“Data is the new water.” That observation by a chief information officer we met a few months ago really nails the way we think about data security and compliance today. He went on to say, “We have to reserve it. Preserve it. Share it. And make sure it’s clean.” Innovations in cloud, mobile, social media and big data mean the opportunity for increased risk. And that increased risk means that data security planning has to be more than just a check mark on a compliance report. In a recent webinar, we talked about how planning ahead for security can make the S/4HANA journey safer and more compliant.
When we work with SAP S/4HANA clients, we like to say that security is now an enabler that helps organizations weather market shifts, changing operating environments and the evolving regulatory environment. Since the introduction of SAP HANA, how organizations operate and secure their SAP environment has shifted significantly. We have left behind traditional security architecture for more collaborative business models. This evolution impacts how an organization defines, plans, implements, monitors and builds resilience around its security practices.
In today’s S/4HANA environment, how an organization is equipped to respond to cyber threats changes regularly, as new threats emerge. Many of our S/4HANA clients have elaborate security strategies. Yet they still see vulnerabilities, from access management and patch management to unsecured services and connections.
Keep this one rule in mind: security should not be an afterthought. Those who attended our recent SAP S/4HANA webinar series heard this message again and again. Organizations should plan methodically for security and controls in the same way that they plan infrastructure, integration, data governance and other key components of an S/4HANA implementation. Furthermore, it needs a holistic approach which requires a continuous improvement to ensure the organization is properly managing long term.
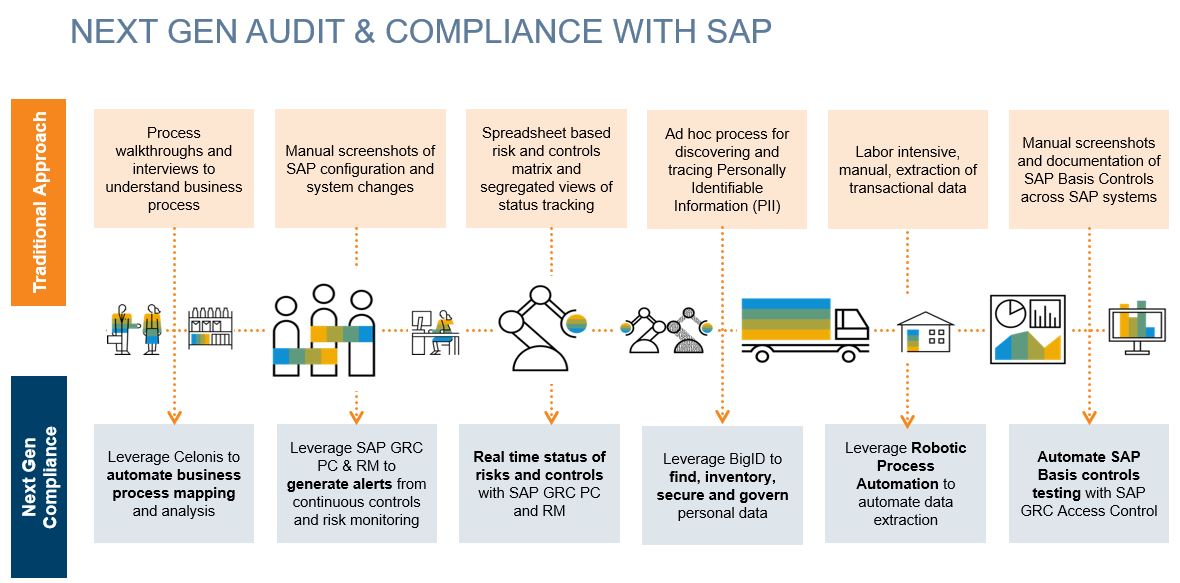
Next-Generation Processes and Tools for Audit and Compliance
During the S/4HANA planning process, there are several questions to ask to understand the organization’s current audit and compliance processes and where it intends to be in the future. By the way, getting senior executives from across the organization involved in setting these goals is our recommendation to ensure the objectives are understood and embraced by all. We also find it helpful to perform interviews or process walkthroughs, or risk ending up with an incomplete picture that may not capture ever scenario.
Ask:
- Does the organization still rely on uniform and reactive risk assessments?
- Does the organization still perform audits and reviews the same way as in years past?
- Has the organization introduced new technologies to enhance the internal audit function?
- Is the organization able to leverage enterprise data efficiently to conduct risk assessments and continuous monitoring?
- Is the organization positioned to respond to changing business process and IT risks associated with S/4HANA transformation?
- Has the organization added resources and skill sets to addressed increased expectations from internal and external stakeholders?
While these questions are among the thought starters that will drive the planning processes, remember that controls are only good if designed appropriately and at the right time in the S/4HANA journey. It is very important to design and identify controls early in the process versus trying to fit them in later.
As for tools, there are a range of next-generation GRC tools and processes available. For example:
- Data analytics provides insights into processes and validates completeness of data extracts
- Process mining provides a complete understanding of all processes that are actually being followed
- Controls testing focuses on exceptional processes that can often be less well-controlled
- Data privacy and protection software from companies such as BigID help secure customer data and satisfy privacy regulations
- A next-generation approach provides a vision for continuous monitoring that is focused on process changes.
We work closely with our clients to ensure that everyone is up to date with the latest S/4HANA releases and covered by the next generation SAP compliance and audit tools.
Regardless of where the organization is with the S/4HANA journey or internal controls roadmap, these steps are critical:
- Ensure the chief information security officer (CISO) is an integral part of your S/4HANA transformation project
- Emphasize building a secure culture: security is everyone’s responsibility!
- Security and controls should be business process enablers, not just a compliance check box
- A next-generation approach provides a vision for continuous monitoring
- Plan ahead: avoid retrofitting the S/4HANA controls environment.
And finally, as the S/4HANA implementation begins, remember that security is a program and not just a team or module. Ultimately, the critical pieces make up a successful holistic program:
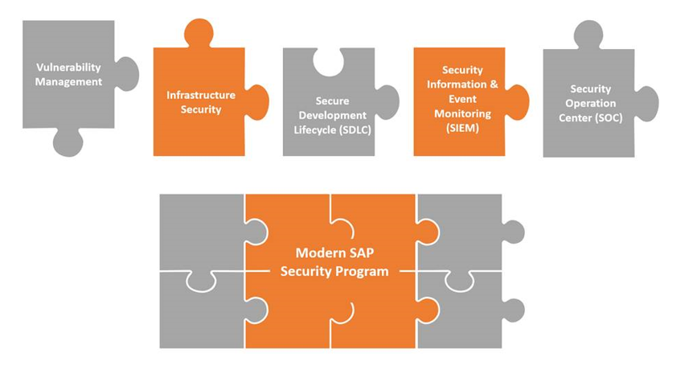
We like to say we’re living in the “age of ‘with’,” which essentially means, work WITH the right tools and work WITH the right people, following the right processes, and success will happen.
To listen to the entire SAP S/4HANA webinar series, click here. Or, visit Protiviti’s SAP consulting services page for more information on our solutions.