The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) has achieved broad adoption across a range of different industries. The NIST CSF, which allows organizations to evaluate their maturity against a detailed set of standards and best practices, is broken down into five core functions:
1. Identify: Does the organization know how to manage cybersecurity risk to systems, people, assets, data and capabilities?
2. Protect: Has the organization implemented safeguards to ensure delivery of critical services?
3. Detect: Does the organization undertake activities to identify the occurrence of a cybersecurity event?
4. Respond: Does the organization undertake activities to address a detected cybersecurity incident?
5. Recover: Does the organization undertake appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident?
When it comes to organizational performance across these functions, one notable outlier emerges. An analysis of over 100 NIST CSF assessments completed by Protiviti over a four-year period shows a very high level of consistency in average scores across core functions, with the notable exception of recover.
NIST Category vs. Average Organization Category Score
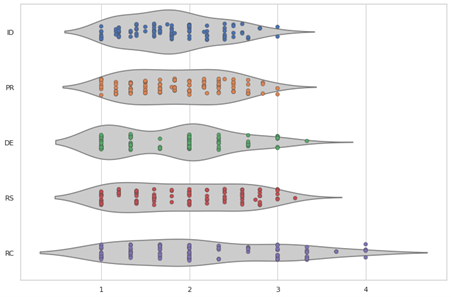
The above graphic shows the spread of average NIST category scores for 110 different organizations. The trend is apparent; while most companies score consistently across identify, protect, detect and respond, there is a noticeably larger spread across recover. A grouping of companies on the right end of the average category score axis has achieved the highest possible maturity score, with others inching toward it. This implies a broader range of approaches taken to address recovery-related standards and controls, with some firms performing significantly better than others in this area while maintaining homogeny in maturity across the other four functions.
Put another way, recover is the most difficult category for an organization to outperform their peers in. As organizations look for newer and more intuitive ways to rank themselves against peers using NIST maturity scores, they may consider reporting the percentile in which they sit, rather than their score versus an industry average. Using this approach, companies need to do better in recover to keep up: to score better than 90 percent of other organizations in any of the other four categories, an average score of around 2.5 would be required. To do the same in recover, an organization would need to score a full point higher at around 3.5.
What does this disparity between recover and the other four core categories mean for business leaders? For one, that companies may be further behind their peers than they realize when it comes to recovery capabilities. As the percentile example above shows, scoring in kind with, or ahead of, other organizations requires higher maturity than may be expected.
Additionally, the data suggest that a certain subset of organizations are significantly underspending and underperforming in recover. In a survey conducted by Protiviti, companies consistently estimated recover-related investments to occupy the smallest share of their budgets out of the five NIST CSF categories. Combined with the stratification seen in the average score, there is presumably a significant amount of underspend occurring at the lowest scoring companies.
Altogether, these trends imply that some organizations may be overspending on capabilities meant to reduce the likelihood of cyber events at the expense of capabilities that may minimize their impact. This trend is especially concerning given that breaches are fairly common and have remained so for several years: Twenty-five percent of Fortune 1000 companies will have a breach in a given year, according to the 2020 Cyentia study, a figure which has held firm for the past five years.
Organizations can address this issue by assessing their recovery capabilities. Given the wider spread of scores in this function, an organization may be on uncertain footing in this area, even if they are achieving average maturity marks in other categories. Understanding where an organization falls in this broad spectrum can help ensure that breaches are able to be contained and understood quickly, especially in the face of increasing ransomware and other attack varieties that may have significant business impact if not mitigated. Protiviti has developed the Guide to Business Continuity and Resilience, which examines critical concepts around business continuity and related practices. The guide serves as a comprehensive overview of where to begin to prepare for the unexpected and build resilience. Click on the IT Disaster Recovery topic to see just some of the factors we consider when working with clients to strengthen their recovery practices.
To learn more about our cybersecurity capabilities, contact us.





