When it comes to cybersecurity and privileged access management (PAM), we have some bad news, and we have some good news. “Breaches are inevitable” is the bad news. But the good news is that adding resiliency to PAM programs can, and will, make a significant difference in an organization’s risk posture. In a recent webinar on this topic, we focused on how cyber resiliency gives organizations the ability to continuously deliver intended outcomes and services despite adverse cyber events. We like to illustrate the concept by saying that cyber resiliency lives at the intersection of cybersecurity and business resiliency. For PAM, this means establishing the capability to continue delivering outcomes and services despite threats against privileged accounts.
According to Gartner and other leading research firms, PAM is, and has been one of the top 10 projects that security leaders should be implementing now. These industry experts anticipate that investment in PAM will continue to accelerate in the coming years since most attacks do involve the compromise of a privileged credential. Anyone is susceptible. These attacks are happening across the technology stack and while many companies are starting to do the basics around PAM, they maybe have not yet expanded their scope beyond the typical administrator-type accounts and the things that IT owns and manages. We strongly advocate that approach must be expanded and that PAM needs to be an enterprise-wide program.
At its core, privileged access refers to permissions or entitlements within some system or application that are significantly greater than those available to the majority of users. A privileged account is then simply an account that has elevated access to an organization’s systems, application data, etc. It is important to note that privilege is bigger than default administrator accounts or those things that IT owns and manages, and really, PAM should be evaluated based on risk, so organizations need to think about privileged account management and their PAM programs using a risk-based approach.
Protiviti’s Privileged Account Management Framework
We often see customers deploy PAM tools as a response to an audit finding or compliance gap, but then struggle to truly mitigate privileged access risk beyond that initial push. To assist our clients with this journey, Protiviti has developed a framework to inform the elements of a comprehensive PAM Program:
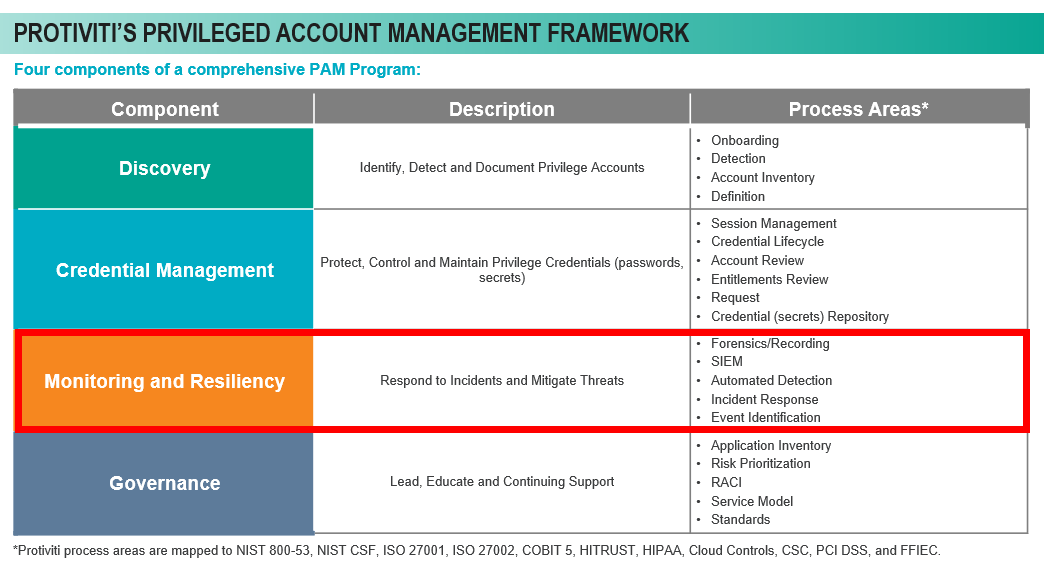
There are four components to our PAM framework:
- Discovery – Identification, detection and documentation of privileged accounts
- Maintain an enterprise definition of privilege
- Use of automated scanning and manual discovery processes to continually identify privileged accounts
- Credential Management – Managing the lifecycle of those privileged credentials, including:
- Creation and retirement of privileged accounts,
- Access requests and recertification of the account and entitlements
- Session management
- Monitoring and resiliency – Detecting, responding to, and mitigating threats against privilege:
- What should be monitored and alerted?
- Has the organization identified the right events?
- Does the organization have the incident response plans identified to take action against those events?
- Does the organization have the capability for high-risk use cases to record privileged sessions for forensics purposes?
- Has the organization enabled integrations with its Security Information and Event Management (SIEM) product?
- Does the organization have the ability to do automated detection and response?
- Governance – how the organization will make the PAM program run over time
- Begins with the definition of an enterprise-wide PAM standard
PAM is something that needs to be taken on in a risk-based approach. In the absence of doing so, organizations either risk over-controlling every privileged account, which can be very expensive and intrusive to users, or under-controlling every privileged account, which doesn’t mitigate the risk. Using a risk prioritization model can help determine what systems and assets are most critical and which accounts have the highest risk and need the strictest controls.
Being resilient means fully automating immediate response activities to include mitigation. The key is to drastically reduce the window from detection to effective response, taking the capabilities of multiple systems and making them work together to provide a faster path to mitigation.
Use Cases and Tools
Traditional approaches for monitoring require significant investment in technology and training, yet still rely on human intervention to do research and take mitigating actions. In today’s attack landscape, attackers are able to exfiltrate data from an organization long before a breach has been identified, so reducing time to respond is key.
Being resilient means reducing the reliance on human intervention and introducing technology that makes intelligent decisions driven by data that is aggregated across multiple data sources. During our webinar, we presented a number of use cases, followed by a tools demonstration by our partner CyberArk. A couple of high-risk use cases that can be implemented quickly to automate remediation and reduce risk include:
- Detecting new unmanaged privileged accounts
- Bypassing the PAM solution for privileged credential checkout
- Accessing the PAM solution at irregular times or from irregular locations
These use cases are good examples of potentially nefarious behavior that organizations can automatically respond to by programmatically vaulting credentials, locking out users in question and alerting appropriate teams.
Final Thoughts
Breaches are becoming more inevitable and previous security postures like monitoring only as a reactive control are no longer sufficient. Organizations should look to introduce resiliency in order to be able to continue providing business-as-usual services, despite threats (both internal and external) against privilege. Privileged credentials are used in the majority of breaches, so PAM resilience is critical. But implementing PAM resilience should not feel like an insurmountable mountain.
In many cases, PAM resiliency can be introduced as an out-of-the-box solution, using technologies that most organizations already have. Start slowly by implementing high-value, low-effort use cases and expand from there. Already have an enterprise PAM program? Assess it for resiliency. Not sure where the organization currently stands? Assess what currently exists in the PAM space. Document high-risk use cases where resiliency may be lacking and implement with existing technology. Enable a partnership between your PAM and security operations team to enhance PAM resiliency over time.
To learn more about cyber resiliency in PAM, listen to the full webinar or contact us.





