Every cybersecurity organization, through its program maturity journey, grapples with the challenge of choosing and aligning with a security framework. Frameworks provide structure, but also allow the organizations to evaluate their program internally, as well as against industry peers. Let’s take a closer look at some of the most common security frameworks used within the industry, including key considerations when selecting one and pitfalls to avoid.
NIST Cybersecurity Framework
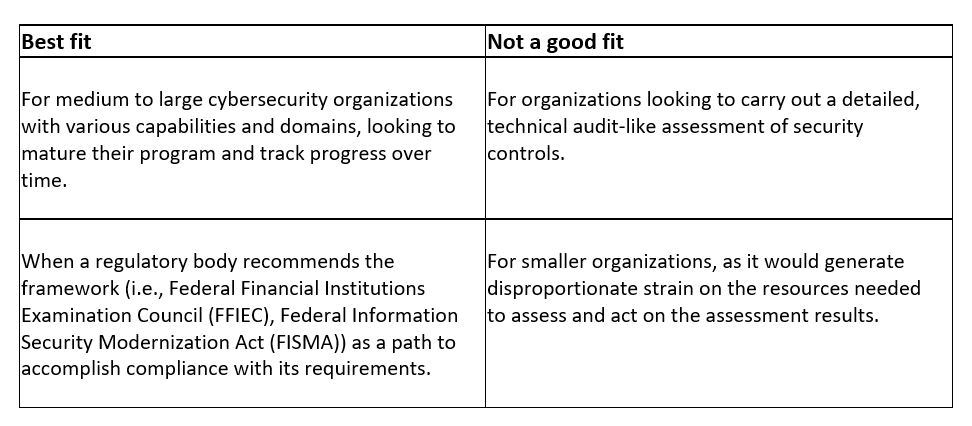
The NIST Cybersecurity Framework (NIST CSF) may be one of the most referred-to frameworks in the industry. Twenty-three categories are aligned to the five functions of this security framework: Identify, Protect, Detect, Respond and Recover. Each category includes subcategories, representing control objectives that together provide a foundation for a comprehensive cybersecurity program.
ISO 27001 by the International Organization for Standardization
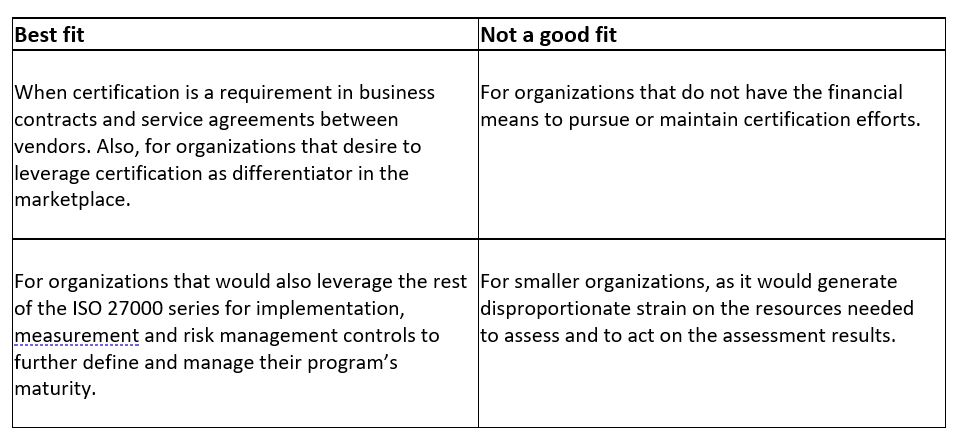
This security framework is most recognized due to the opportunity to certify compliance through an independent technical audit and prove that data protection standards have been achieved by the company. ISO 27001 divides its controls as: Organizational, People, Physical and Technological.
As an alternative to ISO 27001, organizations may pursue SOC 2 certifications as proof of independent security audits. The decision to pursue either is most often influenced by geography (i.e., ISO 27001 is more globally recognized than SOC 2) and contractual agreements.
The Center for Internet Security Critical Security Controls
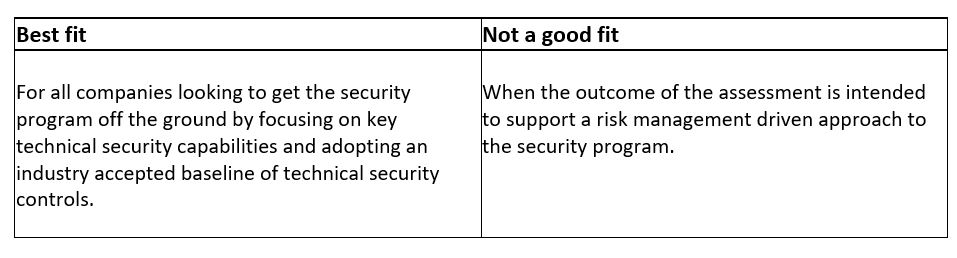
CIS Controls is a prioritized set of safeguards. The safeguards refer to controls that are technical in nature and are prioritized by three implementation groups that enable companies of all sizes to benefit. Large organizations can leverage the full extent of CIS Controls, while smaller security organizations with limited resources can begin by identifying a starting set of safeguards.
