Encryption is a topic that many people easily recognize the importance of, but often fail to appreciate the complexity around it. And complexity only increases when enterprises shift to a cloud environment because cloud services options are expanding at an exponential rate. To provide a bit of clarity, we’ll break down what encryption is, describe the different methods of encryption, and explore how encryption can be applied in Amazon Web Services (AWS).
What is encryption?
Encryption is the process of scrambling data and making it unrecognizable, so only those with access to the correct decryption key can read it. This makes it harder for bad actors to decipher and understand data and offers organizations a layer of security that ensures information is accessed by the individuals meant to receive it. AWS offers a variety of services to aid organizations in making the right choices for their encryption needs.
Before diving into how AWS encrypts data, we should first clarify the difference between encryption at rest and encryption in transit.
- Encryption at rest is, to some degree, very straightforward as data is encrypted while stored in the server or mobile device. It is important to be able to decrypt when attempting to retrieve the data.
- Encryption in transit is much more complicated and deserves closer examination. Within the TCP/IP model, encryption is typically applied at the application layer, the internet layer (generally referred to as the network layer), or both.
Illustration of common encryption technologies and mapping against the TCP/IP model
Application versus network layer encryption
When applying encryption at the application layer, only the application data is encrypted — a typical example is the https protocol. The advantage of this is that end-to-end encryption can be achieved from the client to the target server. The downside is that the IP and transport information are still visible. In some cases, hackers can decipher the encrypted application message by analyzing the data and pattern of the network/transport data. 
Illustration of application layer encryption infrastructure
When applying encryption at the network layer, all the data from the network to application layers are encrypted — a typical example is IPsec. The advantage here is that data is encrypted in the network and transport layers. In practice, however, the downside is that it does not provide end-to-end encryption (as depicted in the diagram below).
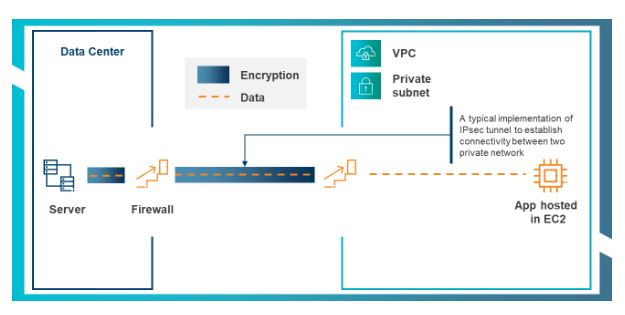
Illustration of network layer encryption infrastructure
Best practice is for an organization to properly evaluate its use cases, considering factors such as criticality, location, consumers, performance, etc. to determine the most appropriate encryption approach to protect the data. In some cases, organizations may leverage both methods to secure data traffic.
AWS encryption services
With that context in mind, AWS offers several services that customers can utilize to apply encryption and to validate that encryption is in place. The boxes shown in blue (light & dark) are services the customer must purchase and configure, while the services in black are available to the customer by default.
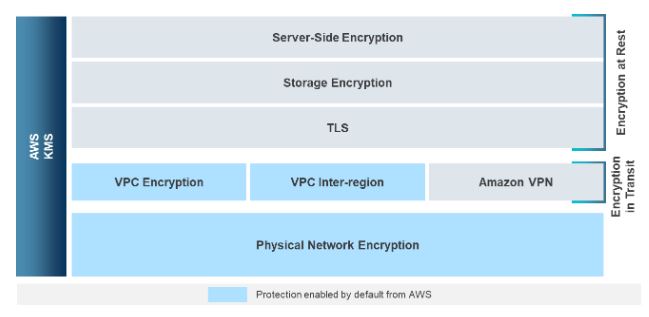
Illustration of encryption stack in AWS; Source: AWS Re:Inforce 2019
Encryption at rest is a feature that can be turned on across all of AWS’ services (e.g., EC2, S3, EBS volume, RDS instances). When enabled on a particular AWS service, the service leverages AWS Key Management Service (KMS) to generate the required key to encrypt the data.
Encryption in transit can be achieved in different ways depending on the requirement. It can be broken into two broad methods as described in the section above: application layer encryption (TLS) or network level encryption (Amazon VPN).
- TLS: for client-server architecture, which can be achieved through services such as CloudFront, Elastic Load Balancer & AWS Certificate Manager.
- Amazon VPN: site-to-site VPN establishes an IPsec tunnel between a customer gateway and the organization’s logical VPN gateway in AWS. This effectively establishes connectivity of services within two private networks without exposing them to the public internet.
Encryption in transit default is network and network access level encryption that AWS provides by default. Customers gain the benefit of the encryption by utilizing related services.
- VPC encryption: traffic between certain types of EC2 instances within the VPC are automatically encrypted.
- VPC inter-region: traffic between two VPC peers that are in different regions are automatically encrypted.
- Physical network encryption: any traffic that travels between AWS datacenters and locations is automatically encrypted.
AWS KMS is the key storage and management service that makes encryption activities easier in the AWS environment. Customers can use the key generated by AWS in KMS, or customers can bring their own key to be stored in KMS. Regardless of which option is used, it is important to ensure resources only have access to the keys they need, and key hygiene (i.e., key rotation) is being maintained.
Regardless of what type of encryption is employed, enterprises should establish a process to validate that encryption is in place. Fortunately, such validation processes can be automated through AWS Config, which reports what services have enabled or disabled encryption, as well as identifies insecure traffic within the VPC by thoroughly examining Virtual Private Cloud (VPC) flow logs. With validation, a feedback loop can be established to ensure data is being protected and that security and compliance standards are being adhered to. Protiviti can help guide organizations in implementing these components based on their needs and further implement solutions to improve AWS security.
To learn more about Protiviti security and AWS consulting solutions, contact us.