More and more financial services firms are saying they are cloud first, but they are really cloud averse and it’s understandable. When we ask firms how they are embracing “digital transformation,” and the impact associated with fundamental digital change, most business owners proclaim they are transforming or evolving into digital. However, there is a disconnect between the business and support realities. The IT and security departments at the same firms will say that they are being forced to address the technical debt in their data centers as well as disruptive technologies such as Cloud, IoT and blockchain. A foundational change such as transformation, as a result of these disruptive technologies, forces a firm to reassess the applicability and cost of the controls it applies today and determine the viability of these controls for revamped processes leveraging disruptive technologies. In addition, firms may need to address conflicting pressures on multiple fronts:
- Customers want easy access to funds;
- Boards and senior executives want to find cheaper-better-faster ways to do business to increase shareholder value; and
- Corporate wants cheaper-better-faster and increased shareholder value; Regulators want to be sure that risk management and compliance requirements are factored into decisions to adopt innovative technologies.
Compliance ≠ Security
Within the highly-regulated financial services industry, there is an acute focus on maintaining regulatory compliance. Short-sighted compliance thinking when scoping IT requirements can have a butterfly effect during a breach. This pressure is multiplied when migrating and using cloud services due partly to the lack of visibility or shadow IT services. Cloud security requires a different strategy than on-premise security and is neither a check-box approach nor a “set it and forget it” approach. Compliance is the minimum a firm should accomplish in its fiduciary responsibilities.
Research conducted by Protiviti and the North Carolina State University’s ERM initiative found top risks in 2019 echo the same concerns as cloud aversion and regulatory uncertainty, as evidenced by the top three concerns expressed by board level and C-suite executives who were surveyed:
- Existing operations and legacy IT infrastructure may not be able to meet performance expectations related to quality, time to market, cost, and innovation, especially against “born digital” competitors, without the technical debt
- Regulatory changes and scrutiny may impact the way our products and services will be produced or delivered
- Rapid speed of disruptive innovations may outpace our organization’s ability to compete and/or manage risk appropriately.
In addition, under-funded security teams and programs are also challenged to keep pace with the changing landscape and threat environment. More companies are moving toward offsetting people with tools, including security tools and robotic process automation (RPA). Our view is that technology executives should leverage cloud solutions to address a number of business and technology objectives including transformation and digitalization initiatives, focusing on core businesses rather than IT infrastructure, and improving agility and speed to market. On-premise security is not equal to cloud security and requires new tools and methods.
Cloud Security ≠ On-Premise Security
In the past, organizations established a perimeter goal: Keep bad things out and protect data on the inside. Data resided on enterprise-owned IT services and devices, meaning the enterprise was either in physical or administrative control of the device (e.g. desktop, laptop, tablet, phone, etc.). Enterprise IT bought and managed its IT services on premise. Remote access may have existed, but it was limited to specific people, which meant employees had to come to an office. Security professionals spent a decade building the perfect on-premise security stack — equal parts next-generation firewall, Intruder prevention/detection, end point protection, data loss prevention and a couple more bits and pieces to cover other gaps. Throw it in a rack in the data center and wait for the Security Information and Event Management (SIEM) to report something, set it and forget it. This doesn’t work with cloud services.
Today, there is no perimeter. The new cloud environment has disrupted enterprise IT. Data resides in whatever service the employee is using, sometimes outside of enterprise control. Every business unit and employee wants or needs remote access to corporate data to be more efficient and competitive. Enterprise IT is challenged to keep up with these evolving business needs, so business units and employees are often procuring their own services or devices outside of enterprise IT knowledge and control. This also means outside of the enterprise information security and compliance infrastructure (a potential compliance risk when trying to manage cloud-based corporate data repositories). Why a compliance risk? Because there is now a potentially under or unprotected repository of corporate data (e.g. customer details, credit card information, sales data) available on the public internet. This may not be a direct financial risk, but an indirect reputational risk where customers migrate to competitors if the repository was discovered and compromised.
Cloud security is a firm’s responsibility. New tools built for the cloud must be used to meet these new challenges and evolve financial service organizations to meet innovative business needs.
