Corporate technology and security executives no doubt spend many a sleepless night anticipating what hackers might do next to attempt to gain access to valuable company assets. Keeping company and valuable customer data safe is Job One, as breaches can cost millions in lost assets, not to mention the reputational damage a corporation can suffer when an attack happens. Clearly, hackers can own the minds and pockets of the corporate world.
In this blog, we set out to show how easily high privilege accounts can be accessed during an internal network test. We recognize a disconnect exists between what is secure and what is perceived as secure.
The process of initially gaining, then escalating privileges has been very similar for some time now. Taking advantage of the way Windows authenticates, an attacker is able to intercept credentials and through the use of tools, able to obtain a clear text username and password. Once an attacker has access to an internal network and a set of valid credentials, gaining information and other credentials from workstations is much easier.
In this blog, we assume the role of an attacker or malicious user and outline a well-used method to obtain privileged credentials and own the domain. The tools below take advantage of Windows specific vulnerabilities, so it is assumed a Windows environment is being used and the following conditions have been met:
- An IP address has been assigned
- The attacking host is on the same VLAN as other workstations
Essentially, the attack host has successfully connected to the target network, the network consists of mainly Windows machines, and the attack host can ping other workstations. These tools will work with most Linux distributions.
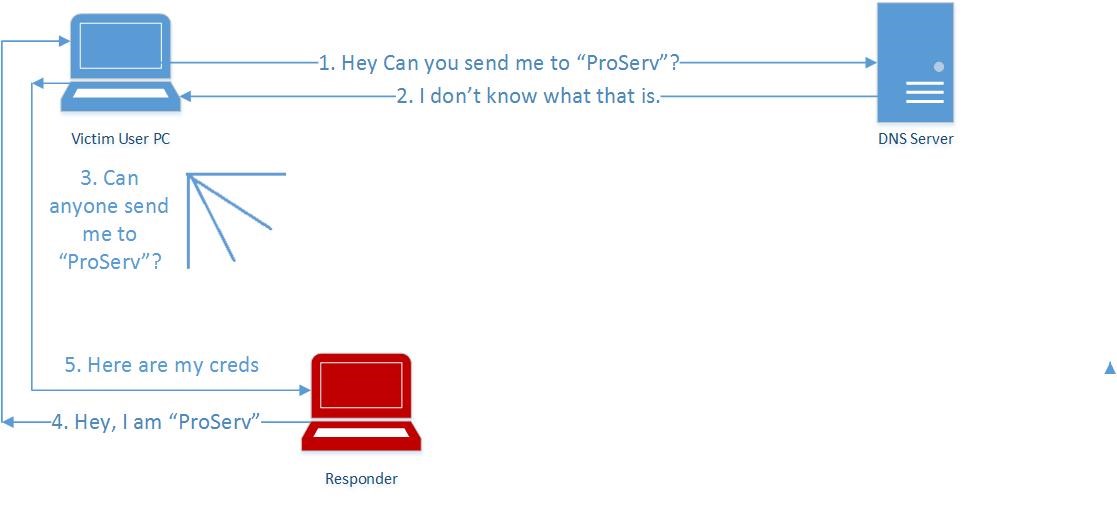
The first tool is Responder, developed by Spiderlabs. Responder sits on the attacker’s computer and listens for computers sending usernames and hashed passwords. It involves spoofing responses to questions that are asked during the “Windows authentication process.”
Responder and the MME Market
Windows will send hashed credentials to any service that claims to be the resource which has been requested, and it does not validate the requested service, which allows for this Man in the Middle (MiTM) attack. This happens thanks to the services Netbios Name Service (NBT-NS) and the successor Link-Local Multicast Name Resolution (LLMNR). These services broadcast requests when the DNS fails. Responder then listens for those broadcasts, and “responds,” hoping the computer will send their hashed credentials. With a non-malicious Windows request, the hashed credentials would be processed and the requestor would be given access to the resource. When Responder is used and a request is captured, the request is forwarded though to the appropriate resource, or the request is dropped.
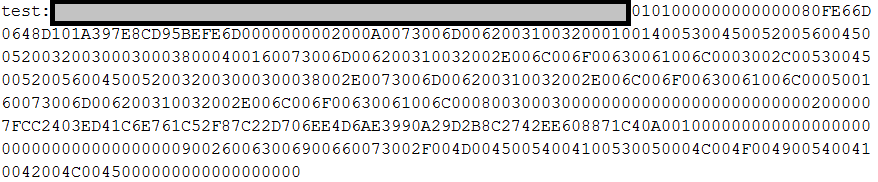
An example of an NTLMv2 hash captured by Responder
Furthermore, Responder can only successfully capture credentials when the DNS cannot identify the requested resource. This may happen more often than realized. For example, if a domain user misspells a requested resource such as a Server Message Block (SMB) share, HTTP, or HTTPS webpage, the DNS will be queried first before it performs the search. Because the resource is misspelled, the DNS will not be able to resolve the hostname, so will utilize NBT-NS or LLMNR and request the local machines to resolve the query. If this happens and Responder successfully impersonates the requested resource, the attacker will have a valid NetNTLM Hash, containing a plaintext Username, plaintext Domain, and a hashed password.
