In today’s fast-paced business landscape, organizations rely heavily on robust enterprise resource planning (ERP) systems like Microsoft Dynamics 365 Finance and Supply Chain Management to streamline operations and drive growth. However, granting unrestricted access to sensitive financial and operational data can pose security risks and compromise data integrity. That’s where read-only roles come into play, providing a powerful solution to strike a balance between providing visibility and restricting modification capabilities.
Microsoft Dynamics 365 Finance and Supply Chain Management gives clients the ability to customize their security environment, providing the flexibility needed to modify Dynamics 365 security to fit their business and user needs. At a high level, the elements that make up Dynamics 365 security are roles, duties, privileges and securable objects. When modifying security, it is best practice to follow the security hierarchy. This hierarchy states that securable objects are assigned to privileges, privileges are assigned to duties, duties are assigned to roles, and roles are assigned to users. This enables security to be linear and uniform, preventing confusion or accidental incorrect assignment.
There are four access types a developer can assign to a role: read, update, create and delete. This access is granted at the securable object level. Access becomes very prevalent when restricting permissions. One way to restrict access is by creating a read-only role. Read-only roles can be used to limit a user’s functionality by removing the ability to create, modify or delete data in the application. An example use case for a read-only role is for audit personnel. Often, audit requires the ability to view all items, but should not be able to update.
D365FO has out-of-the-box duties and privileges that may initially appear to be limited to read-only access but actually provide more than just viewing capabilities. These duties and privileges begin with the words ‘inquire’ or ‘view.’ For example, the ‘inquire customer retention’ duty appears to be read-only but contains the ‘maintain customer retention’ privilege. It is important to take this into consideration when building read-only roles. To ensure a role is strictly read-only, check the role permissions report and ensure all fields above read are unset.
When creating a read-only role, it is important to ensure that the assigned securable objects do not provide access above read. The process to create a read-only role includes:
- Creating a new privilege and assigning the necessary securable objects with read-only permission.
- Creating a new duty and assigning the privilege created in step one.
- Creating a new role and assigning the duty created in step two.
Once a role is correctly created, the changes should be published so they can be assigned to users. It is necessary to follow the correct change management guidelines to promote and test security through appropriate environments. Any changes related to end-user security must be driven by business input rather than being led solely by IT. Prior to implementing any changes, it is essential to obtain approval and sign-off from the respective business owners.
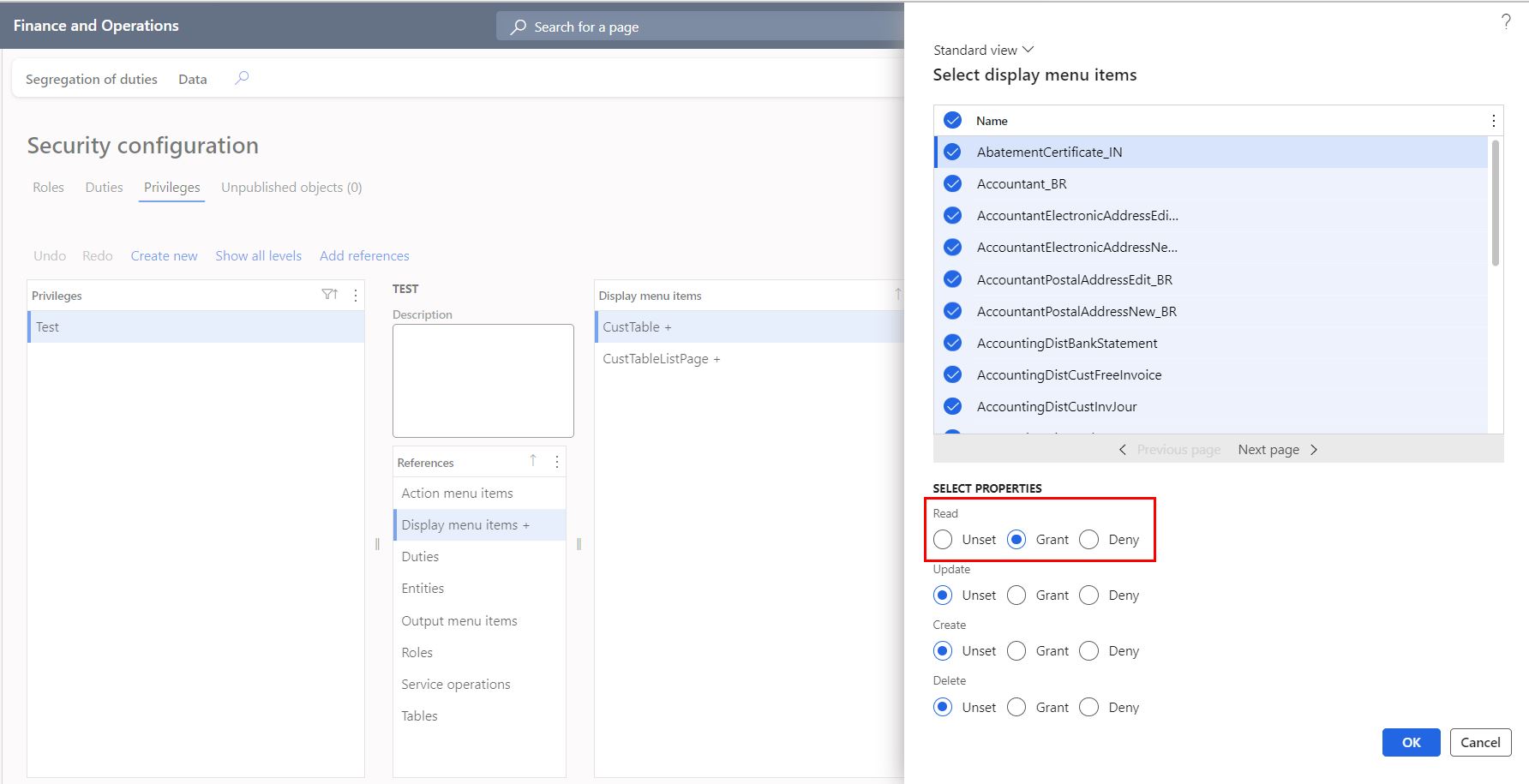
On the system administration page, assign securable objects to a privilege. Also, ‘unset’, ‘grant’ or ‘deny’ access to that securable object.
When creating a role, there are scenarios that may arise in which additional security types beyond the security object (e.g., user groups, table permission framework, etc.) are required to grant access. When creating a read-only role, it is important to validate that additional access is not being granted by these other security types. In addition, there are menu items that require greater than read access to be fully operational (e.g., the menu item “Sales and Marketing > Sales Orders > All Sales Orders > Open” requires edit access to be visible.). These are important to take into consideration when building security.
Creating read-only roles in Microsoft Dynamics 365 Finance and Supply Chain Management is a fundamental step to ensuring data security, compliance and operational efficiency. By granting read access while limiting write and delete permissions, organizations can strike the right balance between productivity and security. Implementing well-designed read-only roles can enhance transparency, streamline auditing processes and empower employees with the necessary insights for informed decision-making.
To learn more about our Microsoft consulting solutions, contact us.





