What drives cybersecurity spend and budget decisions? Too often, the reasoning behind these decisions is reactive in nature, rather than proactive. Often, CISOs see budget increases following a breach at their organization or in response to what is happening to industry peers. While this is not inherently negative, fear should not be the primary driver of security program budgeting and spend prioritization.
Security is often viewed as a cost center, necessary to keep the business afloat and to avoid costly events, but not generating profit. This can put CISOs and security leaders in precarious situations in which they must compete for budget with other revenue-generating areas of the business. Different stakeholders within the organization will have their own opinions on the value of cyber spend, whether finance, legal, sales, IT, marketing, risk, etc.
Prioritization with FAIR
To prioritize spend and compete for additional budget as a security leader, it is important to speak the same language as some of the other areas of the business. One method to accomplish this is cyber risk quantification, a method used for translating cybersecurity events into financial terms. Protiviti helps organizations accomplish this using Factor Analysis of Information Risk (or FAIR). Like other schools of thought around risk, in FAIR, risk is comprised of frequency (likelihood) and magnitude (impact). However, other models don’t break the model down further. On the magnitude side, there are six forms of loss that are typically analyzed:
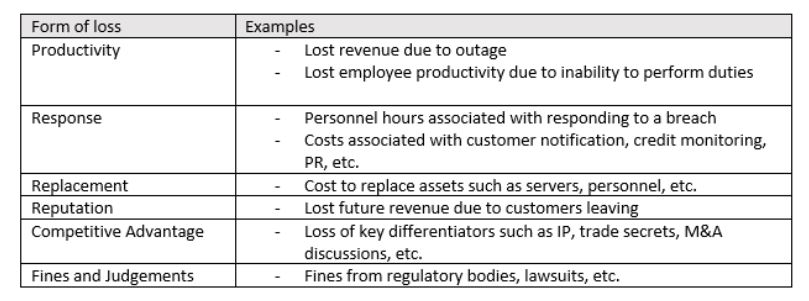
Source: The FAIR Institute
When CISOs start looking at potential cyber events through this lens, it can help put numbers around otherwise arbitrary risk ratings. When communicating with the board, what does a high risk mean to them? How did the risk assessment team come to the determination of a high risk?
Using risk quantification, the CISO can explain to the board that a cyber event is expected to cost the organization between $1.5M and $2M next year and show how that estimation was determined.
This enables the CISO to begin to frame their budget argument. However, they can also go one step deeper, looking at the cost of their proposed initiatives and building a business case based on the quantifiable risk reduction associated with them.
The following table outlines top cyber risks of a sample organization:
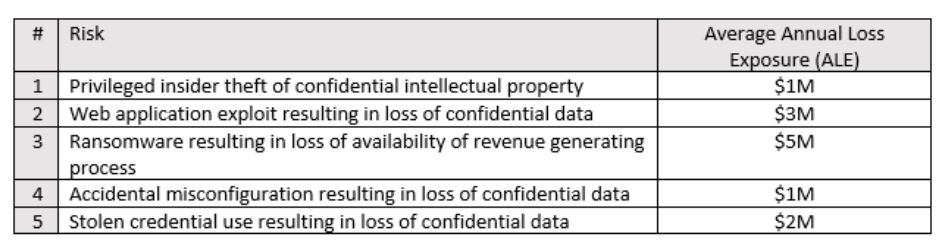
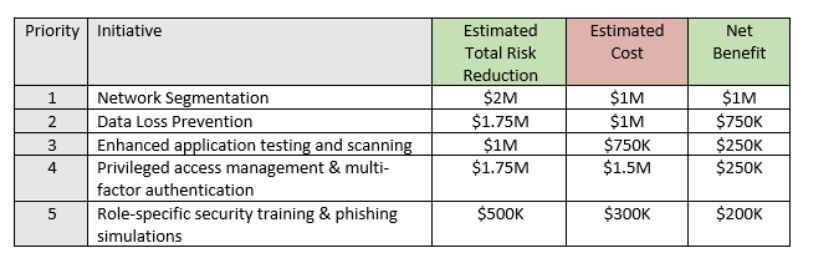
Now, consider the following proposed risk reduction activities from the CISO’s roadmap and how they tie to the various risks:
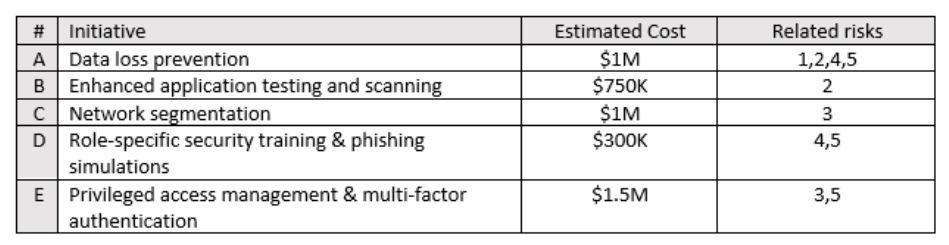
Since the proposed initiatives now have estimated costs and are mapped to specific risks, the CISO can work with their risk analysts and security team members to estimate what the impact of each initiative would be on each risk.
