Having worked with different clients throughout the years, across industries and varying sizes, we notice there are many thematic “hot topics” and concerns that come in waves. Much of this has to do with evolving audit requirements, increased regulatory compliance and ensuring there is accountability, transparency, and effective risk management practices throughout organizations.
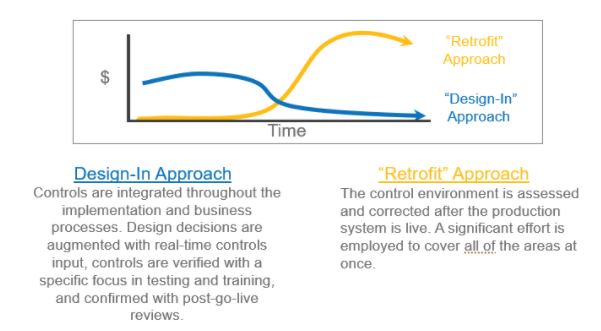
As many companies are planning for, or have already started their journey to SAP S/4HANA, now is the time to ensure the below considerations are designed into the project or at least discussed with key stakeholders early on (e.g., collectively deciding SAP Access Control is the preferred access management solution). Without these discussions, organizations may find themselves having to retrofit an area after the initial upgrade, which will end up costing significantly more time, money and end user disruption. Or worse, on day one of the go-live they are forced to assign end users “SAP ALLmost” access just to keep the business running!
Source: SAP
Security and Access Control
This topic has been in the spotlight for the last several years (but one that still causes many companies to have audit deficiencies). While it may be well-known that security roles should be designed SOD-free and implementing automated access management tools like SAP Access Control and Identity Access Governance is essentially the bare minimum, it is important that this is built into the project from the beginning (if you do not already have a solution in place). Timing is key as this provides the ability to design SOD-free security roles in parallel with the upgrade and have them tested as part of the established project testing cycles (i.e., minimizing the need for rework if done later). For organizations planning to pursue a full Fiori user experience, security design is even more important to get right early on as there are no quick fixes, like assigning “SAP ALLmost,” within the Fiori architecture. The security design greatly influences the look and feel of the user experience and controls the appropriate access. Therefore, it is incredibly difficult to address any issues after go-live.
Configuration (Automated) Controls
Companies are taking this opportunity to maximize their use of the S/4HANA software, enabling standard features and functionality that can serve as a control. For example, establishing three-way matches, tolerance limits, required fields and system messages. While many implementors promise to establish these controls through their standard “out-of-the-box” model company/industry solutions, keep in mind that is greatly oversimplifying the process and effort. Each business needs to first understand the available configuration settings that can be implemented as a control (i.e., understanding the software capabilities), then decide on the appropriate settings based on the business requirements and control needs. For example, what is an acceptable PO to Invoice tolerance for your business? Two percent? Five percent? Should the system message prompt a warning to the end user and then allow them to move forward? Or should the system prompt an error message preventing them from moving forward until the issue is resolved? Key business process decisions need to be made to implement these configuration controls, which generally has a dedicated workstream within an S/4HANA project. The goal is to maximize automated controls, maximize resources’ time to be productive and achieve greater efficiencies and standardization through automation.
SAP Process Control and SOD Transaction Monitoring (Quantification)
As organizations mature and adopt more automation and GRC products, Process Control and SOD transaction monitoring (quantification) are on the top of the list. We are finding it more common that SAP Process Control implementations are embedded as a separate workstream during a S/4HANA project (e.g., enabling continuous controls monitoring). While it may sound like adding more work to an already large initiative, companies recognize the need to protect their investment of designing, standardizing and automating configuration controls. Not only will this help ensure compliance, but the automation also systematically enforces standard business processes and increases efficiencies.
A common scenario we often find is organizations with lean headcount or resources share many of the same responsibilities, allowing users to have conflicting access. Ideally, these access assignments would be separated, but we understand there are exceptions. In these cases, we are seeing organizations implement tools like Greenlight’s Access Violation Management (AVM) for SOD transaction monitoring (quantification). Whether it is an SOD that was unintentionally assigned to a user or a known exception, this gives the organization visibility and accountability when conflicting access has been performed. It is also often a better alternative to costly and less effective manual controls.
Cloud and Cybersecurity
With more companies opting for a smaller technical on-premises footprint and adopting the cloud because of costs and flexible scalability, often this introduces new risk exposures and the need for new controls. It is important to understand the impact and how the organization plans to account for those changes. Companies are performing assessments of existing controls against leading practice cloud controls to identify gaps and optimization areas, as needed.
In addition to incorporating critical cloud controls, companies are looking to understand existing cybersecurity vulnerabilities within their systems. There are automated solutions that will help expedite these assessments and continuous monitoring. For example, Onapsis is a solution to perform a thorough assessment to identify vulnerabilities, understand the business impact, prioritize risks and develop a remediation plan (e.g., custom code, transport and system assessments). Ultimately, it is important to invest in securing the “crown jewels” and monitor the known risks and have a solution for detecting and identifying unknown risks. It is critical to have established protocols to respond to cyber incidents and a recovery plan.
Data Governance and Classification
While classifying and securing data may sound like a no brainer, it is much harder to do than it sounds. Directly impacting how an organization’s security roles should be designed and assigned, we need to understand where the data resides and its classification (e.g., public information versus restricted). Embedding a strong data governance program will help ensure greater control around the data and ensure compliance with regulations such as CCPA and GDPR. Luckily, there are automated solutions that will help accelerate this process (for those that do not already have a solid handle on it). For example, BigID is a solution to help companies identify, classify and develop a data privacy and protection roadmap. Even as recently as a few years ago, these capabilities were not available to assist in data privacy and protection.
Updating Risk Universe and Internal Control Matrices
This last step should not be overlooked as it is intertwined with those detailed above. As the organization migrates to S/4HANA, it is necessary to revisit existing SAP application and general computer control frameworks and make appropriate updates. For example, the IT landscape may be different with new Fiori and HANA database risk considerations. Is the organization on-prem versus cloud? In addition, if the organization has implemented new business process configuration controls, this is the time to update the work program and eliminate manual controls and take credit for the automated controls (not to mention, it should significantly reduce the time resources are performing manual controls as well as costs associated with auditing the controls).
While it may seem like excessive overhead to take on these workstreams during an already demanding S/4HANA project, it is a necessity to do it right the first time around. Having to circle back and retrofit any one of these areas afterwards would only cost the organization more time and money in the long run (and depending on the severity of the issues, potential audit deficiencies to go along with it). As legendary basketball coach John Wooden said, “if you don’t have time to do it right [the first time], when will you have time to do it over?”
Join us for our 5-part SAP webinar series which includes the topic: Protecting S/4HANA Finance With Emerging Security and Control Technologies. Series begins on February 25.
To learn more about our SAP capabilities, contact us or visit Protiviti’s SAP consulting services.