The past 18 months have seen a significant increase in threats targeting critical infrastructure and operational technology (OT) networks. These environments are prime targets due to their age, complexity and importance to organizations. OT is the driver behind the largest corporations in the world – whether it is mixing the secret recipe for Coca-Cola, generating power for millions of customers, or producing lifesaving medication for millions of patients. For large corporations, a disruption in the OT network can easily cause millions of dollars of lost revenue per hour. It’s no wonder companies like JBS Foods, Colonial Pipeline and Brenntag paid a combined $19.8 million in ransomware payments to regain access to their OT networks and restart production. These are just three examples readily available in the public domain, with general agreement among security professionals that the amount not publicly disclosed is likely staggering. These surely include multi-million-dollar breaches and ransomware payments that have not been publicized.
Given the potential for lost revenue, harmed reputation and regulatory fines – companies are scrambling to find ways they can easily secure their OT security programs at scale. The natural desire is to find the fastest, most efficient and effective way to achieve “security.” This desire for a “silver bullet” is further complicated for multi-national global organizations that have vastly different OT network architectures, varying technology stacks, an abundance of opportunities for shadow IT, limited OT network visibility, and dozens of primary languages, cultures and politics to navigate. Any attempt to measure the residual risk of an OT Program for a cyber insurance provider or board of directors sounds like a monumental task. Further, where does one even begin to prioritize risks and compare locations against each other to identify trends and share best practices? In this blog post, we will identify a proven four-step approach for large, complex organizations to begin measuring their OT Security Risks across multiple sites.
Step 1 – Define the risk management framework
A risk management framework (RMF) allows organizations to use a risk-based approach to review business values and risk tolerances to create processes that integrate security controls into an organization’s OT sites and networks. This risk framework should align with the OT Security policy. This framework should define risk indicators for a site and have security control requirements that are scaled by the relative risk of the site. Work with counterparts to understand how business value is defined for production sites – Is Site One a critical path in the supply chain to produce materials at other sites? Does Site Two have a proprietary formula that must be protected at all costs, whereas Site Three has processes that are publicly known? Does Site Three have delivery contracts where the company must provide all the product or be financially responsible for the entire shipment? Additional indicators of risks impacting business risk calculations could be business value, supply chain impact, the connectedness of site equipment, geography, the product manufactured, revenue, and regulatory considerations. Each company is unique and may have confidentiality, integrity and availability constraints that differ wildly across the sites. Securing buy-in from senior stakeholders at the outset is paramount to acquiring resources, funding, and support for enhancing the resiliency and safety of OT sites.
Step 2 – Outline the control set
Define OT security controls to measure sites against industry risks, external frameworks, best practices and the ability for the program to execute. Given the delta between an organization’s readiness to implement and the risk profile of OT security sites, it is highly recommended to have a consistent baseline of controls that map to industry standards (i.e., IEC 62443, NIST 800-82, TSA Security Directive 2) and levels of required controls based upon the regulatory and risk landscape of the OT sites. For example, the highest revenue-producing site where availability is the top concern should have higher requirements for resiliency, redundancy of hardware and backups in place. Selecting OT security controls is an important process that balances the need to secure critical organizational assets while avoiding adverse impacts to operations or the health and safety of personnel on-site. OT security controls should be defined in an organizational OT security policy and allow flexibility to meet the needs of OT sites that have different threat profiles. There should be a process to handle policy exceptions with considerations for technical feasibility issues, where the technology cannot meet a control and the focus needs to be on mitigating controls to reduce risk.
Step 3 – Measuring site-level maturity
Measure compliance of OT sites against defined controls and prioritize residual risk based upon the likelihood of compromise and impact on the organization’s operations (leveraging the risk framework from Step One) considering the mitigations in place. Organizations need to develop a repeatable process for gathering risk information and measuring results. It is recommended to use a consistent set of questions to assess OT sites against a common set of controls that maps back to an industry standard. Over the past 5 years, we have seen greater adoption of the NIST CSF Framework, since it is helpful in communicating the results of maturity across multiple sites in a concise manner and leverages a consistent set of controls. One of the most difficult challenges with managing risks across multiple OT sites is prioritizing resources to efficiently reduce organizational risk and gathering funding to address the issues. Maturity comparisons of site-level security across risk characteristics like geography, product and revenue can help drive remediation activities.
