In this two-part series, we look at the factors needed for a Privileged Access Management program to be considered mature.
In today’s dynamic world, businesses are constantly being asked to become more agile, more nimble, and more forward-thinking to keep up with customer demands and the competition’s services. This leads to more rapid changes in technology footprints, software development methodologies and a perhaps unintended consequence of security occasionally taking a backseat. This has led to cyber incidents and breaches becoming more and more commonplace in this rapidly changing technology landscape as the pressure to enhance existing and create new services outweighs traditional security measures.
These cyber incidents and breaches nearly always rely on account compromise for attackers to be able to get a foothold in an organization’s environment. From there, they can quietly move around and escalate their privileges until they get to valuable assets to either release publicly, hold for ransom or exfiltrate for other goals. Regardless of the initial account that is compromised, attackers are navigating the environment to find privileged accounts, those accounts with elevated access to an organization’s crown jewel information. Increasingly, this threat is generating more awareness and acknowledgement of the inherent risk within the security community and organizations:
- According to Forbes, approximately three quarters of all breaches start with the compromise of a privileged account
- Gartner in June 2019 called PAM a Top 10 Security Project once again, so companies are at least thinking about privileged access and buying PAM solutions.
As awareness of this issue has increased, the fact is many organizations are not feeling the full value and the risk reduction associated with having purchased these PAM tools. Why is that? Protiviti believes many organizations are not recognizing that PAM is a program and without appropriate structure and management, these programs fail to meet their potential and achieve real value.
Many organizations begin their PAM journeys as a result of a security incident, an audit or compliance finding, or other pointed reason, but see it as a discrete, one-off project to close that gap(s). This type of approach leads to a couple of programmatic risks for an organization:
- Inadequately trained resources to support the on-going operations, maintenance and rollout of the program and supporting technology. With today’s organizations going through frequent staff changes, M&A activities and events outside of their control like COVID-19, having trained staff to keep the program on track is paramount for something as critical to an organization as PAM.
- PAM solutions becoming shelf-ware – Clients buy the tool, vault the first few handfuls of accounts to close an audit finding, but do not plan for the broader rollout or know what should come next.
- Use of inexperienced implementation resources for the PAM tool selected – Resource capabilities are an important factor that ultimately will determine the effort’s overall success. Resources certified and backed by the PAM solution vendor offer greater levels of assurance of success. Resources without these skills and vendor backing lack full understanding of the ‘hidden’ technical challenges, lack program-level advisory support and are inexperienced in providing sufficient knowledge transfer and smooth operational handoff. Leveraging certified partners of solution vendors ensures vendor support and can be a great way to ensure quality of delivery, complimentary solution support and experience in similar environments with other customers.
It is critical to think about PAM strategically to ensure privileged accounts are continuously identified and protected and privileged access risks to the organization are systematically reduced. So the question must be asked, how do I know if I have a healthy, mature PAM program? Below is an overview of Protiviti’s PAM framework. Let’s take a dive, pillar by pillar.
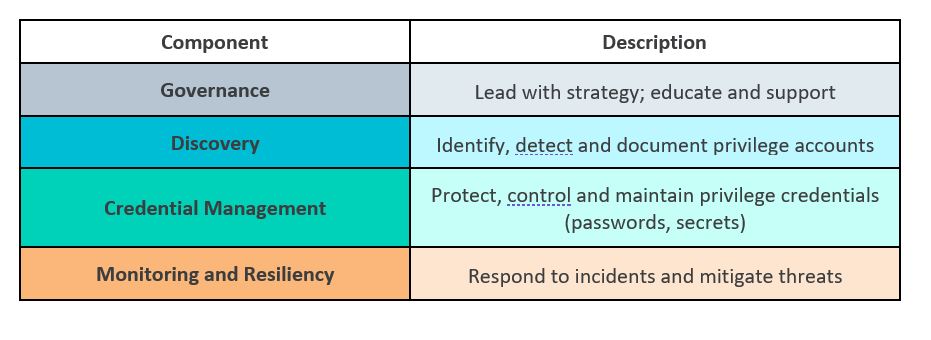
Program Governance First
Governance
Like many things in the Information Technology and Information Security worlds, PAM will only go as far as an organization’s governance and process allows. To simply initiate a project just to close one audit finding may achieve that short-term goal but not reduce systemic risk to the organization. Establishing a well-governed program is key. Questions to ask include:
- Are PAM-related requirements clearly articulated in the organization’s policy and standards? Without this, it will be nearly impossible to obtain buy-in throughout the organization on what privilege is and what controls need to be enforced, and for what accounts.
- Is there a risk model to guide our efforts? Short of a PAM risk model, the organization will be susceptible to the challenge of either over-controlling the environment (negatively impacting user experience and increasing cost) or under-controlling the environment (insufficient security controls). Without a PAM risk model, there is no clear way to determine what assets to protect and what controls to apply to the account.
- What tasks need to be performed? Who is responsible for performing these tasks? Who approves any actions taken? Establishing a PAM RACI chart clearly outlines who is responsible for each element of running a PAM program. This will need to include stakeholders within InfoSec like the PAM (or Identity and Access Management (IAM)) team and the SIEM / SOC team. It will also include resources outside of InfoSec, including application, account and data owners.
- What is the strategy and the drivers around what to rollout first? Being too aggressive with a rollout of every feature and functionality can lead to a failed deployment. Make sure the strategy considers quick wins that will increase end user adoption, and reduce the threat surface in a manner that addresses the risks identified in the modeling exercise.
Part 2 of this series covers PAM discovery, credential management and why monitoring and resilience are essential to a mature PAM program.





