If the year 2020 taught us anything, it was to expect the unexpected. During this unique time, we saw companies adapt to a new reality brought on by the COVID-19 pandemic, making significant investments to ready their organizations to weather the next storm. We also saw substantial change in Industrial Control Systems (ICS) security environments, a trend that brings a range of considerations for organizations large and small.
In a recent webinar, we talked about what ICS security means to organizations and how organizations can build effective ICS security programs to sustain the company in 2021 and well into the future. In this blog, we highlight what we feel are the most important steps to developing and implementing an effective ICS security program.
Step 1: Establish Lines of Communication with Key OT Contacts
It is critically important to engage Operational Technology (OT) teams early, gaining buy-in and support from “security champions” at each site. In many companies, technology teams and operational teams work separately, with differing priorities (OT focused on availability/resiliency, IT more focused on connectivity/security). The IT security organization’s top priority is to secure the environment, while those who work in operations are focused on driving efficiencies and ensure production capabilities are completed as quickly and safely as possible. The OT teams can often view security and additional controls as impediments to achieving their objectives.
We often recommend organizations looking to enhance industrial control system security measures start with building organizational awareness around why controls are necessary, then gain buy-in from the teams that will be in charge of operating those controls. Establishing “security champions” – individuals that can communicate the organization’s security priorities in a way to generate that buy-in – is a key step we find eases the process of bridging any gaps between teams.
Step 2: Establish Program Ownership and Align with a Framework
During our webinar, we asked the audience who in their organization is responsible for ICS security within the company. About a third (33%) responded that the Chief Information Security Officer (CISO) holds this responsibility, followed by the Chief Information Officer (CIO), a plant manager or an ICS Security Manager. Nearly a quarter of the audience (25%) responded “other,” suggesting this critical role may not be given the attention it needs.
The next step involves identifying who is going to own and drive this program. The goal is getting the right people to help prioritize risk and identify critical assets / locations for the organization. Support for ICS security initiatives will be needed from corporate IT, cyber security, physical security on site, and operational technology (OT) teams. As mentioned previously, buy-in and support of the automation team or OT teams will be important as those individuals will be able to articulate the challenges at the field level and business goals / requirements. Their input will be critical in mapping out the path forward and designing controls that meet OT team’s needs and improve the security of critical assets. Having senior leadership support ensures long-term success, and that partnership starts with making sure that executive management understands the risks, how those risks can be mitigated, and what benefits can be achieved (cost savings, improved efficiency, resiliency) in setting a defined strategy for an ICS security project.
There are a number of different frameworks that companies use to align their ICS security programs. As we help clients develop their own ICS security procedures, we often pull from multiple frameworks to develop a solution that works best for the organization’s specific needs. 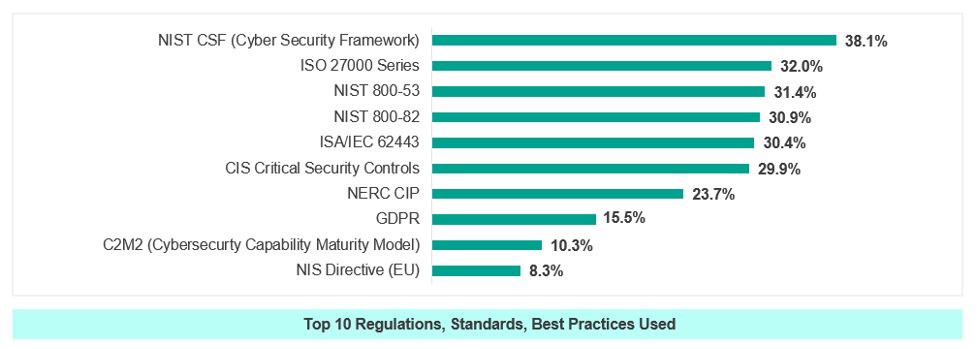 Our clients in Oil and Gas tend to align with the NIST Cybersecurity Framework, some mature clients leverage several controls from NIST 800-82 and, in many cases, our team recommends a hybrid framework that combines approaches from both. (Image source: SANS 2019 State of OT/ICS Cybersecurity Survey)
Our clients in Oil and Gas tend to align with the NIST Cybersecurity Framework, some mature clients leverage several controls from NIST 800-82 and, in many cases, our team recommends a hybrid framework that combines approaches from both. (Image source: SANS 2019 State of OT/ICS Cybersecurity Survey)
Step 3: Quantify ICS Risks and Prioritize Implementation of Controls in a Risk-Based Manner
Once an organization builds its ICS Security governance structure, it needs to determine how to address the multitude of risks facing the company. There are likely multiple different operational sites with difference risk landscapes and technology stacks, so a quantitative approach is needed to determine how to start address known security risks. Understanding the legal and regulatory landscape will help with some of the risk prioritization, since lacking those controls may directly lead to fines. When determining where to start, we also recommend risk ranking facilities to create a prioritized approach for security and to gain a better understanding of the business. Because resources and time are often constrained, making a prioritized approach a necessity. Furthermore, we recommend utilizing a pilot approach with a plant site where relationships are strong to build support for the program and better understand the business impacts to proposed security controls. It is important in the pilot phase to be flexible, learn from the business and document everything.
