Often, there exists the need to perform one-time and regular reviews of Identity and Access Management (IAM) health to answer some of the basic, yet critical questions security professionals care about:
- Who is entitled to perform what actions against what resources?
- Are there orphan identities?
- Am I granting service access to identities that do not utilize them?
Last accessed feature and need for automation
Luckily, these questions can be answered with AWS IAM’s last-accessed feature. This feature generates reports on when a user or role accesses a certain service and is turned on by default in the IAM console. View the last accessed data via user/role/policies panels and via the “access advisor” tab of the selected entity.
However, the default views provided in the AWS console can prove lacking when data needs to be aggregated and connected from different entities. For example, to ensure there are no rogue entities created on accounts, manual navigation through different AWS accounts will need to take place. Or, if an organization wants to understand if an associated policy can be deleted as part of a user/role cleanup, then navigation across multiple console views is necessary to obtain the full picture.
It would be much better if an automated process existed to aggregate all these data points and visually present them in a meaningful manner for security professionals and decision-makers to analyze and review.
AWS automation architecture
By leveraging last access APIs and other AWS services, the architecture below can help achieve such automation.
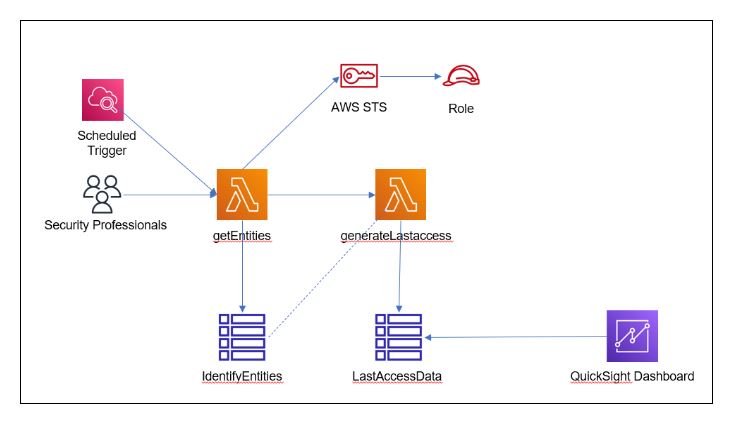
This automation can be triggered manually by a security professional, or by leveraging AWS CloudWatch to run the automation on a regular basis.
getEntities: This is the entry point of the process. The goal of the function is to retrieve all the identity entries and entitlements (users, roles and managed policies) within the organization. To do that, it will obtain a list of accounts within the organization, then work through the accounts to retrieve the identities, and finally store them within a DynamoDB table. It is important to note that, while this blog contains suggestions for managing identities, each organization’s needs will differ and Protiviti is not promoting these suggestions as best practices or processes for managing identities.
generateLastaccess: This function will traverse through all the entities retrieved from the previous step. For each entity, it will generate the corresponding last access report and store the relevant data within the LastAccessData table.
QuickSight dashboard: The data in the LastAccessData table will feed into AWS QuickSight, where data will be visualized and refreshed (this depends on how frequently the automation will be run).
Considerations
A few areas to consider as organizations adopt this architecture into their environment include:
- Last accessed limitations: Last access information is only available for Amazon EC2, IAM, Lambda, and S3 management actions such as creation, deletion or modification. Additionally, the tracking period is limited to the last 400 days and new activity will generally appear within four hours. The last accessed information is also limited to the standard AWS regions. To see what regions are tracked and when they were added, visit Where AWS tracks last accessed information.
- Lambda limitations: The getEntites function generates a list of all identity entities while the generateLastaccess function iterates through all accounts to generate last accessed information for those accounts. It is important to keep in mind Lambda limitations, such as timeout at 15 minutes and resources used to run and store the functions.
- Architecture cost: Can vary based on the number of accounts and identity entities in the environment. Another factor to consider is the frequency with which the architecture is run.
- AWS organizations: The architecture can be further expanded to include last access information on the AWS organization level, which includes entities such as organization root, organizational units (OUs), accounts and service control policy (SCP).
Implementing the last accessed architecture will help keep track of user activity on applicable AWS services. It will help to maintain an inventory of entity actions, identify entities with more access than necessary and track inactive entities. This can assist with user access reviews and segregation of duties, which are important in making sure to keep an organizations AWS environment secure from bad actors.
Automating AWS processes, like the IAM review process, improves efficiency, reduces human error, and ultimately, secures your AWS environment. However, not all processes can or should be automated. Protiviti has the expertise to help organizations identify the key areas within AWS that are candidates for automation, and to implement such automation to maximize efficiency.
Chris Flesher and Jeff Conner, Directors – Security and Privacy, contributed to this post.
To learn more about Protiviti security and AWS consulting services, contact us.






