Enterprise networks have been described as being like an egg, with a hard shell on the outside and soft on the inside. There have been heated dialogues between security professionals that treat the “insiders” as trusted and anything outside the network as a threat. However, this thought process began to change after the introduction of Zero Trust Networks (ZTN). ZTN represents a paradigm shift from the existing security and threat model of “trust but verify” to a “never trust, always verify” approach. The introduction of technical approaches such as Software Defined Perimeter (SDP), have served as a catalyst to propel the adoption of ZTN. Some security professionals even argue that SDP is the most effective method for adopting a Zero Trust strategy.
Based on our experience we believe SDP is currently the best available framework for the implementation of the ZTN concept and theory because it meets all three ZTN principles.
Basics of Zero Trust Networks
The concept of ZTN originated from the Global Information Grid (GIG) Network Operations (NetOps) endeavor operated by the U.S. Department of Defense (DoD) in the early 2000s. Since then, the concept of ZTN has evolved and matured to the point where hundreds of organizations have implemented or are implementing ZTN principles into their own network infrastructures.
The ZTN mindset sees everything and everyone as a threat. According to the Cloud Security Alliance (CSA), “ZTN is a network security concept centered on the belief that organizations should not automatically trust anything inside or outside traditional perimeters and aims to defend enterprise assets.” ZTN embodies the following concepts:
1) Don’t trust anything regardless of where it originates (e.g., cloud, on-premise, etc.)
2) Enforce access control on everything
3) Log and monitor all traffic to identify malicious activity.
Given the three principles above, ZTN enables organizations to mitigate security and configuration challenges. These challenges could include securing a rapidly changing network perimeter (e.g., on-premise and cloud), addressing user accountability concerns and decreasing the amount of security tools needed to secure the environment.
Software Defined Perimeter (SDP) and Zero Trust
The Cloud Security Alliance (CSA) developed the SDP framework around the same time as the DoD developed the ZTN concept. SDP stems from the same core principles of ZTN and its goal is to secure applications, users and the connection between them. The SDP architecture is composed of a control plane and a data plane. The control plane is used to establish trust with the user/device and the data plane is where the data is transferred between the application and the trusted entity, which is the core concept of ZTN.
The figure below, which was published in the Cloud Security Alliance SDP Specification 1.0, shows an example of SDP architecture.
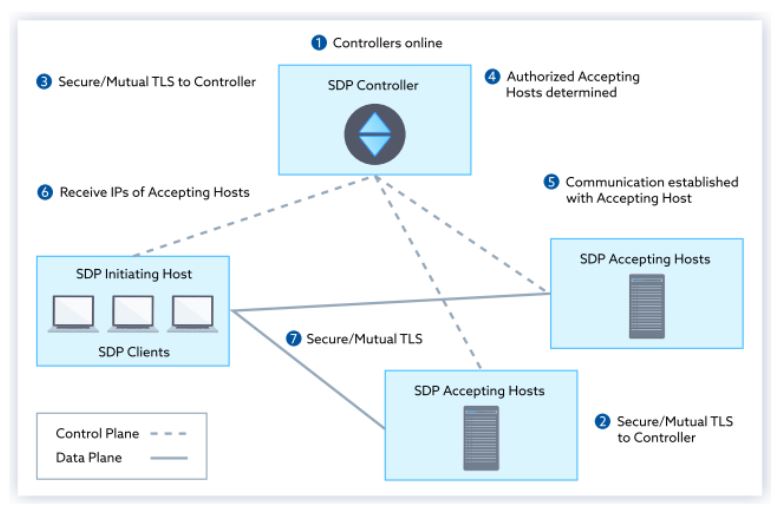
Per the Cloud Security Alliance, “SDP’s basic tenets are ABCD: Assume nothing, Believe nobody, Check everything, Defeat threats.” Supporting those tenets, the four key components of SDP are:
- Trust is never implicit for any user
- Making the user-to-applications connection over the internet more secure
- Inbound connections are not allowed
- Application segmentation is utilized instead of network segmentation.
These key components of SDP and its ability to secure all connections make SDP a prime candidate for ZTN implementation.
Parallels Between ZTN and SDP
SDP enables assets to be hidden from the user, access is not granted to any assets until the user is authenticated and authorized. This fits perfectly with the “enforce access control on everything” requirement for ZTN. SDP also questions the origin of the traffic regardless of whether the request is coming from an “insider” or an “outsider.” All traffic is considered “outside” traffic and is reviewed with a consistent level of scrutiny, which is essential for the ZTN requirements of don’t trust anything regardless of where it originates.
One of the main challenges traditional networks have faced include logging traffic to identify malicious activity. With SDP, all log traffic is centralized and assessed by the controller, which makes it easy to meet the logging and monitoring requirement for ZTN. SDP not only meets all three core ZTN concepts, it also includes a number of additional pros that could strengthen the ZTN implementation and could benefit the overall security posture of an organization.
Is using SDP the right approach for implementing ZTN?
Since taking on ZTN is a sizeable task, it is important to understand the pros and cons before taking the leap.
Pros
Utilizing SDP to implement ZTN can provide a variety of technical and business benefits, including:
1) Compliance Benefits
The SDP controller is the single point that allows users on registered devices to access specific applications. Due to the centralized nature of the controller, SDP can provide extra visibility into connections, what it was used to access, who initiated the access, when the application was accessed, etc. Thus improving reporting for compliance and regulatory requests and auditing.
2) Attack Surface Reduction and Hiding Devices
SDP makes the application infrastructure invisible to the internet due to the “no inbound connection” approach. This could assist with avoiding network–based attacks, such as application exploits, man-in-the-middle attacks, Structured Query Language (SQL) injection, server scanning and Distributed Denial of Service (DDoS) attacks.
3) Authentication Before Access
The successful usage of authentication before access requires the control plane and the data plane to be separated, which SDP can accomplish. Traditionally, the user connects to a service or network first and then is authenticated. The control plane authenticates the user first to confirm the user is who they claim to be, then authorization is provided before access is granted to services and the data. Organizations must utilize a strong method of authentication to ensure access is provided in a timely manner, so users do not experience delays.
Cons
Although there are tremendous security advantages an organization can achieve by implementing their ZTN strategy with SDP, it does cause the security policy and approach to become more complicated. We have identified several ways having such an all-inclusive strategy can be taxing:
1) High Time and Effort during Initial Setup
Technical policies that will need to be reconfigured on the existing network to transition over to a zero trust approach would be challenging since the systems need to be available for day-to-day operations. Most organizations end up building a new network from scratch that include SDP concepts of access control. If legacy systems exist, they will not be able to accommodate the zero trust framework and would have to be rebuilt, increasing the time and effort for initial setup.
2) Understanding User Access
An organization must have a deep understanding of user access rights from the highest level possible to the bottom of the technology stack. Without this, it could be very difficult to have a complete, accurate ongoing view of access changes for all resources in the enterprise architecture.
3) Impact on Employee Productivity
Although the zero trust model is meant to provide enhanced security, there needs to be a balance between that model and the availability of information to perform tasks. Keeping users from getting their work done in a timely manner could be a major pitfall for users that perform time sensitive tasks.
The implementation of the ZTN philosophy using the SDP framework prepares organizations against the next generation of security threats by allowing the infrastructure to be invisible to the internet and making “authentication first” a priority. Although there are a variety of frameworks and environments upon which the ZTN philosophy can be implemented (that we will discuss in a future post), SDP has proven itself to be one of the most powerful and compatible to ZTN concepts.



