In a previous blog, we covered the importance of information protection and how Microsoft Information Protection (MIP) can help organizations address new and emerging compliance and privacy requirements, such as the General Data Protection Regulation (GDPR). More specifically, that blog discussed the comprehensive set of capabilities that MIP provides to help protect sensitive data throughout its entire lifecycle – across devices, apps, cloud services, on-premises and Microsoft 365 (Exchange Online, Teams, OneDrive).
MIP sensitivity labels
MIP provides a framework for products and integrated capabilities that use the same labeling store (unified labels) and helps protect the organization’s sensitive information. MIP addresses business concerns regarding data protection by creating safeguarding controls and measures for the document at the file level. Utilizing a sensitivity label, organizations can ensure their users and partners are aware they are working with sensitive data by automatically marking the document or email with a header, footer, and/or watermark. In addition to this content markup, a sensitivity label can protect the data by applying encryption directly to the document itself. This encryption is applied to the content directly and is not dependent on the location in which it is stored. In fact, if an encrypted document leaves the organization’s environment, the individual attempting to open the file outside of the organization will not be able to view the content without the appropriate credentials and permissions.
As described in this blog from Microsoft, sensitivity labels from the Microsoft Information Protection solution work to classify and protect an organization’s data, while making sure that user productivity and their ability to collaborate aren’t hindered. Sensitivity labels can be used to:
- Provide protection settings that include encryption and content markings. For example, apply a confidential label to a document or email, and that label encrypts the content and applies a confidential watermark. Content markings include headers and footers as well as watermarks, and encryption can also restrict what actions authorized people can take on the content.
- Protect content in Office apps across different platforms and devices. Supported by Word, Excel, PowerPoint, and Outlook on the Office desktop apps and Office on the web. Supported on Windows, macOS, iOS, and Android.
- Protect content in third-party apps and services by using Microsoft Cloud App Security. With Cloud App Security, you can detect, classify, label, and protect content in third-party apps and services, such as Salesforce, Box, or DropBox, even if the third-party app or service does not read or support sensitivity labels.
- Protect containers that include Teams, Microsoft 365 Groups, and SharePoint sites. For example, set privacy settings, external user access and external sharing, and access from unmanaged devices.
- Extend sensitivity labels to Power BI. When this capability is turned on, labels can be applied and viewed in Power BI, and data protected when it’s saved outside the service.
- Extend sensitivity labels to assets in Azure Purview. When this capability is turned on, currently in preview, sensitivity labels can be applied to assets such as SQL columns, files in Azure Blob Storage and more.
- Extend sensitivity labels to third-party apps and services. Using the Microsoft Information Protection SDK, third-party apps can read sensitivity labels and apply protection settings.
- Classify content without using any protection settings. Simply assign a label as a result of classifying the content. This provides users with a visual mapping of classification to the organization’s label names and the labels can then be used to generate usage reports and see activity data for sensitive content. Or, choose to apply protection settings later.
In all these cases, sensitivity labels in Microsoft 365 can help users take the right actions on the right content. Use sensitivity labels to classify data across the organization, and enforce protection settings based on that classification.
Problem solved: encrypting MIP label missing in the sensitivity drop down
Recently, we encountered an issue with a client running an MIP pilot who experienced an encrypting MIP label missing the sensitivity drop-down options within Office Client Apps. All other labels were there (public, internal, confidential, etc.), including the labels that were configured to encrypt. The only one missing was the restricted label. This label was also encrypted, but unlike the confidential label, which had the encryption groups configured on the label itself, the restricted label allowed users to set the encryption themselves. Keep in mind; this is expected behavior when working on the web version of Office, where any label that prompts users to set permissions is not currently supported. In this case, however, we were using the standard Office 365 client.
Possible causes to consider
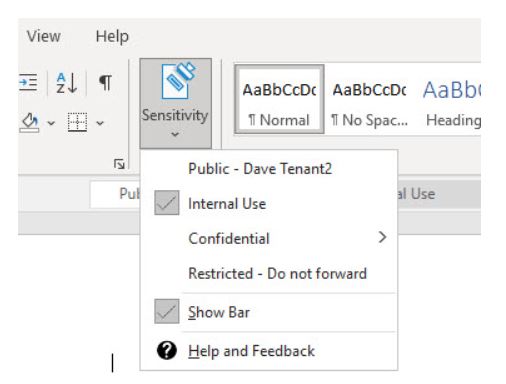
There are certain situations where this type of label will not show up in the sensitivity button.
As mentioned above, Office online versions (including the interface in Microsoft Teams) are not currently supported.
