Things just aren’t as simple as they used to be. When it comes to managing organizational IT risks associated with confidentiality, integrity and availability (the long held “CIA” triumvirate within security), it doesn’t get any easier. A confusion of terms as well as the merging of traditional security and resiliency processes has contributed to recent noise. As companies address the risk of cyber breaches (hacks, ransomware, social engineering, etc.) and seek to develop a cyber incident response plan (CIRP), confusion emerges on how the corresponding activities fit within IT security, crisis management and business resiliency (or continuity). This post more clearly defines the new converged risk management approach that we see emerging in the marketplace and provides some recommended steps toward the management of these disciplines. All of this represents but a small piece of a larger focus on Operational Resilience that we are beginning to see gain traction, particularly in the financial services industry.
Most organizations recognize the need for a CIRP so they know how to respond in the event of a cyber breach. The risk of a cyber breach is very real, as evidenced by the nearly constant hacker attempts and successes in the news each day. The risk factor is recognized by executive management and boards who are asking relevant questions regarding the level of preparedness by their organizations to respond to a breach or related outage event. 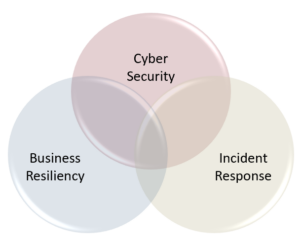 While the concept of ensuring that appropriate cyber controls are in place to prevent a breach is outside the scope of this post, the ability to respond to an event in a rapid and thorough manner that has been internally tested in a collaborative manner is equally important. That need has given rise to the development of CIRPs to document a cyber breach response. But how does a CIRP link into crisis management, business resiliency and other types of incident response plans (IRPs)? That’s a question many organizations are asking.
While the concept of ensuring that appropriate cyber controls are in place to prevent a breach is outside the scope of this post, the ability to respond to an event in a rapid and thorough manner that has been internally tested in a collaborative manner is equally important. That need has given rise to the development of CIRPs to document a cyber breach response. But how does a CIRP link into crisis management, business resiliency and other types of incident response plans (IRPs)? That’s a question many organizations are asking.
A CIRP, while written to address specific elements of cyber risk, shouldn’t exist as a standalone document or process. Ideally, it should be part of a broader risk management program with ties between business resiliency/continuity and cyber security.
Companies may have many different types of response plans (or IRPs) to address various risks perceived as highly significant and highly likely. The CIRP is one such example, however there are many others, such as:
- Hurricane response plan
- Building outage or relocation
- Civil unrest
- Active shooter, etc.
Other plans or programs are specific to an industry or type of business. A couple of examples are:
- Plant incident response programs (generally driven by Environmental Safety and Health (ES&H))
- Emergency operations (or management) plans (response plans for hospital incidents that impact clinical – patient-facing – operations)
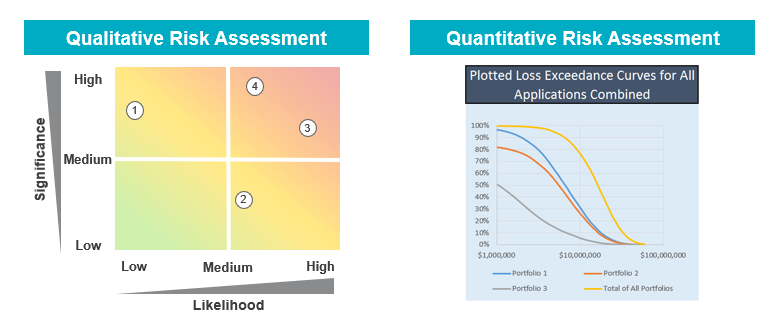
All of the above are types of incident response plans that address risks in the organization that are perceived to be highly significant and highly likely, such that their inherent risk demands a specific response plan. A methodology that incorporates both a qualitative and quantitative risk assessment will provide an organization the direction needed to incorporate the right plans to offset identified potential risks. Questions including “are we doing enough to minimize risk, ” “how much would a breach cost us?” and “are we spending on the right things?” are critical to developing the right risk strategy. While an organization can’t (and shouldn’t) have a response plan for every type of outage, it can (and should) have plans to address or mitigate its highest risks.
