Organizations are struggling with how to structure their cybersecurity and risk management programs in cloud environments. They are failing to understand the frameworks and resources available to them to securely configure and audit their cloud footprints. In some cases, organizations are moving to the cloud with architectures that fail to adapt to the paradigms of cloud computing and cloud design patterns. One of the foundational elements often missing in cybersecurity and risk management programs is the overlay of security controls and governance to the various arenas of the modern technology operating environment. The figure below outlines six possible arenas in which organizations are operating.
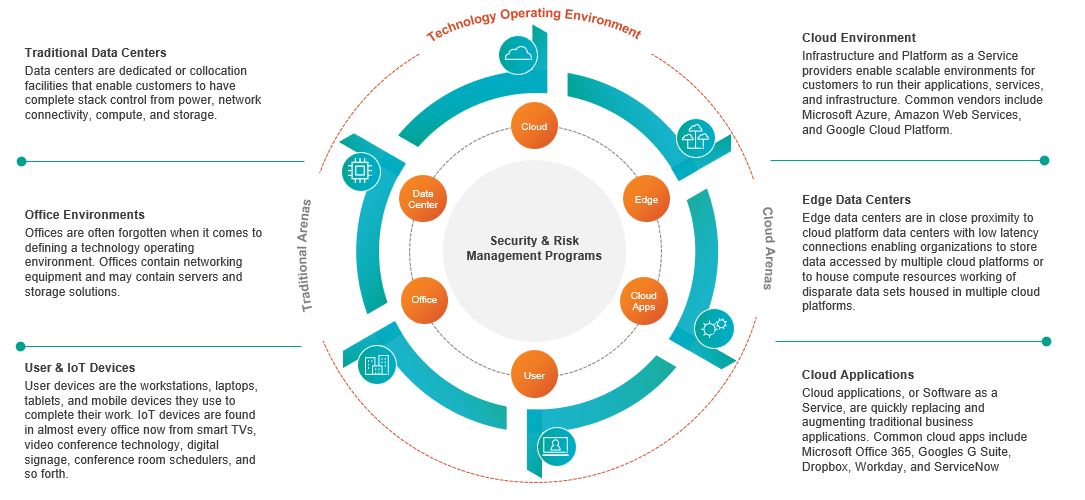
When we look at the modern technology operating environment, it becomes clear that we are all living in a hybrid arena, where our workloads transit both traditional and cloud arenas, and will do so for the foreseeable future. Organizations need to structure their security controls and governance to align to capabilities that can then map to implementations that are appropriate for the arena they are operating in. Yes, this introduces complexity; however, the trade-off is an operational nightmare.
Vulnerability and patch management capabilities are a prime example of how a program designed for traditional data centers will fail in a cloud environment. In a data center, an organization will likely deploy scanners (or agents), create periodic reports, and ideally patch systems on at least a monthly basis. In an ephemeral cloud environment, periodic scanning of compute instances is ineffective as these instances should be spinning up and down on a regular basis. These instances will be reusing IP addresses at a rate unmatched in a data center environment. The results are scan reports that contain systems that no longer exist, or worse have been replaced with new systems that contain different vulnerabilities. To achieve the same capability outcome – cataloging and remediating known vulnerabilities – organizations should establish an image that is updated via an automated factory and published for the organization on a periodic basis. Vulnerability scans should be performed against this image to ensure known vulnerabilities are patched. Security teams can then use the cloud APIs to gather the image in use by current instances to understand their vulnerability footprint.
Organizations should also take the time at the beginning of their cloud journey to understand the resources and frameworks available to them. In a recent local ISACA chapter webinar, one topic was the use of provider-agnostic resources like Cloud Security Alliances, Cloud Security Guidance and Cloud Control Matrix to establish a baseline of controls and capabilities that can be augmented by provider specific resources. The Center for Internet Security (CIS) offers security benchmarks for each of the major cloud platform providers, core services, and operating systems. These benchmarks harden the environment and reduce the overall attack surface. A good rule of thumb is to use the CIS Top 20 Controls as a prioritization mechanism. Further, each Cloud Service Provider offers extensive documentation on the security options for each service, and these should be fully understood and adopted in alignment with the organization’s risk appetite.
In the same light, organizations should train their staff on cloud concepts and design patterns and should require teams to have cloud specific certifications in addition to other professional certificates. For example, Amazon Web Services (AWS) offers Solution Architect, DevOps Engineer, Systems Operations Administrator, and specialty certification for Security, Database and Advanced Networking. Microsoft Azure and Google Cloud Platform have similar certification journeys as well. These certifications require a baseline of security knowledge and best practices that can be invaluable for operating in the cloud. For auditors, the Cloud Security Alliance is planning to release a Cloud Auditor certificate in Q4 of 2020 which will help prepare auditors for the unique risks and assessment methodologies for cloud environments.
To learn more about Protiviti’s cloud, cybersecurity and data privacy capabilities, contact us.



