In a technology world where terms like Internet of Things (IoT), big data, augmented reality and bots are hot, a conversation about modems might seem painfully antiquated. But phone modems are still a surprisingly viable way for hackers to gain access to your organization’s valuable data. So today, we’re talking about the process for setting up an environment for interacting with modems, as well as gaining access to routers and other internal systems connected to the targeted modem.
Background
Taking a step back first, it is important to explain the methods for attacking a phone modem to understand why assessing the security of this technology is so important. Assessments like the one that will be covered in this blog were part of our standard methodology less than 10 years ago. Due to a change in focus from telephone systems to more Internet-based attacks, modem tests have been put on the back burner.
War Dialing was a common method of searching for computers and other systems near the end of the 20th century. The process is similar to port scanning (a technique used to identify open ports and services available on a network host) today, where a large list of telephone numbers is scanned and the tone returned listened to determine if the number is a modem and the types of services running on that particular system.
After determining if the number is in fact a modem on the other end, interacting with the modem can occur either via a tool called Minicom using Ubuntu, or directly through a serial connection using PuTTY on Windows. Setup is straightforward and requires little configuration. Once complete, it is as simple to use as dialing a number on a telephone (see commands below). This is where the fun begins, and where this blog details how Protiviti was able to gain access to a router on a remote network.
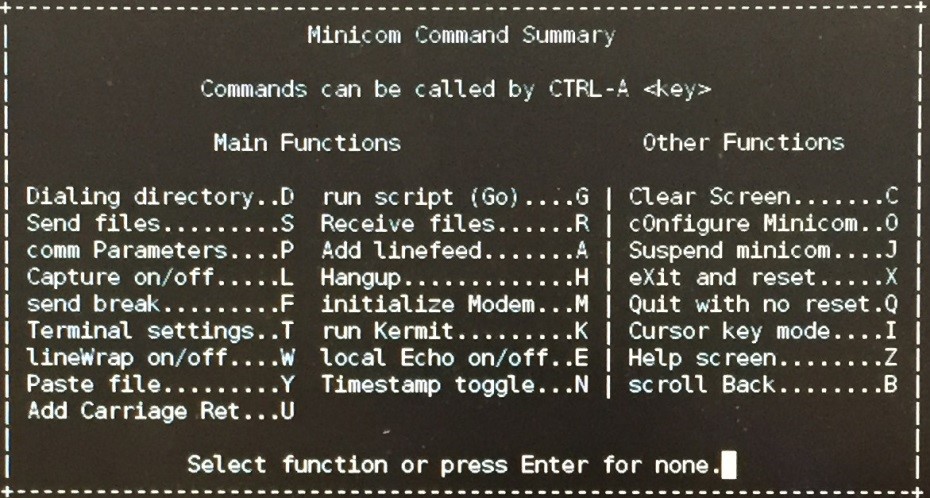
Setting Up the Lab Environment
In order to communicate with the client’s modem, we needed to first obtain the following hardware and cables:
- Carrier grade modem – Protiviti used a US Robotics Courier External 56K dial-up modem.

- USB to Serial DB25 cable – To connect the modem to the laptop

- VoIP ATA (optional) – If a telephone line is not accessible, then an ATA would be required to convert the analog signal to digital and then back to analog on the client’s end.

- Laptop running Windows or Linux – Protiviti used an IBM T60 running Kali Linux since the tool needed to dial out was preinstalled within the APT repository.

The following can be used if access to a telephone line exists (items pictured below are a laptop plugged into a modem using a USB to DB25 cable and an analog out to port cable):

If a telephone line is not available, then use the VoIP method (items pictured below are a laptop plugged into a modem using a USB to DB25 cable and an ATA plugged into the modem with an Ethernet port going to a router):

Performing an Assessment
The Protiviti team can clone an Outlook Web Application (OWA) webpage and purchased a phony domain that mimic well known domains. Email can then be sent to a sampling of employees stating that the helpdesk (which was actually the Protiviti team) was updating to a new OWA website and needed everyone to test their access. When employees enter their credentials on the website, those credentials can be harvested.
Why is this important, and what does it have to do with the modem assessment?
Modem’s can be found to use Active Directory (AD) and Terminal Access Controller Access-Control System (TACACS+) to authenticate users. This protocol was created by Cisco and designed for authentication, authorization, and accounting (AAA). Although utilizing AD in and of itself is not an issue, utilizing stolen credentials an attacker would not have any restrictions to authenticate. To paint a picture, this means that an attacker who is able to successfully obtain an employee’s credentials and is able to locate the number to dial to access the modem (i.e. via war dialing) could gain access to the client’s internal network.
This diagram illustrates how the Protiviti team accessed a remote network.
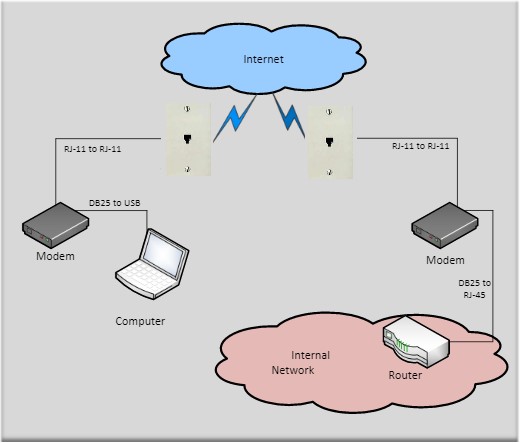
By dialing the phone number of the modem using Minicom, the Protiviti team was able to create a successful connection to a modem. The interface Protiviti was able to interact with was a Cisco C3900 router. Once the team was able to identify the type of router, they decided to research default credentials for the device and began attempting to brute force the login screen. When the team was unsuccessful in gaining access to the router using default credentials, the team used the credentials received from a phishing campaign. Immediately, the team noticed that all credentials harvested were able to successfully authenticate to the router. Once in, reconnaissance was performed and location inside of the network was identified. The team was able to retrieve encrypted password hashes of local modem users. Ultimately, the team was able to use the modem as a jumping off point to the rest of the internal network.
Pen Tests a Must for Modem Users
Performing a penetration test on a regular basis is critical for clients who still use dial-up modems. Information security specialists focus on internet-based attacks due to the considerably higher risk they pose to organizations, but even some of the simplest of technologies can be vulnerable to attack. This, In turn, can lead to an attacker gaining unauthorized access, and ultimately cause a breach of a client’s network. It is critical for clients that wish to understand where their controls are failing and where they can mature their security posture, but it is especially critical for those still using dial-up connections.