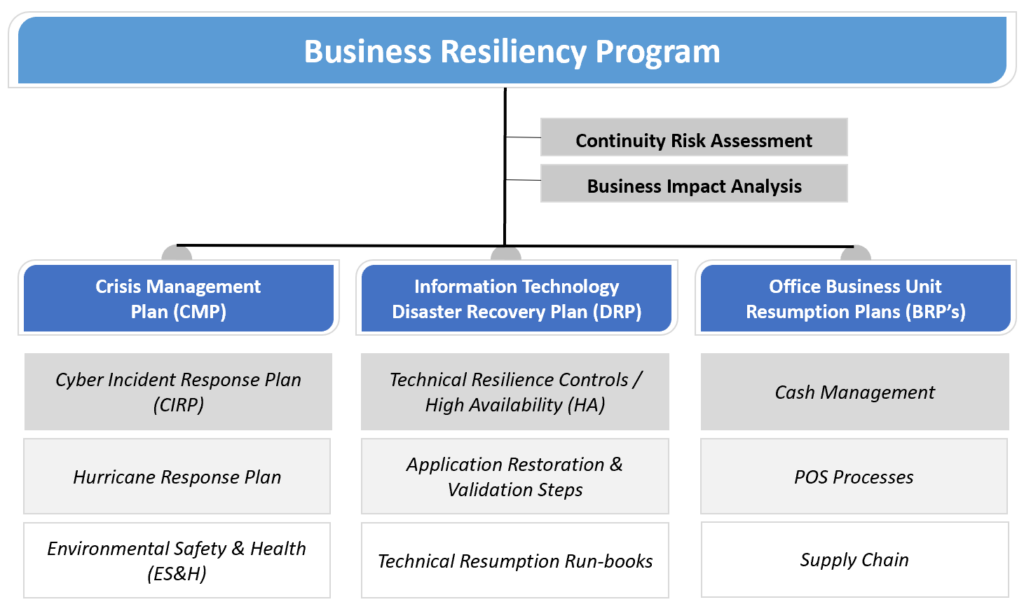
All of an organization’s IRPs should be governed by an organizational crisis management plan (CMP). A CMP provides the structure, protocols and communication mechanisms to ensure that whatever type of CIA-related outage event occurs, personnel know who to contact, how to prioritize and when to escalate. It also represents the playbook for responding to events that may involve actual life and safety risks. As such, it is key to have in place to demonstrate management’s ability to quickly organize, respond, coordinate and communicate.
All these components, including others like a disaster recovery plan (specific to restoring IT resources) and business resumption plans (specific plans unique to critical business processes) comprise an organization’s overall business resiliency/continuity program.
The enormous increase in cloud-based infrastructures has significant impacts on both security and resiliency. Whether clients are using cloud-based data centers (AWS, Azure, Google) to host critical components of their networks, or they are employing software-as-a-service (SaaS) oriented models for key applications, there are unique security and resiliency impacts that need to be considered together.
Given the cross-discipline nature of these tasks, the maintenance, ownership and responsibility for maintaining and testing these plans is often a point of confusion for most organizations. As an increasingly popular option, the chief information security officer (CISO) may assume the responsibilities for overall business resilience as well as their typical IT security and privacy roles. The “availability” aspect of the “CIA” security model points to ensuring the ongoing availability of the network, infrastructure and essential applications to support the company’s most critical business processes. The inclusion of resiliency controls in security related certification programs (i.e., CISSP) bears this out. Since business resiliency includes crisis management (and associated IRPs), IT disaster recovery and business resumption, there is a need for multiple owners ranging from executive sponsorship to business process owners.
As the convergence continues between cybersecurity and business resiliency related operations, organizations will need to evaluate how they are aligned to ensure the greatest level of efficiency and control. Rather than having cyber security and business resiliency operate in silos, they should be interlinked to ensure the risks of each are well controlled throughout the organization.





