As the number of ransomware attacks rise, the failure of businesses to properly invest in cybersecurity tools, technologies and trained resources continues to become more prevalent. Not only do the ransom demands continue to increase but the average cost of ransomware recovery continues to skyrocket. Sophos research revealed that the average ransomware recovery costs are $1.85 million compared to $761,106 just a year ago. Zero trust principles can be implemented across company environments to defend against rampant ransomware cybercrime.
Ransomware trends
Ransomware made its first appearance in 1989. Since then, its scope and breadth has changed dramatically, from simply encrypting files and demanding a ransom payment to exfiltrating data or shutting down entire networks. Additionally, the way malicious actors spread ransomware has also evolved. For example, ransomware-as-a-service (RaaS), which are available ransomware services platforms where attackers can obtain ransomware tools, technology, and other capabilities. These perpetration tool sets are made available to threat-acting organizations, are offered based on their intended usage (fees charged based on use e.g., similar to the SaaS model) and are available from multiple independent black-web sources to facilitate Ransomware attacks.
Ransomware has also begun to take aim at managed service providers (MSPs), targeting both the MSP and the MSP’s clients. By far, the most common ransomware infiltration method continues to be via phishing. Over the past year, the COVID-19 pandemic has revealed technology weaknesses within industries that may not have had sufficient cybersecurity protection for work-from-home business users. Target industries include healthcare, education and local government.
We will likely continue to see a rise in state-sponsored ransomware to further political agendas, and phishing will most likely continue to be the most common infiltration method. Additionally, vulnerable industries such as healthcare and associated supply chains may continue to be targeted due to a lack of adequate cybersecurity infrastructure.
Further, we may see increased use of artificial intelligence to develop more sophisticated attacks. Attackers can use artificial intelligence to:
- Have ransomware programs impersonate standard users or systems behavior to deliver and execute malicious software payloads
- Trigger the malware to run at a certain time
- Collect data regarding attack techniques and their respective successes or failures, and
- Trigger attacks, depending on the types of vulnerabilities that exist within environments.
The importance of zero trust today
The Executive Order on Improving the Nation’s Cybersecurity released on May 12, 2021, by President Biden revealed the importance of zero trust and cloud security in the world today. The Executive Order specifically states “The Federal Government must adopt security best practices; advance toward Zero Trust Architecture; accelerate movement to secure cloud services, including Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS); centralize and streamline access to cybersecurity data to drive analytics for identifying and managing cybersecurity risks; and invest in both technology and personnel to match these modernization goals.” We may have seen cybersecurity-related executive orders in the past, but this is the first time we have seen the United States government provide an order quickly after an incident (the Colonial Pipeline ransomware attack). Clearly, zero trust is being sewn into the fabric of cybersecurity and has begun its journey across all industries.
Zero trust defenses against ransomware
Although ransomware attacks are becoming more sophisticated and continue to become more prevalent and innovative over time. A typical attack is performed via the three steps outlined below.
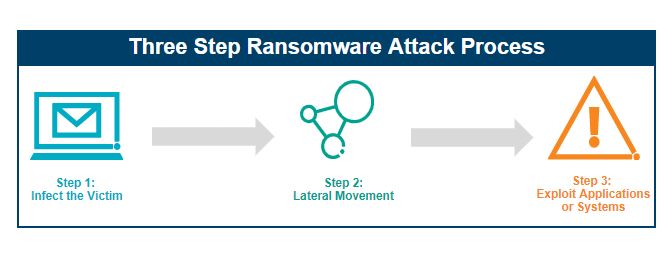
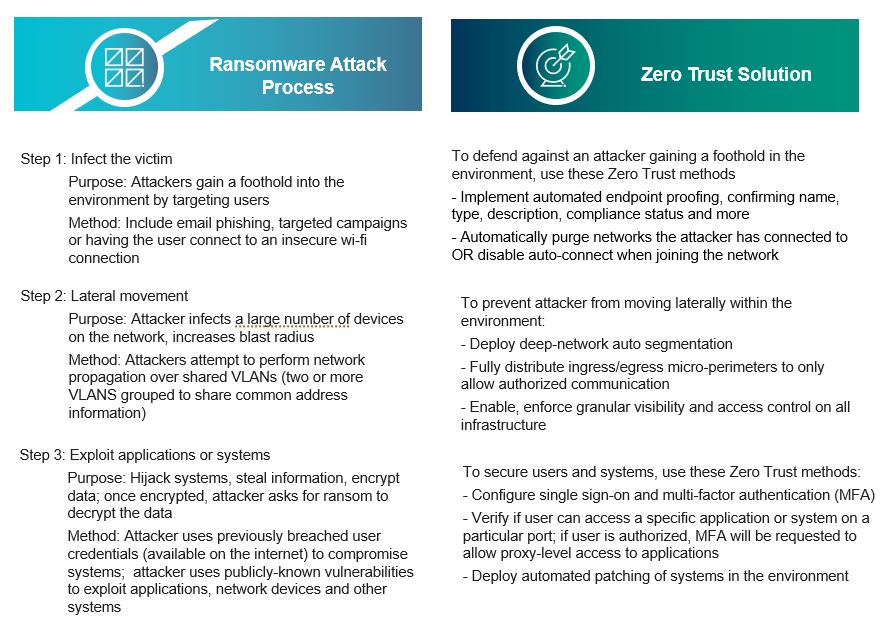
Each aspect of the ransomware attack process has at least one zero trust solution, which includes the implementation of security principles, processes, tools, or technologies that can be used to defend the environment. The ransomware attack methods, purpose and zero trust solutions are described in detail below.
What changes should be considered in the near future?
As organizations continue to mature their security posture, they should consider making the following changes to protect against ransomware attacks:
- Implement zero trust principles in the environment – Implementing zero trust principles can significantly reduce the impact of a ransomware attack and it may also prevent a ransomware attack. It is an effective principle to reduce the overall security risk.
- Use automation to contain ransomware – This includes mechanisms to stop lateral movement throughout the environment (enabling micro-segmentation) and block access to sensitive data and business-critical systems (requiring the use of MFA and SSO).
- Introduce User and Entity Behavior Analytics (UEBA) – UEBA tools can be implemented and configured to identify abnormal activity and can detect when a ransomware program has been executed in the environment.
- Conduct purple team exercises – Perform periodic purple team ransomware exercises to assess how susceptible an organization is to ransomware. A purple team exercise is a practice in which an offensive team (red team) attempts to infiltrate the organization’s environment, while the defensive team (blue team) reviews existing security prevention and detection tools to verify if attacks have been successfully thwarted. These exercises can assist with identifying areas of improvement to further strengthen capabilities against ransomware attacks.
Read our blog, Five Best Practices for Implementing Zero Trust, for more information.
John Stevenson also contributed to this post. To learn more about our zero trust, ransomware and other cybersecurity consulting capabilities, contact us.