Looking ahead to 2021, we see that organizations are looking for controls that do not negatively impact resilience and availability of critical assets. The chart below identifies key implementation challenges that ICS organizations encounter. As expected, availability and safety are two of the most important considerations. If you’ve gone to your plant sites recently, you are certainly aware of the importance placed on health and safety. Health and safety organizations have made tremendous strides the past couple decades in getting their mission ingrained with operations and your teams should be keenly aware of how to integrate with health and safety teams and explain how security can assist in creating greater confidence in the safety and well-being of plant employees.
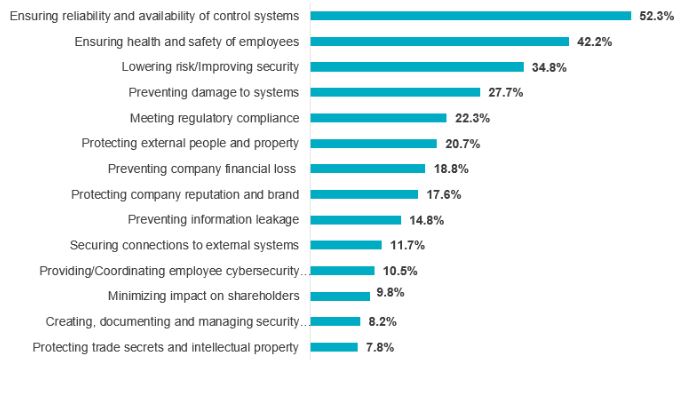 (Image source: SANS 2019 State of OT/ICS Cybersecurity Survey)
(Image source: SANS 2019 State of OT/ICS Cybersecurity Survey)
With regards to health and safety technology, a key focus is the need to protect safety information systems. This involves intentional design around ensuring safety systems are connected to the right sensors to create alarms in the event something happens, and that the systems can remain available despite unexpected challenges.
We are seeing more companies focusing on separating their safety systems from their additional control systems, which helps ensure that, if the main control system is compromised, it doesn’t necessarily compromise the health and safety systems.
It’s a challenging world out there, with attackers constantly devising new ways to impact control systems and cause physical harm to environments and people. Organizations that know exactly how their operational data flows going in and out of their systems, know which users should have access to make changes and require strong authentication processes can mitigate considerable damage before it happens.
Summary
Leadership buy-in, strong communication across IT departments and operational facilities, and having the right people and systems in place are leading factors in ICS security success. Don’t be intimidated by what may seem to be a daunting task. We liken the challenge to that adage about eating an elephant one bite at a time. Prioritize risks. Prioritize locations. Develop a risk framework. Start with a pilot approach. Then build on ICS security success with an iterative approach that builds upon the implementation successes of previous site deployments.
To learn more about Protiviti’s ICS security program capabilities, contact us. And, listen to our podcast, Building an Effective Industrial Controls System Security Program.