MITRE ATT&CK® knowledge base
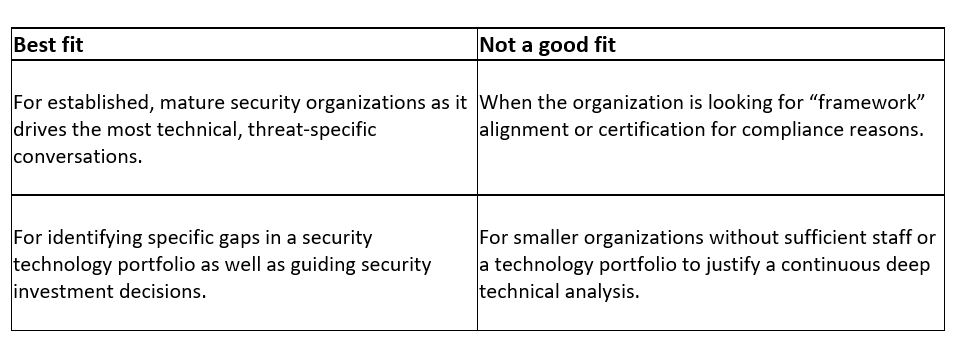
MITRE ATT&CK® is not a framework. Instead, it’s a knowledge base that security organizations should consider leveraging to mature their capabilities to address very specific, real-life threats from adversaries. MITRE ATT&CK® provides continuously updated technical knowledge from the attacker’s perspective.
Choosing a security framework, conducting a thorough assessment, prioritizing findings and driving initiatives is undoubtedly a resource-intensive challenge for any organization. Therefore, companies should consider the need from a variety of angles to select a framework that will provide the best value:
- Security program maturity – Is the program newly established with a relatively small team and broad functions or has it grown to have an appropriate level of staffing and technology? This may impact the appetite for in-depth assessments. Are the resources available to staff the effort and most importantly, drive action from the outcome of the assessment?
- Regulatory landscape – The industry, types of business processes and data types being processed can drive a list of compliance activities and required assessments. Understanding the external drivers will help select a framework that maximizes alignment with the requirements and derive efficiencies. For example, the Federal Financial Institutions Examination Council (FFIEC) provides a mapping of its requirements to the NIST Cybersecurity Framework.
- Expected outcome – this may be the most important element that an organization should answer. “What is the outcome we need to accomplish?” will be a key driver for this exercise. Is there a compliance issue? Is it a general need to understand the capabilities of the security program and the level of protection and risk mitigation it provides? Is it a regulatory activity? Is it to facilitate prioritization of the security program investments and/or build a security strategy?
Finally, common security frameworks bring the expertise of many industry professionals to a maturing security organization by defining a set of best practices for alignment and benchmarking. While there are many other security frameworks available (e.g. NIST 800-53, Secure Controls Frameworks (SCF), HITRUST), the ones covered in this blog have been adopted widely and leveraged often for establishing trust in a company’s data security practices.
Once a framework is selected, it is important to consider some important next steps as part of the process of adopting a framework:
- A framework assessment is not a complete and final solution to all security issues. Control framework assessments by themselves do not measure risk if all that is assessed is compliance or alignment with security controls. Controls are an important component in understanding how risks the organization is subject to are mitigated, but they do not paint a complete risk picture. To understand the risk exposure, a risk assessment needs to be performed that includes the identification of critical assets, threats, and vulnerabilities applicable to these assets and then applying the controls present in the environment to mitigate identified risks. The risk assessment should be performed in accordance with industry-accepted methodologies, like NIST 800-30, FAILR, Octave, etc., and will result in a prioritized list of residual risks for the environment. Once an assessment has been completed, it is time to prioritize findings, reflect the results in the organization’s investment decisions and continuously measure risk reduction as solutions are implemented.
- Educate the Board of Directors and/or executive leadership on the ratings and tiers of the framework selected before presenting the outcome of an assessment. There is a risk that the focus becomes earning a high score across the spectrum. In many cases, this is not reasonable to achieve or necessary based on the risk appetite of the organization. Leadership should understand how the framework is used as a tool to determine capability and enable maturity as opposed to simply being a scorecard. It is also important to demonstrate how the control maturity fits into the overall risk picture and the risk mitigation value provided by the controls in the environment.
- Think outside the box. Frameworks, while comprehensive in concept, may not have an emphasis on the company’s unique risk exposures. Encourage and allow flexibility. Deviations from the frameworks may be necessary to meet business, cultural and other constraints, or requirements of the environment.
- Don’t get complacent. Regularly re-evaluate the selected framework against business needs and external factors. Recognize that, over time, doing the same thing does not mean that ratings or tiers stay the same as well (in fact, they may deteriorate as the risk profile of the business or environment changes). Similarly, incremental improvements and ongoing investment may only result in sustaining previously assessed levels of framework capability and maturity. It takes meaningful effort to move the needle!
Build a cybersecurity strategy to drive long-term strategic value from the framework alignment. Don’t miss the opportunity to pair any assessment with a roadmap to achieve key security goals that align with the overall objectives of the business.
To learn more about our cybersecurity consulting solutions, contact us.





