Every day, clients come to us with questions about ransomware and how to best prepare their organizations against potential attacks. This is perhaps one of the most vexing challenges in cybersecurity as ransomware attack methods, motivation and barriers to entry are constantly evolving. We’ve collated three key questions that concisely explain ransomware:
- How do these attackers target my organization? Ransomware attacks are a business unto themselves and if an organization displays a lack of defenses, it is likely to become a victim. Organizations that do not adapt and change run the risk of fostering attacker innovation.
- Why have these attacks grown? It’s a vicious cycle. Attacks are funded by victims, enabling attackers to innovate and develop the next generation of attack method and technology, targeting the complex and difficult security elements that are not quickly or easily fixed. The cycle will continue as long as the attacker sees an opportunity to profit.
- What happens to my organization when an attack occurs? Files with critical business information and systems become unavailable. Sensitive data is exposed, regulators demand answers. Legal disputes can go on for years. Paying a ransom does not mitigate the damage and may encourage a return.
Anticipate, respond, recover
An active defense – including assessment exercises, threat hunting and tabletop exercises – can improve any organization’s ability to quickly react to evolving threats. Ransomware attacks require companies to focus on anticipating the attack, responding when it happens and recovering and updating business controls to help prevent future events.
- Anticipate: Understanding the threat landscape to gain insight into potential threat vectors that can impact a company’s weak control areas is vital; this requires external sensing, an active defense posture and continuous risk analysis.
- Respond: The crisis management approach coordinates the entire enterprise to respond to a ransomware attack. This includes executive, legal and technical functions.
- Recover: This is more than just the resumption of operations. Decisions made during the crisis can have long-lasting impacts on recovery efforts. Steps to prevent recurrence can add to the length and cost of recovery.
Attackers are growing more sophisticated and treat their work in much the same business manner most organizations do. They are hiring developers and business analysts, developing more sophisticated “marketing” techniques such as phishing emails and growing more sophisticated in recruiting the global skillsets needed to stay ahead of the cyber controls and investments that organizations are working hard to put in place. With attackers constantly innovating, they are unlikely to use the same attack vectors twice. Organizations need to build a recovery plan that can adapt to the known and unknown vulnerabilities, to minimize their risk when an incident occurs.
Cyber risk quantification
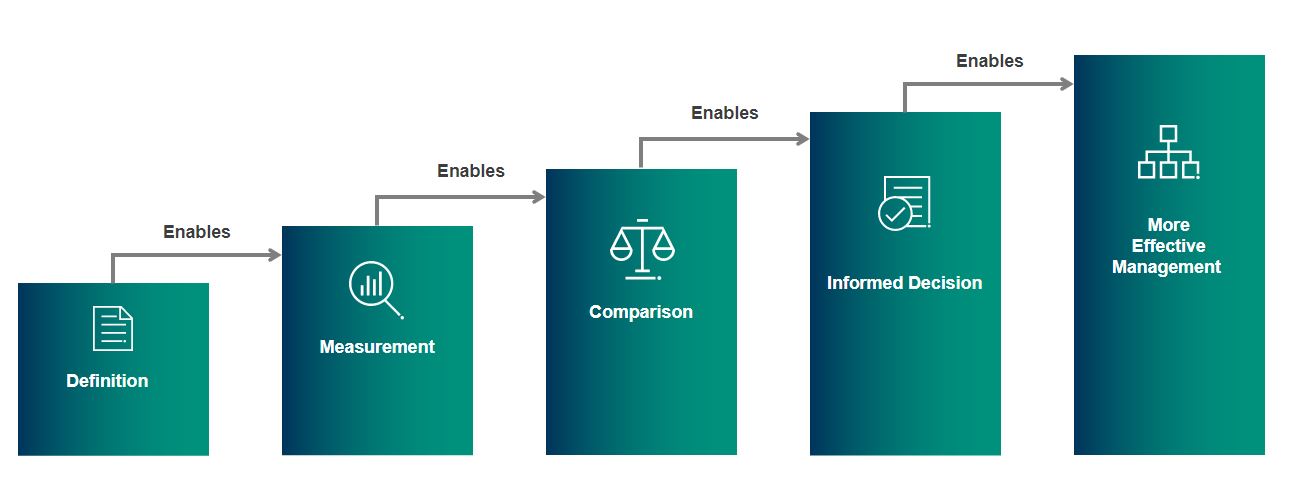
The best offense is an active defense. With so many different attack types and an ever-changing risk landscape, effectively prioritizing investments in defenses can be a significant challenge. Quantifying the risk of a ransomware event can help determine where rational investments can be made and falls under the “Anticipate” step of an advanced ransomware detection approach. Consider the above graphic, which illustrates how risk quantification can be a useful tool in deciding where to allocate resources to get the most impactful risk reduction. Simple, cyber risk quantification translates risks into financial terms – a concept an entire business can understand.
