization” or micro-perimeters was introduced over a decade ago, there has been resistance to adoption due to a multitude of factors; including, but not limited to, cost of hardware, legacy applications, misunderstanding and resistance to change by the business and perceived impact to users. This was turned upside down by the COVID-19 pandemic that led to the rise of remote work, cloud computing and mobile devices. Also fueling this shift is businesses’ exponential demand for data, applications and collaboration in a hybrid work model, which is forcing organizations to rethink their IT landscape.
This dramatic change in the cyber risk landscape has led cybersecurity teams to build a patchwork combination of tools acquired for a specific capability or to address a particular risk. Over the years, inventory of these best-in-class tools has grown, increasing security cost, overhead to already undermanned security teams and adding to existing operational requirements, all while detracting from the user experience.
The above scenario has created an opportunity for security practitioners who are now revisiting the decades-old “castle and moat” approach to security. Additional reasons to consider zero trust include but are not limited to:
- Better management of risk from users
- Increased cyber resiliency and visibility
- Enhanced user experience
- More effective cybersecurity cost structure
- Better visibility and buy-in from management on organizations’ cybersecurity roadmaps
Common misconceptions about zero trust architecture
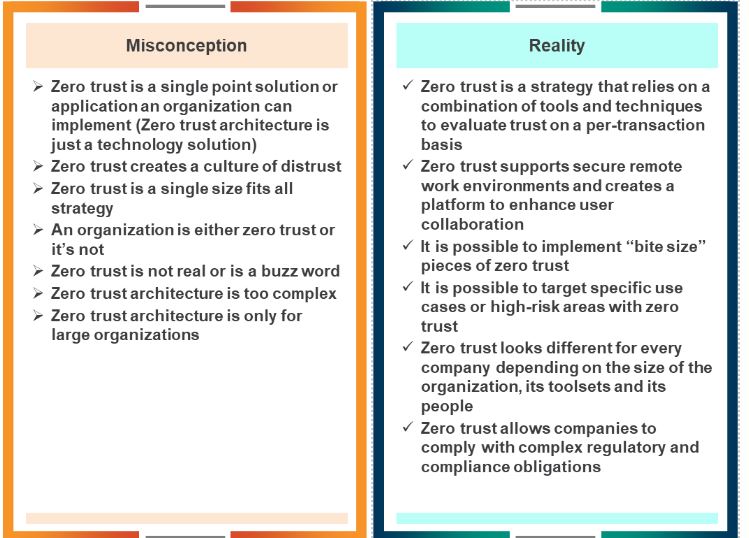
How to start the ZTA journey
Zero trust can take many forms and implementation may look very different to each organization. It is important for organizations to adequately prepare and start their approach to zero trust by establishing an understanding of these questions:
- Why is the organization considering a shift to zero trust architecture and what are the risks and threats that ZTA will help mitigate that the current state does not? What are the benefits to adopting zero trust?
- What are we trying to protect, and do we have a good understanding (inventory) of our assets and systems, user populations, data, applications and related crown jewels?
- Who within the organization should be responsible for implementing zero trust and ensuring its ongoing effectiveness? How will the various parts of the organization, from IT to HR to the business leaders, be involved.
- How will the organization go about implementing zero trust, what steps and technologies are needed, and what are the potential challenges to be addressed?
How Protiviti can help
Protiviti can help companies start their zero trust journey by assessing the company’s current security posture, identifying the attack and protect surface, identifying vulnerabilities and designing a zero trust reference architecture that meets the company’s unique needs. Protiviti can also provide guidance on implementing zero trust policies and procedures, as well as helping with the integration of zero trust technologies into the company’s existing IT infrastructure. With Protiviti’s expertise, companies can implement a zero trust framework that provides greater security and peace of mind.
Readers may also enjoy: The Shift to Zero Trust and Five Best Practices for Implementing Zero Trust.
To learn more about our security and privacy solutions, contact us.







