The fourth industrial revolution, known as 4IR or Industry 4.0, is in full swing. It focuses heavily on automation, interconnectivity of devices, machine learning and real-time data. The intersection of 5G and edge computing technologies are core components of Industry 4.0 and are expected to reinvent industries, change the way security is implemented and revolutionize business operations. Understanding how 5G and edge computing impacts use cases and changes the approach to security will prepare organizations for this quickly approaching new era.
What is Edge Cloud computing?
Readers are likely familiar with the concept “cloud computing”, which is the delivery of computing services such as servers, databases, software and much more over the internet to offer faster innovation, flexible resources and economies of scale. A newer concept that has gained popularity the past few years is “Edge Cloud.” Edge Cloud computing places resources closer to the user device (or at the “edge” of the network) rather than in a cloud data center that may be miles away. Edge Cloud is transforming the way data is being handled, processed and delivered. Most cloud service providers, such as Azure, Amazon Web Services and Google Cloud Platform have released their cloud-to-edge capabilities to expand the cloud network.
Faster networking technologies, such as 5G, allow for Edge Cloud systems to accelerate the creation or support of real-time applications, such as video processing and analytics, self-driving cars, artificial intelligence and robotics. While early goals of edge computing were to address the costs of bandwidth for data traveling long distances, the rise of real-time applications which require processing at the edge is driving the technology ahead.
What is 5G?
5G, or fifth generation technology for broadband cellular networks, is the successor to 4G. 5G provides network capabilities, increasing bandwidth and lowering latency to provide faster internet speeds for mobile devices and improve connectivity and reliability. 5G networks can be used in three main ways:
- Enhanced Mobile Broadband (eMBB): Increases the rate at which data is transmitted and is beneficial for high-traffic services such as Augmented Reality (AR) and Virtual Reality (VR).
- Ultra-Reliable Low-Latency Communication (URLLC): Reduces data transmission latency (delays) and is beneficial for remote technologies like self-driving cars.
- Massive Machine‐Type Communication (mMTC): Supports several base station connections concurrently and is beneficial for developing Internet of Things (IoT).
5G was created to primarily benefit the corporate and public sectors as it is aimed to solve a lot of the issues with mass consumption of data and increased use of mobile devices within businesses.
Drawing the parallel: The 5G Edge
Using Edge Cloud is the only way that 5G will meet latency targets that have been set. Latency, which is defined as the time it takes for data from a device to be uploaded and reach its target, is predicted to drop from 50ms to 1ms with the transition from 4G to 5G. For many applications, 5G and Edge Cloud will be needed for optimal performance. For data-heavy applications, sending data constantly back to the cloud will be expensive even with 5G. However, with the use of Edge Cloud, data can be cached, analyzed, and filtered, sending only what is necessary back to the cloud (see Figure 1).
For businesses, lower latency will make cloud services and applications more responsive and capable, which means there will be reduced employee downtime and almost instant access to the files and information that workers depend on daily. Businesses that rely on collaboration solutions to communicate internally and with customers will experience seamless video conferencing and client presentations will not lag in communications. The use of 5G with Edge Cloud, also known as the “5G Edge,” will improve resiliency, provide real-time interaction and deliver a better user experience.
