This article would be of interest to security professionals looking to enhance security practices around passwords.
Passwords have been computer security’s first and last line of defense for decades. Despite exponential growth in computing power, 8 character passwords still remain the security standard for many organizations. This password length is no longer acceptable. With under $5,000 in equipment, every NT LAN Manager version 1 (NTLM) combination of uppercase, lowercase, and number can be guessed or “brute forced” in 7 minutes. If you want to include all of the special characters, that number becomes 96 hours.
Types of Password Cracking
It’s important to first discuss the different types of password guessing attacks. Password cracking predominantly has two variations: brute-force and dictionary attacks.
- Brute forcing iterates through all combinations of characters. For example, if the password were 2 characters, brute forcing would guess “aa” the next would be “ab” the next would be “ac” etc. until all the combinations were exhausted. This method of cracking is incredibly thorough, but it becomes quickly inefficient the longer the password space.
- Dictionary attacks use a known list of words, and iterates through that list attempting to match the dictionary word to the password. This article will focus on brute forcing, and will comment on dictionary attacking when appropriate.
The difference between types of password cracking is important because most individuals utilize passwords that contain dictionary words or variations of words ($ummer2017). Due to the use of common words attackers generally utilize dictionary attacks before brute forcing as it is more likely to crack a longer password. However, for the purposes of this article we will assume the harder and longer type of cracking brute forcing.
The Password Industry Standard Has Been 8 Characters For Too Long
Password cracking has evolved greatly from the days of John the Ripper and Cain and Abel. It effectively boils down to the use of Graphical Processing Units (GPUs) instead of Central Processing Units (CPU’s). GPUs are designed to conduct simple calculations very quickly which make them a perfect conduit for cracking passwords. Utilizing these simple calculations GPU’s are exponentially faster at going through a list of possible combinations of letters, numbers, and special characters.
Unlike many of the other security standards this eight character password length “best practice” has not evolved. Moreover, it poses a significant security risk to current windows domains. For a sophisticated attacker it is quite trivial is to gain a valid encrypted windows hash utilizing a tool such as responder and putting it into a powerful GPU system (often only takes minutes).
Building a Password Cracker For 5k
A quite powerful GPU cracker can be built for under $5,000. There are many guides on the Internet about this but at its very core it comes down to buying a motherboard, processer, power supply, case and memory that is capable of handling multiple GPUs. One can usually buy all of these components as well as 4 quality GPUs for under $5k. These components can be assembled, an operating system can be installed and a called OclHashcat is all one needs to get things going. OclHashcat is a program that optimizes the GPUs for password cracking and allows the GPUs to test billions of passwords per second.
The Test
All of this comes back to the 8 character password and its inherent number of possible character combinations. With traditional CPU password cracking, it would take around 92 years to guess all of the iterations using uppercase, lowercase and numbers for an 8 character password. For the same possible combinations, it takes a moderately architected GPU cracker just seven minutes.
To illustrate, Protiviti ran various tests against a random anonymized sample of NTLMv1 hashes acquired from domain controller dumps using a custom character mask that brute forced every uppercase, lowercase, and number on 8 characters. The results are as follows:
- Of the ~35k hashes, 14% were cracked. This indicates that in our sample that 14% of passwords contained no more than 8 characters and did not contain a special character of any kind. This 8 character crack took approximately 1 hour and 20 minutes.
- When the same ~35k hashes were run against an 8 character mask that contained uppercase, lowercase, numbers, and special characters the password crack success rate nearly doubled to 28%. This 8 character brute force crack took approximately 2 days.
The conclusion here should not be understated: 7 out of 25 users in this population were cracked within 2 days. Additionally it should be noted that all of these cracked passwords were fully compliant within their respective password policy. Each of these cracked passwords (around 9,000) represent a unique vulnerability to their companies and each of these could be strengthened by increasing the password length requirement.