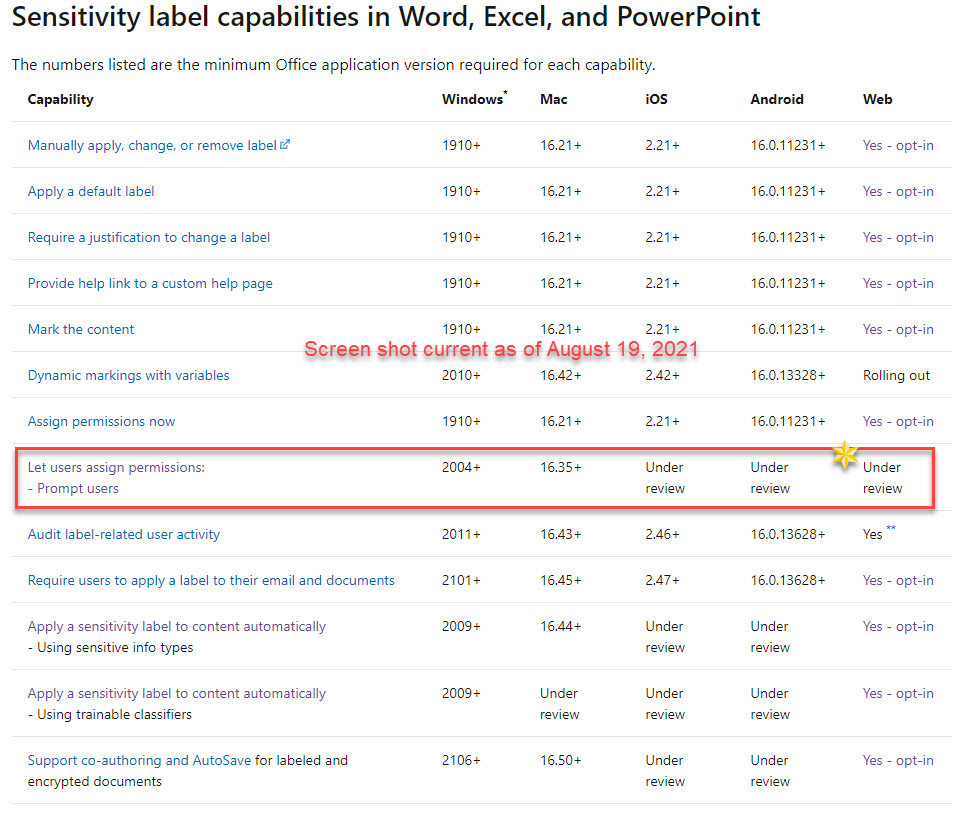
Looking at the above screenshot, notice that assigning permissions is dependent on the version of Office being used (2004 or newer required).
Ruling out Office as the culprit
As mentioned above, if the version of Office is prior to version 2004, a user-configured, encrypting MIP label will not show up in the drop-down. To get around this, if it is not possible to update Office, install the MIP Unified Labeling Client (AIP Unified Labeling Client). At this point, the MIP client takes over the options in the Office app, enabling the user to set the encrypting label. In our case, though, this did not work. To ensure that Office is indeed not the culprit, select a file on a workstation, right-click and select classify and protect.
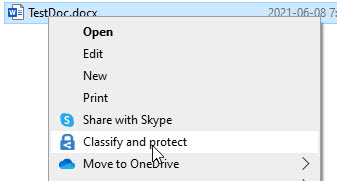
This process opens the MIP Client without interfacing with Microsoft Office. If the problem is something other than the existing version of Office, then the encrypting MIP label will be missing here, too.