Step 4 – Socialize results
Socialize OT security metrics in an impactful manner to gather support on resourcing and remediation of residual program risks. When discussing OT security risks with executives, highlight the potentially unfavorable business outcomes that may arise from residual risks (financial loss, health and safety impacts, reputational harm). PowerBI Dashboards, like the one below, can be a great visual aid for gathering buy-in from top organizational leaders to secure funding while ensuring OT sites meet baseline expectations. We have multiple clients in complex organizations that have seen tremendous benefits in adoption of security processes and reduction of risk when they leverage site-specific metrics to foster a healthy competition between business unit VPs.
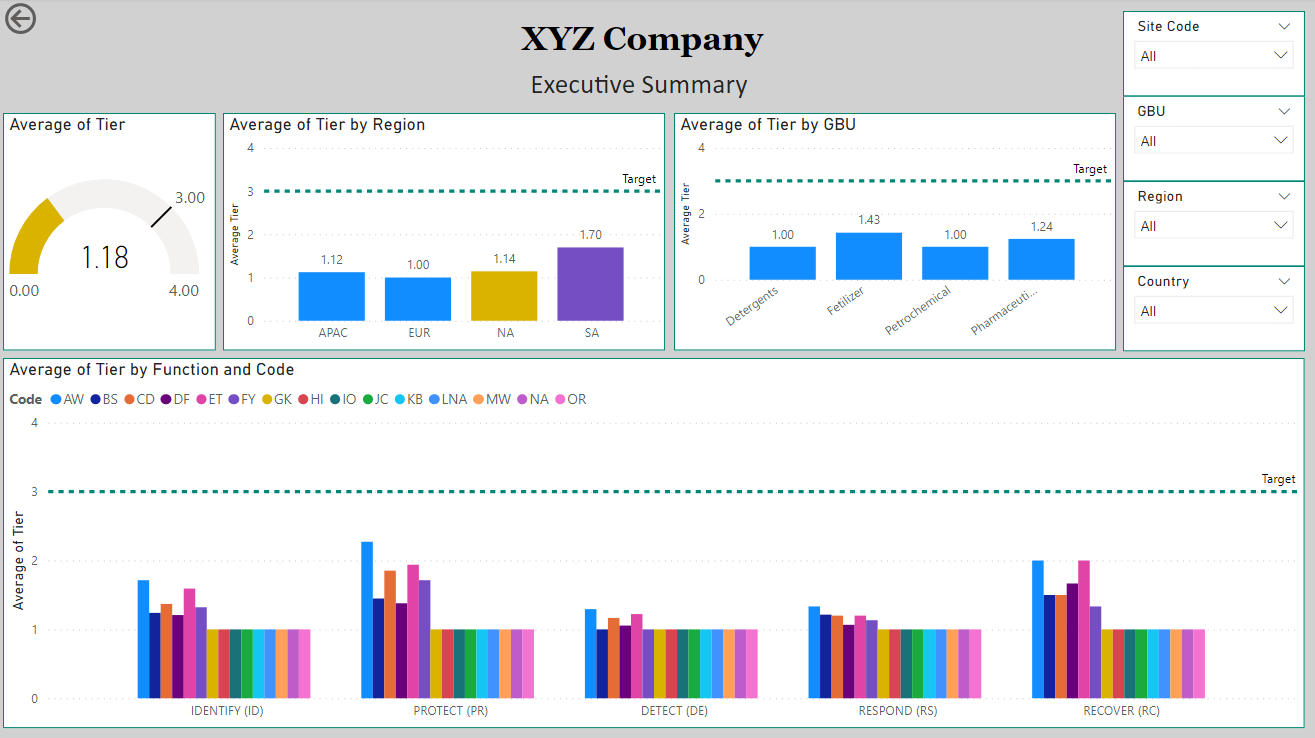
Managing OT security risk at scale is challenging for many organizations. The key is to appropriately identify risk and align resources to reduce organizational risks, that could impact the health and safety of personnel on-site. Protiviti’s phased approach is proven to align internal stakeholders on an approach to measure and prioritize risks, while also gathering the needed support funding and resources to mitigate risks, while improving the resiliency of your OT program.
To learn more about our security consulting services, contact us.