The Math
The math behind password cracking is quite simple. In order to determine the number of possible combinations one takes the length of the password and multiplies it to the power of the character mask. For example, if you are attempting to crack an 8 character password, using uppercase (26 characters), lowercase (26 characters), and numbers (10 characters). You would add these together: 26+26+10=62 and use that as the exponent of the password length: 62^8. The table below shows the great difference between 9 character (62^9) and 10 character (62^10) passwords:
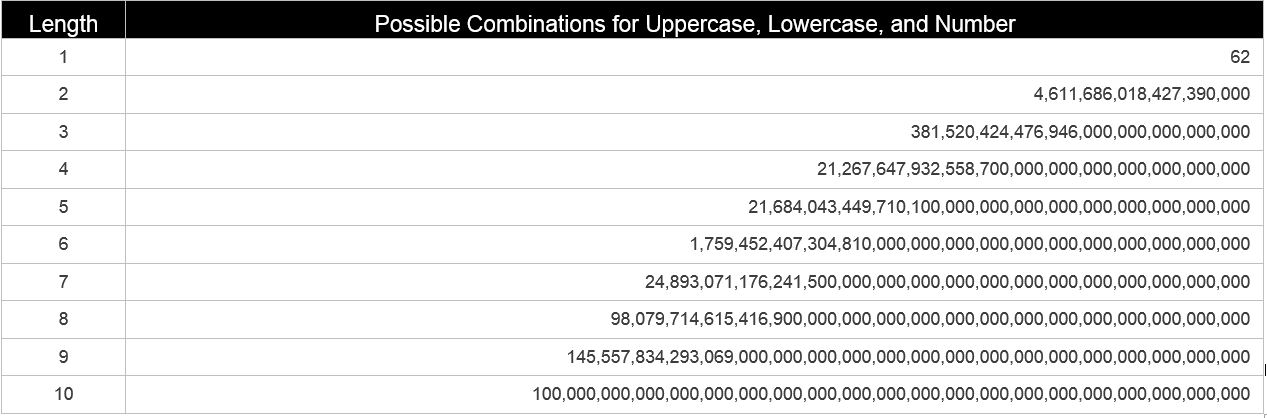
Even at 15 billion password guesses a second (that can be achieved with the $5,000 cracker) the jump from 8 to 9 to 10 is significant. Let’s take a look if we add special characters (for a total of 94 characters):
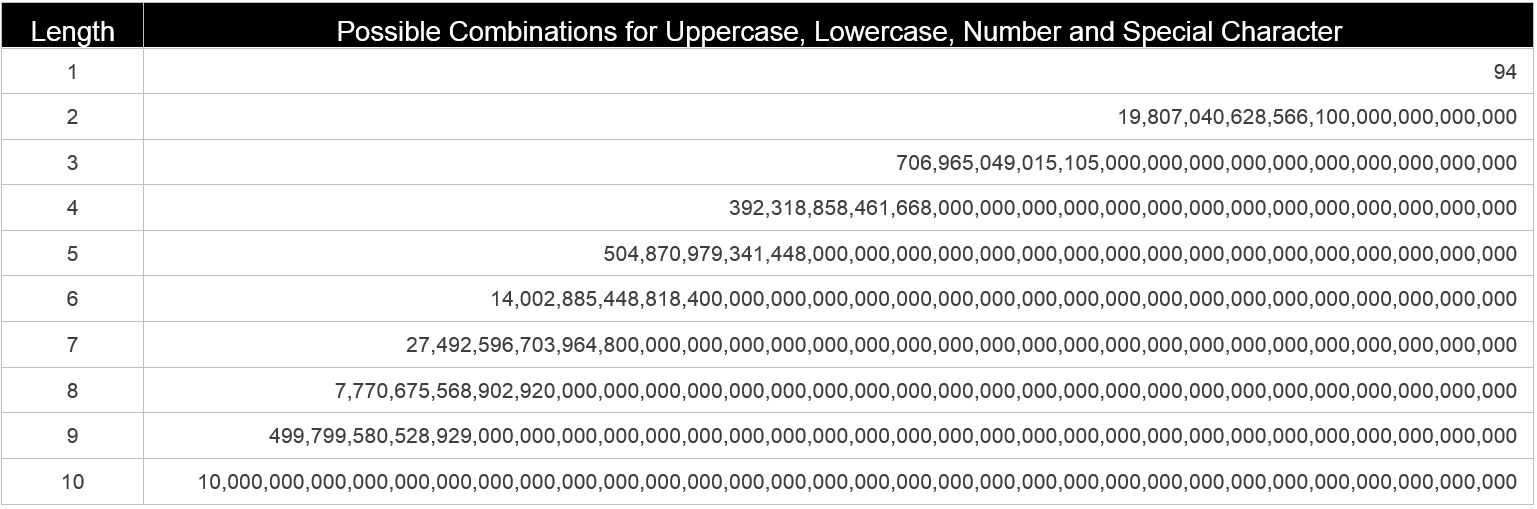
This math reaches some conclusions relatively quickly. If we simply changed passwords to 9 or 10 characters, the same brute forcing techniques become much lengthier in time:
- Time to guess uppercase, lowercase, and number goes from over 7 minutes with 8 character to just over 5 hours for 9 characters while 10 characters takes it to 9 days
- Time to guess uppercase, lowercase, number, and special character is 4 days with 8 characters and over 1 year for 9 characters while 10 characters takes it to 10 years
The number increase dramatically when we go to 10 characters. It should be noted that the environment used in this case study was low powered compared to a hacker for profits or a state sponsored actor.
Time to Change
Based on our conclusions above, increasing password length by even a single character dramatically improves the chances the password not being cracked. Adding 2 characters makes it very unlikely (unless it is a dictionary word). Utilizing long passphrases (sentences with spaces – special characters not needed) makes it even harder to crack!
This minor change in length and time required to enter a password drastically improves the security posture of an organization. As such, why don’t we all rethink the password length “industry standard”?