Integrated Services Digital Networks (ISDN) and Public Switched Telephone Networks (PSTN) are no longer the primary transmission path for basic voice or telephone signaling. In fact, according to statistics within a 2018 report released by the Federal Communication Commission (FCC), the use of Voice over IP (VoIP) solutions has dominated the US market since 2016. Due to this changing technology landscape and the responsibility to maintain and evolve the Payment Card Industry Data Security Standard (PCI DSS or DSS), the PCI Security Standards Council (PCI SSC) released a November 2018 update to the Information Supplement Protecting Telephone-Based Payment Card Data.
This published update suggests the Council and acquiring banks will focus on three key points:
- How merchants and service providers define their PCI scope with the inclusion of telephony processes
- How Qualified Security Assessors (QSAs) properly validate and document each DSS control that would apply to Telephone-based payment systems
- How Telephone-based payment systems have been validated as out-of-scope.
Telephone-based, card-not-present CNP) transactions commonly involve the transmission of spoken Primary Account Number (PAN), Card Validation Values (CVV), cardholder name, expiration date and sometimes personally identifiable information such as a postal code and shipping address. Without appropriate risk mitigating controls, this sensitive/personally identifiable information could be compromised with little effort by an adversary or disgruntled employee with the use of audio recording equipment or data packet capture technologies.
According to the Information Supplement, “Telephone-based payments represent an area of opportunity for fraud as this method of payment exposes account data in the clear and must be given full consideration in any security strategy and PCI DSS compliance program.”
As such, QSAs have the responsibility to clearly understand and validate the defined scope of the assessed environment. This validation commonly begins by gathering supporting evidence of the payment channels (DSS 1.1.3 – data flow diagrams), the network that supports the cardholder environment (DSS 1.1.2 – network topologies) and the segmentation strategies used to isolate the cardholder date environment (DSS 1.2.1 – a firewall rule-set analysis to confirm permitted traffic). Additionally, the master physical inventory (DSS 2.4) and service provider responsibility matrix (DSS 12.8.1) should complement and support the evidence gathered.
“Accepting spoken account data over the telephone puts personnel, the technology used and the infrastructure to which that technology is connected into scope of PCI DSS.”
The Council’s revised guidance applies to all instances of telephony-based handling of cardholder data (CHD), including small merchants with a simple telephone environment where payments are taken over a single telephone line to large multi-site environments where hundreds of card payment transactions occur simultaneously.
Simple Telephone Environment
A simple telephone environment is an environment where an entity (e.g., a merchant) sends or receives account data via a single or limited number of telephone lines (e.g. dial-up payment terminal or a virtual terminal). An example of a simple telephone environment includes one where a traditional telephone line (e.g. “plain old telephone service,” or POTS) is used. In this example the client is not considered responsible for the transmission of card data over the POTS line. However, the client is still responsible to comply with the DSS if an answering machine is used to capture CHD (electronic storage) or if a representative manually records the CHD (physical/electronic storage).
However simple telephone environments also include those using VOIP. The Information Supplement makes it clear that the simple act of transmitting spoken CHD on a VOIP connection brings that connection into scope. In fact, compliance with the DSS is necessary if the payment terminal or PBX (Private Branch Exchange) connects to the acquirer via Internet Protocol (IP), if CHD is spoken over the VOIP line, or if the call conversation is transmitted to a wireless headset. Even in the smallest business, VOIP telephone connections are very common, which makes PCI compliance requirements critical.
Complex Telephone Environment
Complex environments generally involve the use of multiple systems and servers. Assets may include internal telephone switches, the voice and data network assets (e.g. routers, firewalls, switches) and the call recording and storage servers. Often, this type of environment is a customer service center or call center. In this type of environment, the assets used by the entity to manage the calls are in-scope, as are the phones, network connections and any other connected devices.
This call switching equipment and other in-scope components requires configuration standards, system hardening, logging and secure authentication, vulnerability scanning and penetration testing, among other controls.
Service Providers
Within the PCI SSC Online Glossary, it is noted that a service provider “…that involves only the provision of public network access — such as a telecommunications company providing just the communication link — would not be considered a service provider for that service (although they may be considered a service provider for other services).” This stance is still supported but the new guidance brings attention to ‘other services’ that would bring the telecommunications company in scope, as noted within the Information Supplement:
“Some telecommunication equipment owned and operated by the telco, hosted within the entity’s infrastructure for the purpose of provisioning access to public network, may be considered in scope for PCI DSS.”
“If the third-party equipment resides on the entity’s premises, there may be a split PCI DSS responsibility between the entity and the service provider.”
“Everything after the third-party equipment should be considered in scope. If the third-party equipment resides on the entity’s premises, there may be a split PCI DSS responsibility between the entity and the service provider.”
The following image from the Information Supplement provides a good overview of the telephony guidance provided:
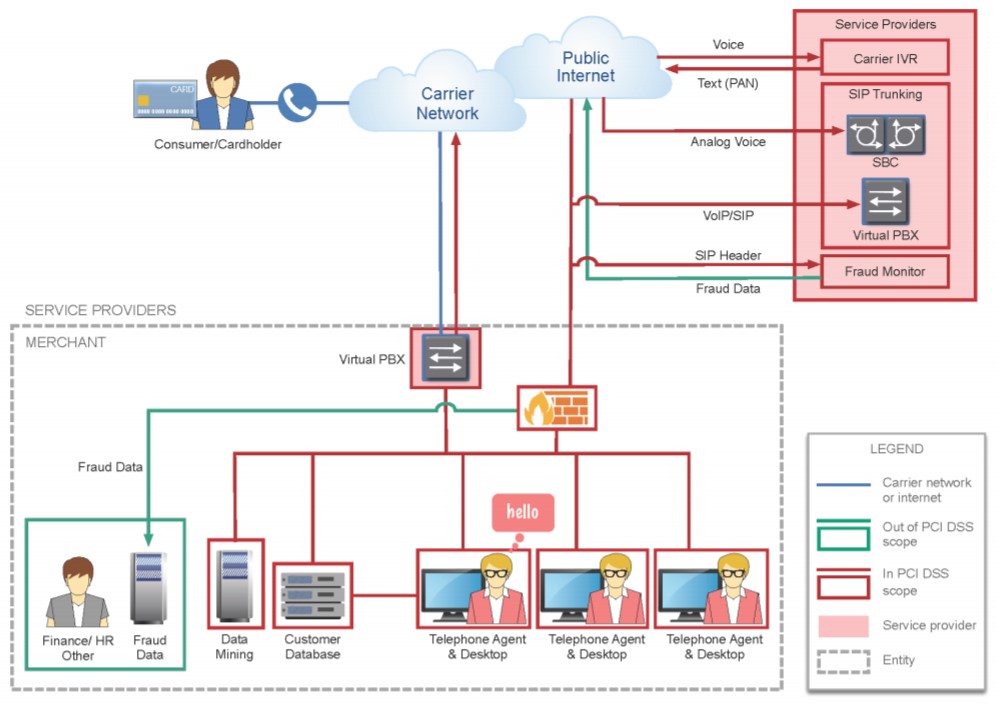
Call to Action
Perform a thorough assessment of your organization’s telephony processes to understand how CHD is handled and protected. During the assessment, ensure data flow diagrams that visually depict the flow of CHD are created, network topologies are updated to reflect telephony segmentation points, asset inventories contain all in-scope telephony equipment and configuration standards used to harden in-scope assets are created. Also, keep in mind that if segmentation strategies are leveraged, then an internal penetration test should be conducted to validate the scope of the environment and hardening of the telephony assets.







