Five years ago, we wrote a post called “The 8 Character Password is Dead,” which was an in-depth look at password cracking in 2017 and how eight-character passwords do not adequately protect organizations.
In that analysis, we broke down the math and how quickly hardware purchased for under $5,000 could make an eight-character length irrelevant. Unfortunately, in just five years’ time, the numbers have gotten worse while infrastructure to perform this testing has become much more readily available for both good and bad actors.
With the rise of cloud computing and subsequently individuals’ access to top-of-the-line computing equipment, the eight-character password ‘standard’ continues to provide little protection to organizations.
Demo time
See the last article for a more in-depth breakdown of the different types of password cracking but in summary, brute force password cracking starts at a given length with one character and increments through each item specified in the character set until all possible combinations have been reviewed. Parameters around what to test can be customized — including the character sets. Any combination of four complexity types can be used for cracking: uppercase letters, lowercase letters, numbers and symbols. However, these are the most common:
- Three of four complexity types as it is the Microsoft Windows default
- Four of four complexity types as it includes every possible character combination on a US keyboard
Below is a quick video example of using the new cloud capabilities on a “complex” encrypted eight-character password from a standard Windows Active Directory deployment. In this demonstration, we use only brute force techniques and no dictionary list (which is likely faster). Specifically, the second brute force type above (all possible characters) is used:
As you saw, we moved from nothing to cracked password in under three minutes. Any eight-character password would have been cracked in no more than eight hours and cost at most $62.59. As you can imagine, if an organization only requires three of the four complexity requirements, the number of possible combinations drops dramatically and it can cost as little as $2.45 to go through every uppercase, lowercase and number combination.
Real-world example
The haveibeenpwned.com application maintains a collection of many major password breaches and their associated hash values. Most popularly, the application allows users to search for their own passwords to determine if they’ve been included in a data breach. We downloaded the entire haveibeenpwned.com password list in the same hash format as standard corporate Active Directory environments (NTLM) and selected a ~1% sample or 6.6 million passwords.
Using this sample, within ten minutes, 4 million (61%) of the 6.6 million selected passwords cracked using the same system as above. Within an hour, 4.7 million (71%) passwords cracked. A short video version of this example can be seen here:
The new math
In our previous post, we outlined the capabilities of a system at the time that could be bought for under $5,000. We’ve updated our math to show what can now be achieved for under $8 an hour and with little to no setup. The results are astounding:
For $62.59 ($7.824 x 8 hours), any eight-character active directory password (uppercase, lowercase, number and symbol) can be cracked in AWS on the g4dn.metal instance type. Amazingly, $7.82 per hour allows guessing of as many as 230 billion passwords a second. Below is a screenshot showing live cracking of an eight-character password:
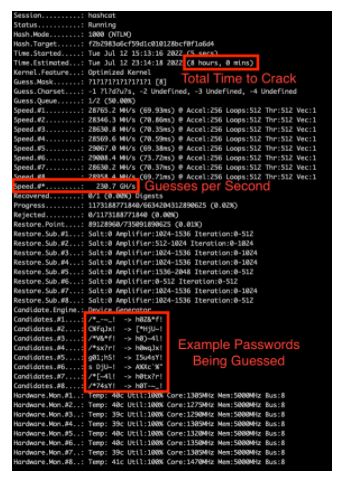
Note: Specific speeds and consistency of speeds may vary based on configuration over long periods of time
The solution
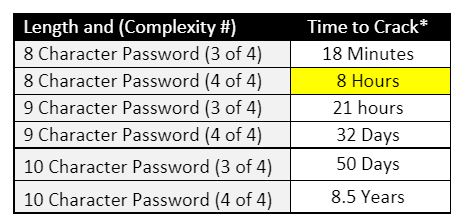
Passphrases. Increasing the length of passwords exponentially increases the difficulty and consequently, the time, to crack (see table above) a given password.
Using long passphrases that are easy to remember not only increases the security posture of the organization but also reduces the possibility of employees saving their passwords in a file or physically writing them down.
Now, more than ever, the eight-character password ‘standard’ is unacceptable. Increasing password length and mandating users use passphrases can dramatically increase any organization’s security posture.
Today its 62 dollars and 59 cents. It’s anyone’s guess how cheap it will be in five more years.
To learn more about our attack and penetration solutions, contact us.