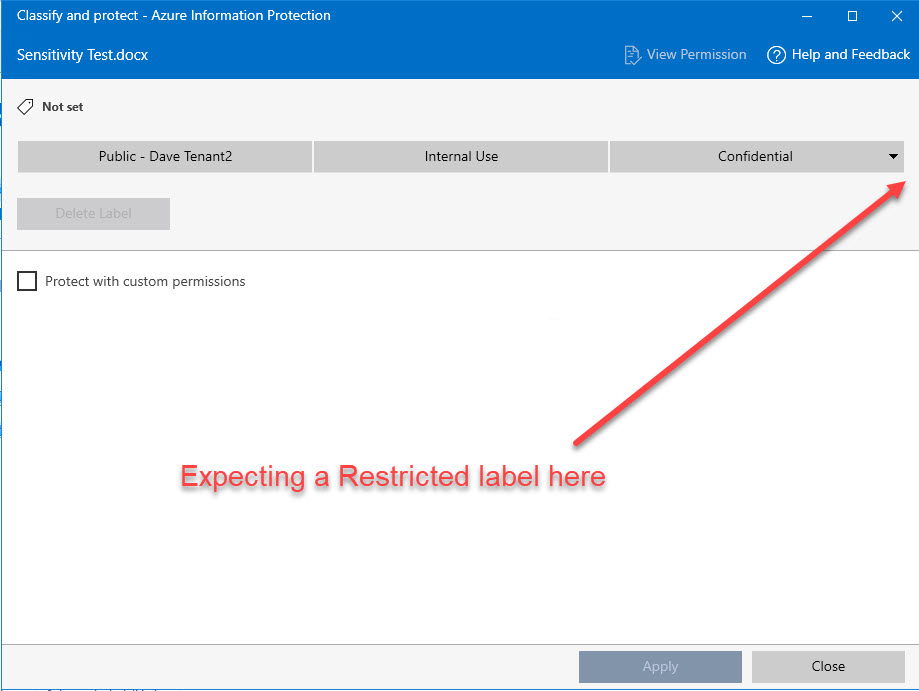
The solution
The culprit is an option on the MIP label that should have nothing to do with the issue observed. When configuring the label to allow users to set the permissions, Microsoft 365 provides some options around Outlook and Word, Excel and PowerPoint. These options are separated to provide a different experience between Outlook and other Office apps. Within the Outlook options, an administrator can select either to enforce “do not forward” controls or to just allow the label to encrypt the email. In our case, we had the second option (encrypt-only) enabled. This option, which should have nothing to do with the MIP client or Microsoft Office client integration, caused the encrypting MIP label to be missing in the sensitivity drop-down issue.
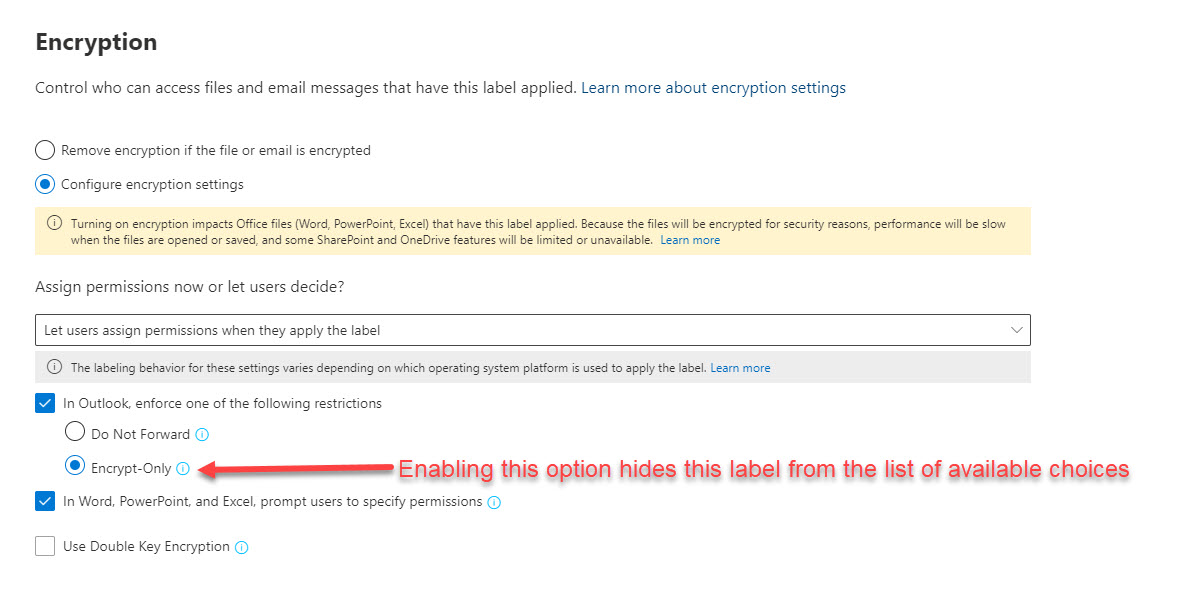
Changing the option to do not forward and saving changes will have the label showing up again. Note: It may be necessary to reset the MIP configuration on the workstation.
With the immense growth of data and an increasingly mobile workforce, the question is not whether Information protection needs to happen, but what is the best way to make it happen. Microsoft Information Protection sensitivity labeling helps organizations protect sensitive data throughout its lifecycle by applying sensitivity labels that are linked to protection actions like encryption, access restrictions, visual markings and more.
To learn more about our Microsoft consulting solutions, contact us.