We apply risk quantification techniques by identifying risk scenarios and the ways that can result in loss to an organization. Using open-source models, we can then forecast loss to an organization from a number of different ransomware threats.
Ultimately, quantitative risk management allows an organization to understand its risk in financial terms, which in turn enables a clear prioritization of actions to be taken. We believe one of the most powerful arguments for quantitative vs. qualitative risk assessments is the ability to compare different investments to identify what future mitigating measures will most effectively reduce the most loss exposure per dollars invested.
Case study: quantifying a ransomware event
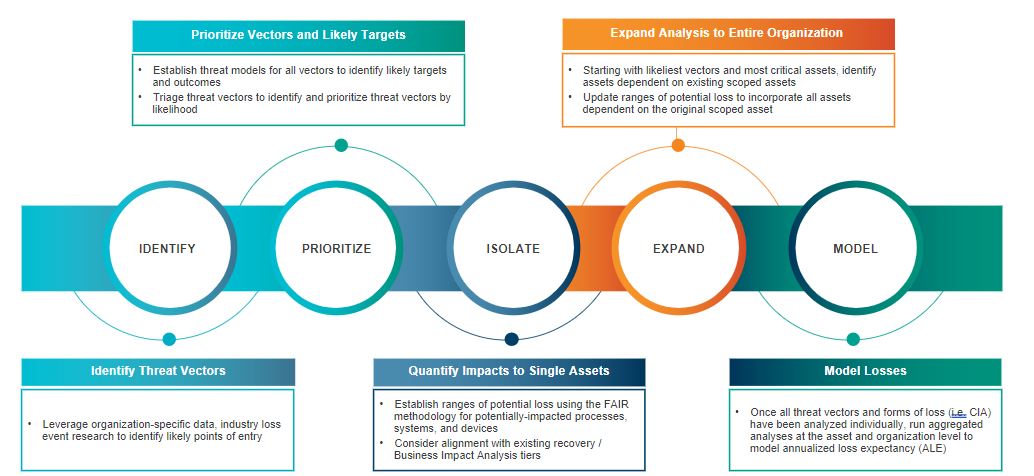
Quantifying risk in an anticipated ransomware event provides a business reason to invest in cyber security and cyber resilience. Quantification replaces open speculation with a methodically sound and repeatable model of risk and impact. We recently released a case study in which we performed a quantitative risk analysis specific to a ransomware attack on a fictional large financial institution. This case study demonstrates how a tried-and-tested method of risk quantification can be deployed to analyze ransomware risk that may involve multiple types of loss events, as ransomware can spread beyond a single system or type of loss. Through this detailed analysis, we estimated this fictional $80 billion bank’s average annual exposure to ransomware to be $10.2 million and its per-event loss to be $48 million at minimum and $266.3 million in the worst-case scenario (90th percentile). Ultimately, the insights identified through our analysis will allow this fictional bank to determine its potential maximum disruption from a ransomware attack, assess whether or not current operations can withstand such an impact and make critical decisions to drive meaningful change.
In order to perform this type of analysis, we consider the effectiveness of the organization’s perimeter security controls and the results of their mock phishing exercises to help construct data that demonstrate how likely the organization is to be attacked. Ultimately, someone’s going to download something they shouldn’t, but effective controls in place can affect the loss event frequency or the likelihood of a further compromise that we can use in our analyses. Once we have identified the most likely initial loss event, we can model potential downstream affects and other losses that could occur.
Every potential event creates a downstream effect that we map out as part of this process, looking at a minimum, most likely and a maximum impact. The detailed case study provides more information about our processes, and we encourage everyone to download a copy.
Remediation creates a sustainable future
A ransomware attack is not a single, discrete event. Someone has gotten in, launched ransomware and/or stolen data. This is an intelligent, human-driven attack that automated tools often have a hard time stopping. Cybersecurity control weaknesses that are impacted by a ransomware attack can cover many areas of a business. In order to fight back, organizations must have an active defense plan that includes proactive assessments and regularly scheduled simulations. We strongly recommend using a risk quantification tool to get the most impact from the defense plan, while securing buy-in across the business for security effectiveness.
More specifically, we suggest these remediation steps to create a sustainable future for any organization:
- Define incident response governance procedures
- Quantify the risk for a ransomware event to enable better decision-making
- Improve security controls managing end-user and admin access to company resources
- Ensure robust vulnerability management practices are utilized
- Establish an active, continuous monitoring program for security events
- Confirm digital identity access rights and corresponding controls
- Assess the organization’s response readiness to deal with the next attack
Ransomware is complex but preventing it doesn’t have to be.
To learn more about our cyber risk quantification, ransomware, and other cybersecurity consulting solutions, contact us.






