“Major cyber security breaches have become routine as organizations rely increasingly on vulnerable technologies and third-party providers” – Protiviti’s 2018 Security Threat Report
Organizations always ask us the same three things: Can we really prevent a breach? Can we detect a breach? Are we currently breached? Staying ahead of each of these three scenarios requires an organization to be proactive and think about effectively detecting threats. Thinking purple involves bringing the organization’s offensive (red) and defensive (blue) cyber security teams together to determine how well their cyber tooling investment and business procedures perform.
For years, Protiviti’s red teamers have executed penetration tests and threat simulations without being caught. Unfortunately, breaches are starting to be accepted as normal even though they often continue to persist, undetected, for 200 days or more. As a result, our team is taking a different approach to maturing an environment by looking at detection and prevention differently. We are not suggesting going cold turkey on security testing, but rather, attempting to get more value from it. More time should be spent evaluating expensive security tools and validating they work as intended instead of trusting they were deployed and integrated appropriately for the environment. There should be more focus on creating sustainable detective routines and being confident about what can and can’t be seen to gain value from technical testing activities (such as penetration tests/vulnerability assessments/threat simulations).
Six Steps to Purple Thinking
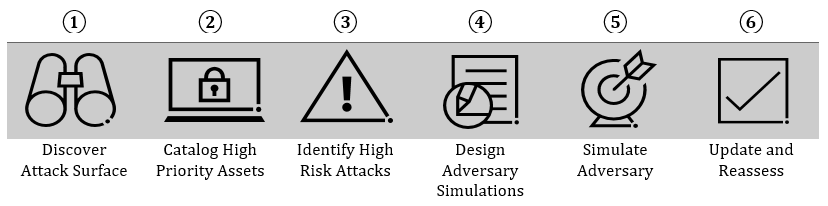
GETTING STARTED
- Discover Attack Surface – Like most organizations, a complex set of accounts and web application interfaces (external and internal) can be leveraged by malicious actors. Use all available red team, blue team and administration tools (many open source) to build up the attack surface (compromise points) of the environment. The primary focus should be on open services, authentication channels, web interfaces and privileged accounts on systems.
- Catalog High Priority Assets – Focus limited resources on the threats with the greatest risk and/or which can cause the greatest damage to the organization. To do so, create a catalog of:
- Critical revenue generating applications
- Critical IT operational infrastructure which supports business functions
- Locations where sensitive data is stored
- Critical services, web interfaces and privileged accounts identified in the previous phase
- Identify High Risk Attacks – For each high priority asset identified in the previous phase, list attacks and techniques being leveraged in the current threat landscape. The MITRE ATT&CK™ framework (https://attack.mitre.org/) is a great starting point and focus on malicious behaviors that are being used against organizations like yours.
- Design Adversary Simulations – Once attacks are mapped to high levels of associated risk, design scenarios that simulate specific malicious behavior. These scenarios should:
- Be designed to validate if a specific defensive control is operating effectively
- Contain useful information for offensive “red,” defensive “Blue” and IT support teams
- Focus on Indicators of Attack (IOA) rather than Indicators of Compromise (IOC)
- Focus on malicious behaviors (using the MITRE ATT&CK framework) rather than signatures (i.e. file hashes, words associated with malware)
- Work with relevant stakeholders, incident response, threat hunting, and monitoring teams to align outcomes and metrics for leadership.
- Simulate the Adversary – Use red teamers to execute real attacks in accordance with the designed scenario(s) and keep the tests small and measurable. Have the red team use multiple offensive toolsets to confirm detective controls are truly focused on behavior rather than looking at specific toolset signatures. Finally, maintain detailed documentation of effective attacks and observed defensive capabilities. Depending on the maturity, use threat emulation software such as Cobalt Strike or one of the free (and open source) options.
- Update and Reassess – On an ongoing basis, identify if high priority threats and technologies have changed. Do this by reviewing changes to infrastructure and discussing strategic goals with leadership. Additionally, update the threat catalog to align it to the current threat landscape and include the latest effective techniques leveraged by the red teamers.
WHY IS THIS APPROACH EFFECTIVE?
Thinking purple gives an organization a number of options for effective security solutions, including:
Business and Technology Driven Approach – An approach driven by business and technology risk rather than by compliance. The focus can be customized based on the environment, industry, technology, revenue streams, etc. This approach also establishes a common communication plan for breach resiliency and maturity against MITRE, NIST CSF, etc.
Behavior-Based vs Signature-Based Approach – Focuses on malicious compromise behaviors, which tend not to change as regularly as malicious toolset signatures. This permits an effective defense long after the attack signatures/tools change.
Enhancement Opportunities and Measurable Results – Enhancement opportunities are identified, and maturity verified as improvements are made. The objectives are achievable, and the results are measurable and trackable.
Strengthened Security Posture through Collaboration – Strengthen the defensive security posture with collaboration on development and design. Offensive and defensive teams work together to determine enhancements that fit the environment (technology and processes).
The six-step process outlined here represents the basics needed to begin an organization’s journey to “purple thinking.” Maximizing the talents of red and blue teams, fostering a collaborative environment and regular communication and innovation will help ensure cyber security across the enterprise.