Cloud Safe
To help clients meet these new challenges, Protiviti recommends implementing a next generation cloud security platform like a cloud access security broker (CASB) or a cloud access gateway (CAG) to support a cloud migration or ongoing cloud security monitoring. Their security capabilities, as described below, overlap with the security segment of Protiviti’s Cloud Adoption Framework.
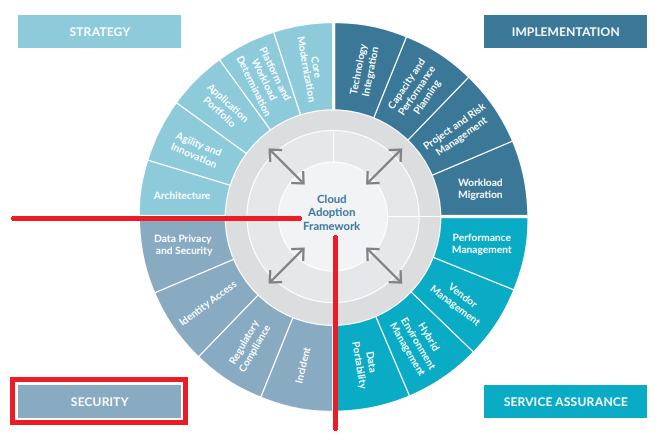
Protiviti Cloud Adoption Framework
Data Privacy and Security – Protecting confidential and regulated data is a fundamental responsibility of financial services organizations. Firms need to consider certain safeguards related to data loss prevention and encryption to achieve cloud compliance, while user behavior analytics is the leading method of identifying risky behavior. Organizations should consider the risk of multi-tenancy or shared client infrastructure and/or applications as well as physical and logical location of where enterprise data resides. A next-generation CASB provides data loss prevention for supported cloud platforms and SaaS applications while also preventing data exfiltration to unsanctioned applications and instances. Data loss prevention capabilities should include setting policies by multiple attributes such as location, device type, operating system, or access type.
Identity and Access Management – Identity remains a critical piece of the cloud migration journey. Protecting a cloud platform begins with managing access to it. Firms must determine who and how to provision access and centrally manage it. Role-based access should be considered, including user groups or job functions. Single sign-on for SaaS integrations remains a leading practice to decrease the use of passwords and implementing multifactor authentication. Key management should also be considered part of the identity and access component. Some next-generation CASBs are an extension of an identity provider while others have supported integration. While a CASB is not itself an identity provider, it does support the identity lifecycle as a policy enforcement or authorization point. In addition, a next generation CASB facilitates both discovery and distinguishing between personal and corporate cloud accounts accessed from managed and unmanaged devices.
Regulatory Compliance – Cloud service providers follow a shared responsibility model. The cloud service customer is responsible for security in the cloud. Standardized controls or frameworks must be adapted to fit the shared responsibility model and embedded in the design and approach under strategy, implementation and service assurance segments of the Protiviti Cloud Adoption Framework. Continuous monitoring, not just periodic assessment, should be implemented to ensure data security policies and IT controls are up to date. A next-generation CASB provides this in two specific methods. It provides a continuous assessment mechanism for leading cloud platforms such as AWS, Google Cloud Platform and Azure, based on either a predefined profile such as PCI DSS, CIS Foundations Benchmark, GDPR or UK Financial Data, and also allows for custom profiles such as one Protiviti is developing for Controlled Unclassified Information. Some next-generation CASBs provide app databases, like the Netskope Cloud Confidence Index (CCI), which is an objective measure of a cloud service’s enterprise readiness and is adapted from the Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM). This allows a quantitative look at the SaaS applications used by a firm and provides an additional method to implement allow or block policies based on a specific CCI level or application category.
Incident Management / Response – Firms need to have an organized approach to addressing and managing threats and quarantine in the cloud and the aftermath of a security breach or attack. The foremost considerations are response times and responsibility. How quickly is the institution notified of a breach on the cloud platform and which tools used to protect customer and corporate data? Next- generation CASBs provide incident reporting mechanisms to include user anomaly and behavior analytics, malicious sites visited, file quarantine and malware protection.
Cloud security is not a “set it and forget it approach.” Firms must include security transformation into their cloud first strategies. Cloud threats are not the same and they are constantly evolving, and firms should consider a next generation CASB to protect their data and reputations.