After Responder has captured a handful of hashes, the attacker can attempt to find the plaintext value of the hashed passwords, a process known as cracking. In this environment, the attacker has access to a tool called oclhashcat, which uses Graphical Processors (GPU) to guess hashed password values at very fast speeds. Once the hashed value is placed into the oclhashcat program, the plaintext value of the hash is guessed billions of times and if it is correctly guessed, the attacker now has a plaintext password. This step can pose a significant difficulty if the client’s password policy is complex, since password cracking gets exponentially more difficult the more length or entropy is added to the password.
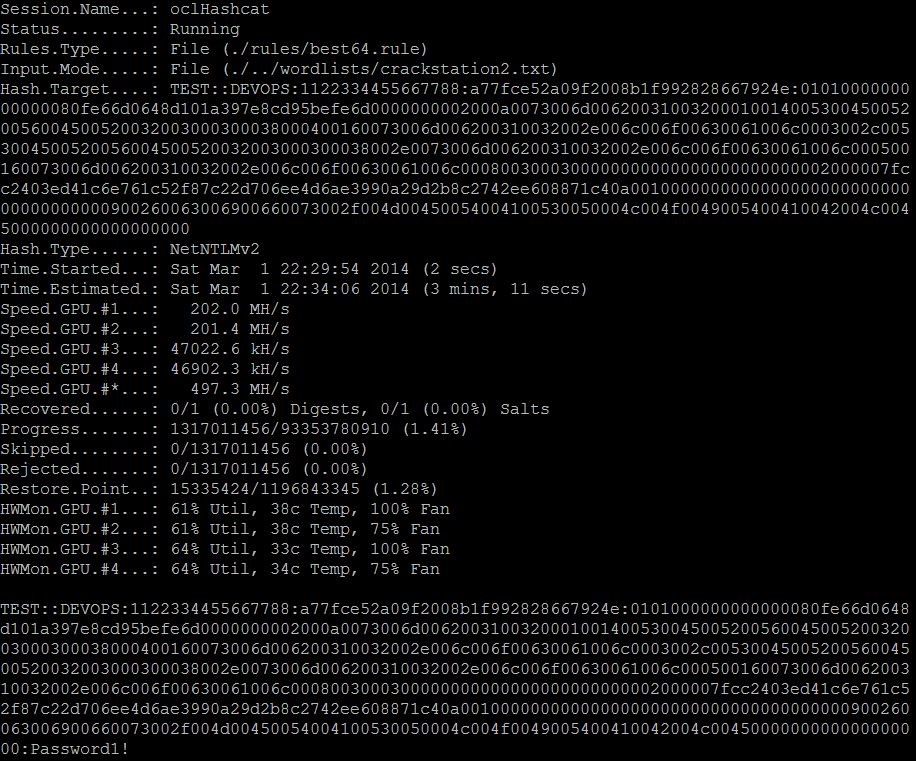
As you can see in the above image, the crack was successful and the attacker now has a plaintext password (Password1!), associated username, and user domain — all of the ingredients needed to remotely access a computer.
Here’s a what’s happened so far:
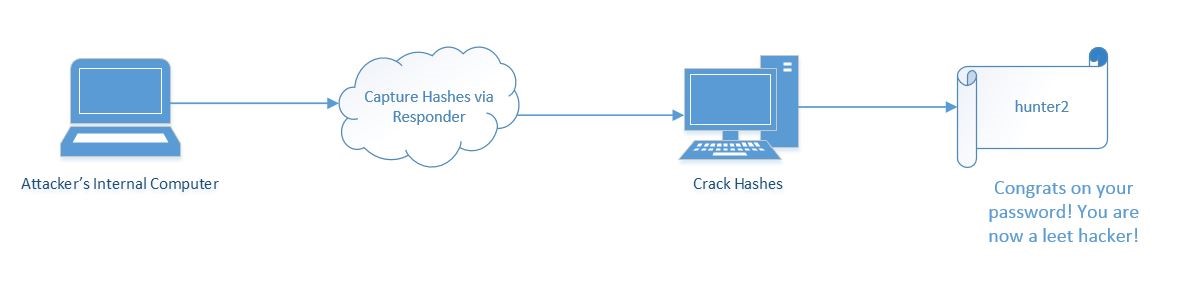
There are a large amount of Linux tools that an attacker can leverage to test the validity of the credentials, including winexe, rdesktop, SMBexec, and psexec. If the attacker wanted to check a range of hosts at one time, the tool SMBexec allows for a scan of a specified range for hosts with port 139 and 445 open, creating a target list. SMBexec will then allow the attacker to test the credentials against the found hosts.