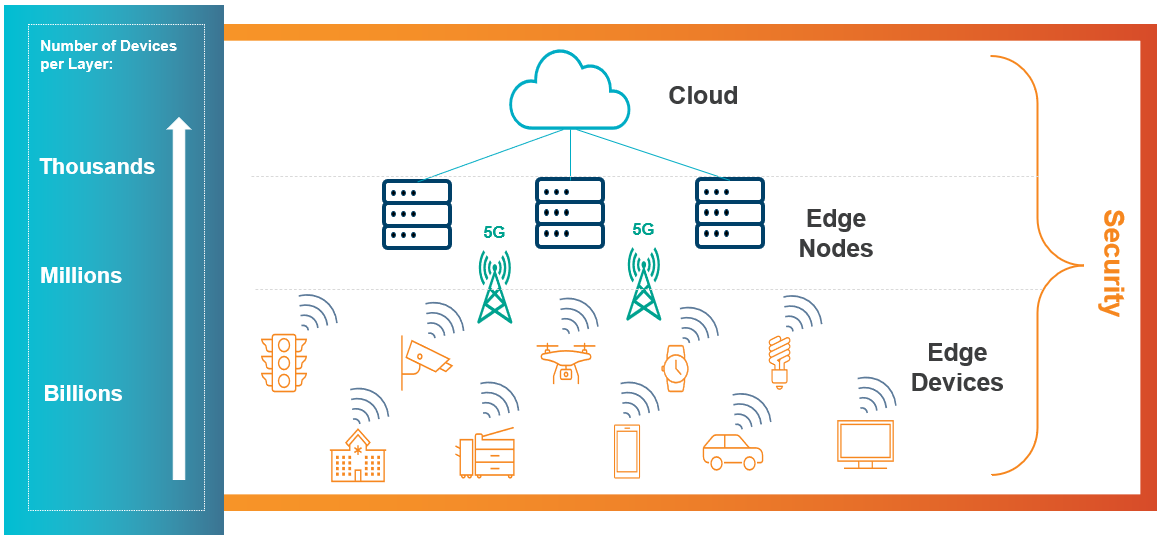
5G and edge computing security diagram
Security implications
Security use: Retail
The retail industry will be transformed with the rise of 5G and Edge Cloud. Retailers will be able to engage with customers in new ways by using AR and VR. For example, using AR and VR, retailers can guide a consumer through a physical store to the exact location of a product of interest. Also, using IoT-embedded sensors, retailers can have a real-time view of their stock, leading to faster response and restocking times.
As with any new technology, there are new security issues to be addressed. One security implication is that because the number and types of devices on the network will continue to increase, a larger attack surface will be created. Additionally, retailers may not have resources to manage the life cycle, security and data policies of these new devices on their network. Therefore, organizations will have to develop methods to test and evaluate the embedded systems and firmware in these IoT devices to understand the relevant cyber risks.
Security use: Healthcare
Another use case for 5G and Edge Cloud is in the healthcare industry. Massive amounts of data are constantly being generated in healthcare which are often not used due to outdated or legacy network architectures. The 5G Edge can accelerate the growth of developments through real-time information exchange enabled by low latency. As one example, this means collecting data through cameras and sensors will be easier to analyze. As such, when monitoring a patient’s vitals in the hospital or tracking daily health statistics (via wearable technology), healthcare providers can receive alerts about meaningful health changes.
Some security challenges to consider in the healthcare industry are vulnerabilities in the edge devices (e.g., cameras and sensors) resulting from the increased number of connections and bandwidth being used. Additionally, data security protocols and policy enforcement (e.g., VPN and IP access) will require regular monitoring and maintenance to ensure patient data confidentiality. Before implementing any new software or technology it is important to evaluate all the risks involved and confirm organizations are prepared to address those risks.
Prepare for 5G and Edge Cloud
To get started with 5G and Edge Cloud, we suggest the following:
- Step 1: Understand how it impacts the business. Start scoping the current environment and understand how it is set up by conducting interviews with stakeholders and performing a security risk assessment. Gain an understanding of how the 5G Edge can benefit the business and document the existing use cases. Once 5G Edge use cases are documented, move on to the next step.
- Step 2: Build and design the 5G Edge architecture. Based on the previous step, start developing the future state architecture by keeping data security top of mind, considering management as systems scale, and increased innovation. Make sure to note what a successful implementation looks like.
- Step 3: Explore the different 5G Edge vendors. There are a variety of vendors offering 5G Edge solutions. Explore which one is the right one for the business, and make sure it meets business and security needs as well as the use cases you came up with in Step 1.
Although 5G and Edge Cloud can stand on their own and function separately; together, they create a force that will change business operations and security of currently siloed and underutilized edge devices. The intersection between Edge Cloud and 5G will allow rapid decision-making, which will impact organizations desiring to maintain their cutting edge. It will also impact how edge devices are managed and secured based on the use cases. Organizations should prepare for these inevitable and upcoming changes, which will be rapid and impacting.
To learn more about our cloud security consulting services, contact us.