Take data loss prevention (DLP), for example. For the applicable risks (Risks 1, 2, 4 and 5), we may expect DLP to reduce the organization’s susceptibility to attempted data exfiltration attempts by 25 percent based on research of the particular solution being considered and its potential impact in the organization’s environment. Calculating the estimated risk reduction for each of the related risks might look like this:
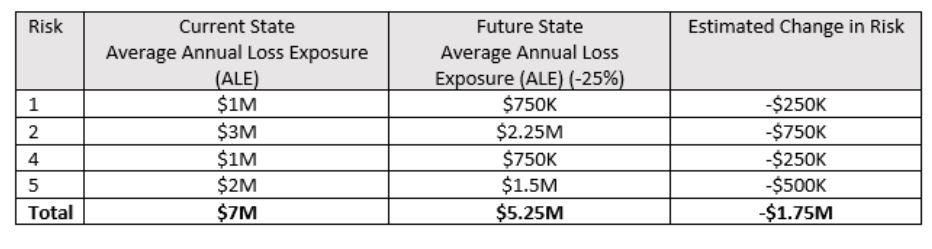
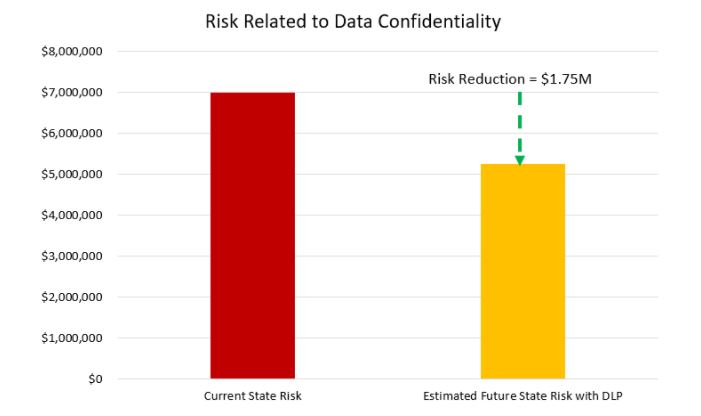
Based on this analysis, deploying DLP for the cost of $1M will reduce risk by $1.75M, which is a net positive of $750K. If the CISO performs this exercise for all proposed initiatives against the organization’s top cybersecurity risks, they can then make an argument for additional budget based on the following:
- How much they will spend on what efforts?
- How much they will reduce current risks by?
- How should they prioritize their efforts based on risk reduction?
Keeping in mind however, various initiatives will impact unique inputs into the FAIR model differently. Some controls will impact frequency of loss events while others will impact the magnitude of loss events. The estimated changes to the scenario inputs by future control state should be well documented with any assumptions and rationales.
For example: Because DLP is in place, privileged insiders will be less likely to attempt to steal confidential information, resulting in a reduction of threat attempts by 25 percent.
Once estimated future state impacts by control are established and well documented, the net benefit of each effort can be shown:
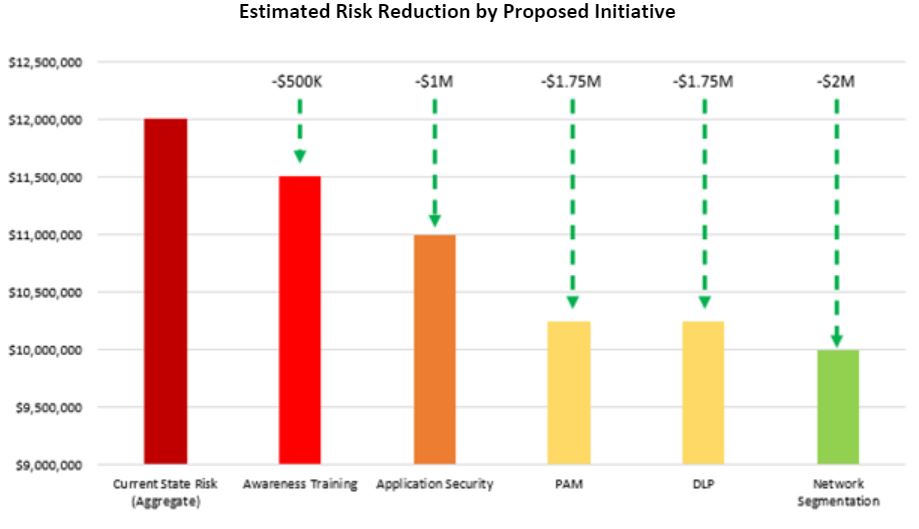
Other factors may come into play that impact a proposed effort’s priority such as the organization’s readiness, ease of implementation, whether external resources will be needed, etc. but performing an exercise in which estimated risk reduction is identified by initiative can be an extremely valuable tool in the CISO’s tool belt as they try to make the best strategic budget decisions for their organization.
Conclusion
A risk-based approach has proven to be effective in undertaking risk mitigation efforts, which are vital to any organization. The threat of cybercrimes is growing across all industries and types of companies. It is incumbent upon the CISO of an organization (or its equivalent role) to get ahead of this threat.
Every organization, project sponsors and stakeholders are unique, and Protiviti can provide a tailored approach to drive organizational adoption of risk management strategies. Cyber risk quantification enables organizations to work with varying quality of data to quantify their risks. Data can come from a variety of sources including organization-specific data, industry data, threat intelligence, etc. It does not require a large effort to identify and quantify an organization’s top cyber risk and once these risks are quantified, it resonates much more with organizational leaders than “high, medium, low” risk discussions.
Protiviti can help organizations of diverse backgrounds and sizes create a compelling business case and a roadmap to implement an individual security strategy.
To learn more about our cybersecurity consulting capabilities, contact us.