Once the attacker has established they can authenticate via SMB, they can then login to the hosts, using the psexec_psh module in the metasploit framework “exploit/windows/smb/psexec_psh.” The psexec_psh module uses powershell to trigger a payload on the victim machine. Additionally, the payload does not touch the hard disk on the target host. Using the default “psexec_psh” settings, the tool will use a Meterpreter payload on the remote computer. Meterpreter is a ruby-based shell that runs entirely in-memory, making information gathering incredibly easy.
After successfully authenticating and gaining access via Meterpreter shell, the attacker will try to access what is available within the current environment, gather information, and then attempt to escalate privileges.
To do that, the attacker can use various discovery commands such as “getuid” to discover current permissions. If the permissions are correct, the attacker can also leverage the Windows NET /domain commands. These commands allow a user with sufficient privileges to query the domain controller for various information about the domain. Armed with NET command, the attacker can discover the hostnames of the Domain Controllers, enumerate various groups in the active directory environment, or discover what groups a specific user belongs to within an environment.
There are many tools that can be used by the attacker to gather additional sensitive information within the environment. For example, within meterpreter, there is an entire group of “post exploitation” modules that can be used to pull hashes, or further enumerate the target, such as a tool called Mimikatz. Mimikatz is a tool developed by Benjamin Delpy at gentilkiwi that allows a user with the appropriate privileges to dump plaintext passwords from memory,and takes advantage of an interaction between the LsaSS DLL and various authentication packages that require the plaintext password in memory, making it a very useful tool in the attacker’s arsenal.
After authenticating and dropping the payload, the attacker can load Mimikatz by using the command “load mimikatz”. If the attacker needs a guide they can type “help mimikatz” and the available commands will show on screen. After Mimikatz is successfully loaded, the attacker provides the name of the authentication package they would like to test against, usually “kerberos” or “wdigest.” If successful, the tool will return plaintext passwords. This tool pulls passwords of all of the sessions that are currently running on the computer. If the target computer has multiple users logged in, then every user’s credentials will be pulled via Mimikatz.
Now where does the attacker go?
With a new set of credentials, the attacker will continue to pivot. The more hosts that are discovered, the more credentials that can be captured. The more credentials captured, the greater the possibility they can find a host with an elevated privileged user, such as an Administrator (SMBexec can find hosts with administrator processes). Once that user account is identified, the attacker can use the tools mentioned above to login and dump the plaintext passwords or hashes, giving them an administrator account’s credentials. Access to a working user in the Domain Admin group effectively allows access to every workstation, as well as creating, modifying, or deleting any user within the associated domain tree. This attack works on most wWindows-based environments, because this vulnerability is part of normal operations within a Windows domain.
5 Remediation Tips
Remediation can be a complex process, but there are many ways this type of attack can be made more difficult. Here are 5 steps you can take now:
- Implementing a password policy that encourages length and complexity. The longer and more complex a password is, the ability to guess the password becomes exponentially harder.
- Disabling LLMNR and NBT-NS if possible. If each of these components is locked down to the minimum needed utilization within an environment, this will minimize the amount of hashes traveling across the internal network.
- Segregating Sensitive hosts from the main user network will make traversing the network harder by lowering the attack surface of sensitive machines.
- Setting the appropriate permissions for users. Regular users should not be local administrators on their computers; if the users access is minimized, the attacker’s compromised credentials will also be minimized.
- Implementing a much stronger authentication mechanism such as Kerberos is best practice. If implementation of Kerberos is not feasible, attempt to selectively implement it on sensitive hosts.
The vulnerabilities inherent in Microsoft systems seem to be here to stay, at least for a while. Attackers need not be highly sophisticated, as the steps they will take are not the most technical and the tools are readily available. The attack surface for any Windows environment is as big as your user base, and all it takes is one easy-to-crack hashed password. Although this paints a grim picture for security, there are solutions to minimize the access and availability of information on the internal network. Bottom line: make the time now to minimize the types of simple attacks we’ve described here, or risk reputational, regulatory, and operational consequences.






